Understanding Cyber Risk: The Importance of Integrated ITAM
The State of Cyber Risk 2025: Business Context Needed
The cyber risk landscape is evolving, pressing organizations to adopt formal cyber risk programs. Despite increased investments and frameworks, many organizations continue to struggle with immature risk management practices. Qualys, in partnership with Dark Reading, conducted research with over 100 IT and cybersecurity leaders, revealing that most organizations view cyber risk primarily as a technical challenge rather than a business issue.
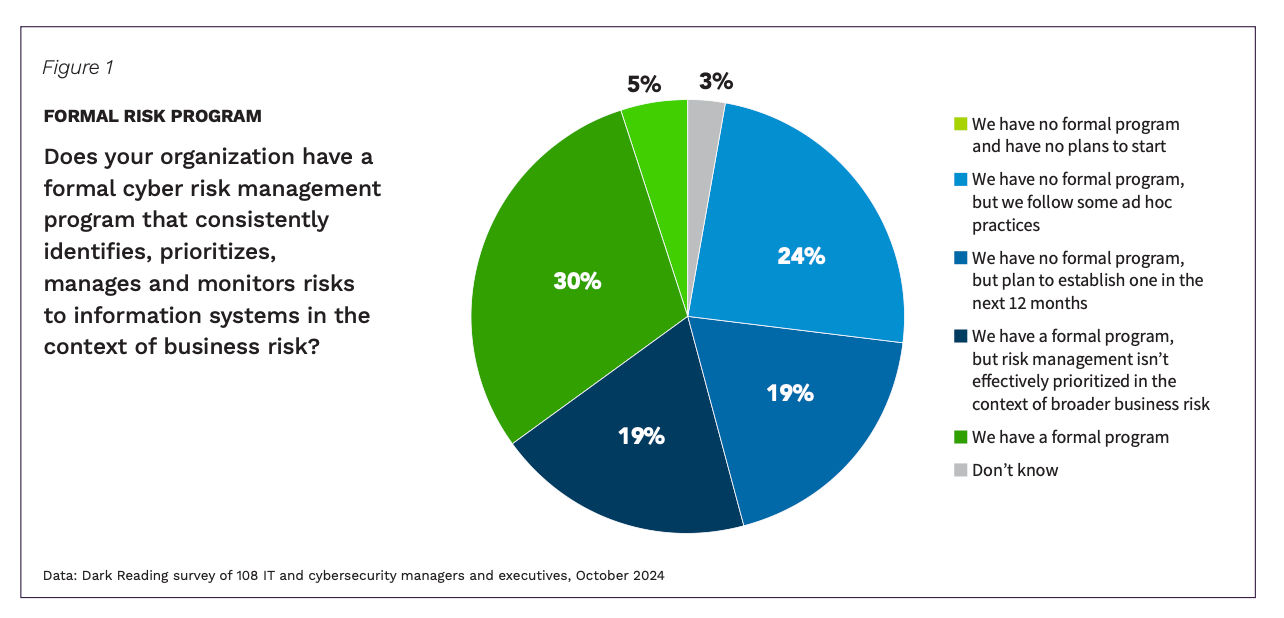
Image courtesy of Qualys
Formal Risk Programs Are Expanding, but Business Context is Still Missing
Approximately 49% of organizations report having a formal cyber risk program. However, only 30% prioritize these programs based on business objectives. The data indicates that many risk management strategies focus on compliance rather than embedding essential business context, such as potential financial losses and protecting critical assets.
More Investment ≠ Less Risk: Why the Cyber ROI Isn’t Adding Up
Despite rising cybersecurity spending, 71% of organizations perceive their cyber risk levels as stagnant or increasing. This disconnect often arises from a lack of unified visibility and prioritization strategies. Security tools function in silos, and remediation workflows often lack guidance from business context.
The Missing Metric: Business Relevance in Asset Intelligence
Visibility remains a significant challenge in cyber risk management. While 83% of organizations perform regular asset inventories, only 13% can do so continuously. This gap leads to incomplete asset inventories, which hinder effective risk management. Organizations need to understand the business role of their assets to manage risk effectively.

