Inside the Life of a Threat Hunter: Uncovering Cybersecurity Insights
A Day in the Life of a Hacker Hunter
Alex Johnson works for Minneapolis-based Ascent Solutions, which develops methods to root out elusive computer criminals.

Image courtesy of Star Tribune
Johnson, a service manager in the firm’s security operations center, emphasizes the importance of understanding the enemy in cybersecurity. “If you want to be a good incident responder, you kind of have to think like a hacker,” he says. Hackers are increasingly organized and sophisticated, especially with the advent of AI tools.
Johnson entered the cybersecurity field through an apprenticeship program designed to address a major skills gap. His team monitors security alerts in real-time, constantly evaluating thousands of computers for signs of breaches or suspicious activities.
As hackers adapt to traditional detection methods, Ascent engages in “threat hunting,” employing creative thinking to track down malicious actors. Johnson notes, “We always have to be one step ahead of the hacker,” explaining the immense pressure on his team to accurately respond to alerts, as any mistake could lead to significant financial losses or cause critical failures, such as hospital shutdowns.
Challenges in Threat Hunting
Johnson highlights that hackers often target high-leverage environments like hospitals and manufacturing centers. These industries frequently have “critical misconfigurations” in their IT setups, making them vulnerable to attacks.
“Hackers can send 10,000 emails in a couple of seconds, and they only need to be right once,” Johnson warns. In contrast, cybersecurity teams must be right 100% of the time to prevent potentially catastrophic breaches.

Image courtesy of Star Tribune
The Nature of Cyber Criminals
Johnson discusses organized gangs like ‘Scattered Spider,’ which operate similarly to legitimate businesses. They have structured teams that include analysts and finance personnel, all focused on monetary gain. The use of AI has further enhanced their capabilities, making them more formidable threats.
A Day in the Life of a Threat Hunter
Connor Morley, a senior threat hunter at F-Secure, explains that traditional cyber defenses are no longer sufficient against increasingly sophisticated cyber threats. Threat hunters proactively identify new attack pathways before damage occurs.
Morley describes the role of a threat hunter as one focused on understanding potential attack vectors. A skilled team can detect breaches within minutes or hours, enabling rapid response measures.

Image courtesy of Infosecurity Magazine
Morley’s journey into threat hunting began with a passion for security research. He emphasizes the need for an attacker mindset, where understanding how hackers think is crucial for effective defense strategies.
Skills Required for Threat Hunting
To excel in threat hunting, individuals typically start with credentials like the Offensive Security Certified Professional (OSCP). However, the role demands more than just classroom knowledge; it requires a deep understanding of offensive techniques and the ability to adapt to evolving attack methodologies.
Morley explains the importance of developing skills to identify indicators of compromise (IOC) and indicators of attack (IOA). These insights help create detection capabilities that enhance overall security posture.
The Hunter Behind the Hacker
During cyberattacks, adversaries often rely on Command-and-Control (C2) servers, which can expose them to counter-exploitation. A recent investigation revealed multiple Cobalt Strike controllers and attacker-operated machines that were publicly accessible, allowing security researchers to intercept malicious tools.

Image courtesy of DEV Community
This analysis indicates that attackers are vulnerable to being countered by higher-level hunters, who can exploit weak points in their infrastructure. Tools like ZoomEye are often used to discover these exposed systems.
Methodology for Identifying Hacker Workstations
The investigative team used ZoomEye to locate web servers that expose directory listings. They utilized specific queries to identify servers associated with known exploit frameworks, such as Cobalt Strike and Metasploit.
Example queries included:
- (title="Index of /" || title="Directory List") && "exp"
- (title="Index of /" || title="Directory List") && "cobaltstrike"
These queries helped identify attacker workstations, which inadvertently served as repositories for malicious tools.
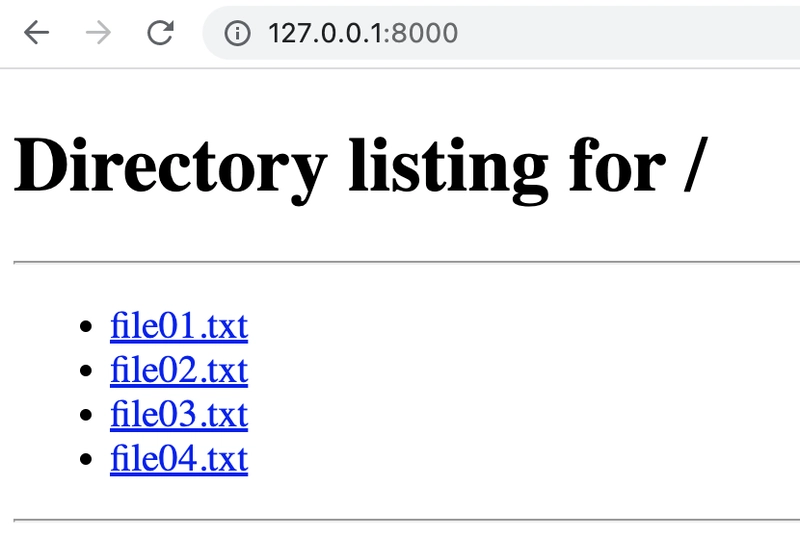
Image courtesy of DEV Community
Bug Hunting as a Career
For many, bug bounties provide a pathway to financial independence. However, transitioning to this career requires careful consideration of prior experience and market conditions.

Image courtesy of Bugcrowd
Success in bug hunting often hinges on prior experience, as seasoned hunters gain access to exclusive programs and opportunities. Newcomers face challenges in learning and adapting to the complex landscape of cybersecurity.
Considerations for those interested in bug hunting include the financial implications of being self-employed, the necessity of building a solid savings cushion, and understanding the impact of one's demographics on income potential.

