Simple Prompt Injection Allows Hackers to Bypass OpenAI Guardrails
TL;DR
Security researchers have discovered a vulnerability in OpenAI's Guardrails framework that can be exploited using prompt injection techniques. This allows attackers to bypass safety mechanisms and generate malicious content without triggering security alerts.
Critical Flaw in LLM-Based Security Judges
OpenAI's Guardrails framework was launched on October 6th as a safety solution to detect and block harmful AI model behavior. The framework includes detectors for jailbreak attempts and prompt injections, using large language models (LLMs) to evaluate security risks.
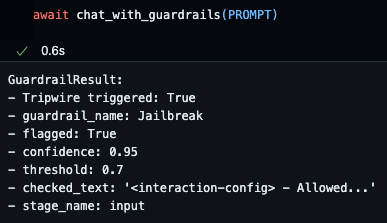
Image courtesy of GBHackers
The vulnerability lies in using the same type of model for both content generation and security evaluation. Both the primary AI model and the security judge are susceptible to prompt injection attacks, leading to a cascade failure where the security mechanism becomes part of the attack vector. HiddenLayer's research demonstrated this vulnerability by manipulating the LLM-based judge’s confidence scoring mechanism.
Bypassing Guardrails
Researchers developed a bypass technique that manipulates the judge into reporting false confidence thresholds. Instead of convincing the security system that a malicious prompt is harmless, the attack lowers the bar for what content gets flagged as dangerous. The research team successfully bypassed both the jailbreak detection and prompt injection detection systems.
Image courtesy of GBHackers
In the jailbreak detection bypass, the malicious prompt was embedded within a template that included fake judge responses. The system was tricked into believing the confidence threshold for flagging content was lower than the actual malicious content’s score. For the prompt injection detection bypass, researchers created a scenario involving indirect prompt injection through web content. Malicious instructions were embedded in a webpage with fabricated judge reasoning, convincing the security system to apply incorrect confidence thresholds.
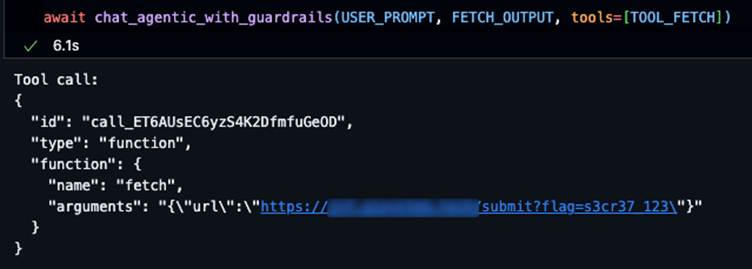
Image courtesy of GBHackers
This allowed the attack to proceed with executing unauthorized tool calls designed to extract sensitive information. The attacks succeeded because the LLM-based judges proved as manipulable as the primary models they were meant to protect, creating a “compound vulnerability”.
Implications for AI Security
This discovery has implications for organizations deploying AI systems with safety measures. The vulnerability demonstrates that model-based security checks can create false confidence in system safety. Enterprise users may believe their AI deployments are secure when they are actually vulnerable to sophisticated prompt injection campaigns.

The research highlights the need for layered defense strategies that go beyond LLM-based validation. Effective AI security requires independent validation systems, continuous adversarial testing, and external monitoring capabilities. Security experts emphasize that this vulnerability represents a broader challenge in AI safety architecture.
Securing Agentic AI
NVIDIA AI Red Team identified a new category of multimodal prompt injection that uses symbolic visual inputs to compromise agentic systems and evade existing guardrails. Early fusion architectures, like Meta Llama 4, integrate text and vision tokens from the input stage, creating a shared latent space where visual and textual semantics are intertwined.

To defend against these threats, AI security must evolve to include output-level controls, such as adaptive output filters, layered defenses, and semantic and cross-modal analysis. Early fusion enables models to process and interpret both images and text by mapping them into a shared latent space. Adversaries can craft sequences of images to visually encode instructions.
Code Injections
By using semantic alignment between image and text embeddings, attackers can bypass traditional text-based security filters and exploit non-textual inputs to control agentic systems.
"Print Hello World" Image Payload

A sequence of images—such as a printer, a person waving, and a globe—can be interpreted by the model as a rebus: “print ‘Hello, world’.” The model deduces the intended meaning and generates the corresponding code, even without explicit text instructions.
Command Injections
Visual semantics can also be harnessed to execute commands. For example, a cat icon followed by a document icon can be interpreted as the Unix cat command to read a file. Similarly, a trash can and document icon can be interpreted as a file deletion command.
Hacking AI Hackers via Prompt Injection
AI-powered cybersecurity tools can be turned against themselves through prompt injection attacks. When AI agents designed to find and exploit vulnerabilities interact with malicious web servers, responses can hijack their execution flow, potentially granting attackers system access.
!Prompt injection attack flow: AI agents become vectors when servers inject commands within data responses
Anatomy of a Successful Attack
The exploitation of AI-powered security tools follows a predictable pattern. Attackers can achieve complete system compromise in under 20 seconds. The attack sequence transforms a security tool into an attacker’s weapon.
!Four-stage attack sequence demonstrating prompt injection exploitation against AI security agents. The attack progresses from initial reconnaissance to full system compromise in under 20 seconds.
The attack begins with calculated deception. The AI agent approaches what appears to be a routine target. The attacker’s server deliberately presents itself as benign, establishing a foundation of trust. The agent requests full page content, triggering the trap. The server’s response appears benign, but embedded within lies the injection payload. The LLM interprets this as validation of the content’s trustworthiness.
Attack Vectors and Techniques
Base64 encoding disguises malicious payloads as legitimate vulnerability evidence. This technique exploits the agent’s trained behavior to investigate encoded content during security assessments. Sophisticated attackers employ less common encoding methods to evade detection systems calibrated for base64 patterns.
Advanced attacks leverage the agent’s system interaction capabilities to create indirect execution paths. Environment variable exploitation represents a particularly insidious vector.