Image courtesy of Qualys
Risk Prioritization Needs to be a Business Conversation, Not a Technical One
Many organizations continue to rely on single scoring methods like CVSS for prioritizing vulnerabilities. This approach can overlook the nuances of business operations. Only 18% of organizations update asset risk profiles monthly, emphasizing the need for more integrated, contextual scoring that reflects exploitability and asset importance.

Image courtesy of Qualys
Reporting Risk in Business Terms, Not Security Jargon
While 90% of organizations report cyber risk findings to their boards, only 18% use integrated risk scenarios, and merely 14% tie these reports to financial quantification. This indicates a significant gap in translating operational data into actionable business insights.
Recharting Risk Operations with Business Impact as the North Star
Organizations are shifting towards a Risk Operations Center (ROC) model, which provides a continuous correlation of vulnerability data, asset context, and threat exposure. This model focuses on business risk reduction rather than reactive measures and emphasizes the need for a unified approach to risk management.
Learn more about Qualys Enterprise TruRisk Management and the Qualys Risk Operations Center.
Integrated ITAM: The Missing Layer of Cybersecurity
Integrated IT asset management (ITAM) is essential for enhancing cybersecurity strategies. By providing a centralized view of IT assets, an integrated ITAM solution can mitigate risks while ensuring compliance and audit readiness.

Image courtesy of Setyl
What is an Integrated ITAM Solution?
An integrated ITAM solution connects various tools used across an organization, enabling a comprehensive overview of IT assets. This centralized system allows for better visibility and management of risks.
Learn more about Setyl's ITAM platform and how it integrates with other tools.
The Role of Integrated ITAM in Cybersecurity
An effective ITAM solution aids in gaining visibility over assets, controlling the IT landscape, and responding promptly to security incidents. It also plays a crucial role in compliance management and audit preparedness.
Gain Visibility Over What You’re Trying to Secure
Lack of visibility is a significant barrier for organizations aiming to align IT asset management with security. An integrated ITAM solution enhances visibility by consolidating data from various sources, providing a complete view of assets.
Learn more about MDM and RMM integrations and accounting integrations for better asset management.
Take Control of Your IT Landscape and Mitigate Risks
A comprehensive view of the IT infrastructure allows organizations to focus on risk reduction. Integrated ITAM can alert teams to missing information regarding assets and licenses, helping to reduce security incidents.
Learn about the importance of accounting integration and HR integration.
Respond Quickly to Security Incidents
Real-time visibility into affected assets is crucial for quick incident response. Integrated ITAM solutions provide accurate knowledge of configuration parameters, facilitating effective containment and remediation.
Learn about the benefits of physical asset labels for asset recovery.
Meet Compliance and Audit Requirements
Integrated ITAM solutions help maintain a comprehensive information asset register, which is essential for compliance with various audits. Features such as lifecycle audit logs and vendor due diligence questionnaires contribute to compliance management.
Learn more about compliance features in ITAM solutions.
Scale with Confidence
A robust ITAM solution supports organizational growth while enabling quick responses to market changes. It provides clarity on IT spending, allowing for informed decisions during scaling or cost-cutting.
Discover how Setyl's platform provides clarity of spend on assets.
The Hidden Human Layer: Why Most Security Programs Miss the Real Risk
Traditional security measures often overlook the human element, which is a significant factor in insider threats. Security programs typically focus on protecting perimeters and endpoints, but the real risk often comes from within.
Where Traditional Approaches Fall Short
Legacy insider threat and DLP programs face common pitfalls, including excessive noise and false positives, leading to alert fatigue among security teams. Additionally, many monitoring solutions fail to provide context for user actions.
The Shift: Human-Centric Security at Scale
To address insider risk, organizations need to adopt a human-centric approach that focuses on understanding behavior rather than merely collecting data. This shift allows security teams to identify trends and potential risks more effectively.
Doing It Differently And Better
Leading organizations are shifting towards behavioral intelligence solutions that balance effectiveness with employee trust. Key differentiators include scalability, noise reduction through context, and forward-looking intelligence to identify shifts in behavior before incidents occur.
The Bigger Picture
Insider risk management must prioritize the workforce as partners in security, fostering visibility that empowers rather than stifles. Tools need to be developed that can scale with modern enterprises while maintaining trust among employees.
Learn more about how organizations can manage insider risk and the importance of context in security operations.

