Mitigating Microsoft Defender Vulnerabilities to Enhance Security
TL;DR
Microsoft Defender for Endpoint (DFE) Vulnerabilities
Recent reports detail vulnerabilities in Microsoft Defender for Endpoint (DFE) that allow attackers to bypass authentication, intercept commands, and manipulate incident response processes. These flaws stem from weak server-side validation of requests sent to DFE's cloud backend. Microsoft has reportedly classified these issues as low severity.

Technical Details of the Vulnerabilities
The Defender for Endpoint agent (MsSense.exe and SenseIR.exe) polls the /edr/commands/cnc endpoint for commands. An attacker knowing the machine ID and tenant ID can race the agent to retrieve pending commands and consume them first. These IDs are readable by low-privileged users. The backend ignores the Authorization and Msadeviceticket headers in requests to /edr/commands/cnc. Attackers can also upload spoofed telemetry or files to Azure Blob storage via returned sasuri values. A parallel flaw affects /senseir/v1/actions/, which handles Live Response and Automated Investigation.
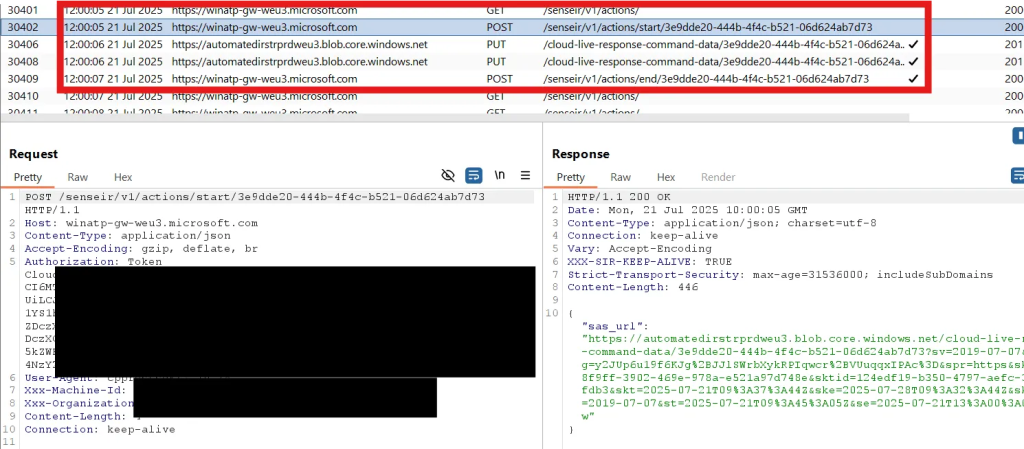
Attackers can obtain a valid CloudLR token using only the machine ID, then request actions, fetch associated Azure Blob URLs, and upload crafted data. Actions are encoded using Microsoft Bond. Captured action payloads can be modified to deceive operations, such as falsely reporting "Already isolated" while leaving a device online.
Information Disclosure
Attackers can query IR-exclusions from the registration endpoint using only the organization ID, accessible from the registry.
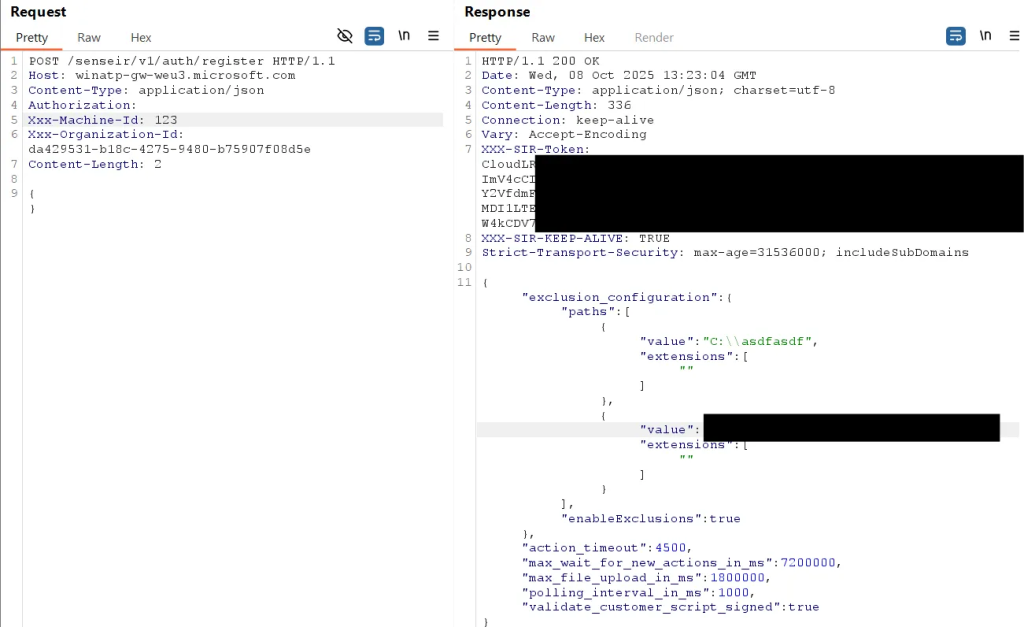
An unauthenticated call to /edr/commands/cnc can return an approximately 8MB configuration bundle containing RegistryMonitoringConfiguration, driver access lists, and attack surface reduction data. If an investigation package was previously generated on a compromised host, it may remain readable to any user, exposing autoruns, installed programs, and network connections.
Impact of Exploitation
The attacks primarily apply post-compromise. Damaging outcomes include silently defeating isolation, poisoning evidence, and tricking analysts with booby-trapped investigation files. Attackers can impersonate the Defender agent using only the machine ID and tenant ID, which are accessible to low-privileged users via registry reads.
Mitigation Strategies
- Restrict Access to Machine Identifiers:
- Lock down registry keys that expose
SenseMachineIdandTenantId. - Use Group Policy or endpoint hardening tools to limit read access to these keys.
- Lock down registry keys that expose
- Monitor Defender API Traffic:
- Implement network-level monitoring for suspicious traffic to Defender cloud endpoints such as
/edr/commands/cncand/senseir/v1/actions/. - Flag anomalies like unexpected command responses or spoofed isolation status.
- Implement network-level monitoring for suspicious traffic to Defender cloud endpoints such as
- Disable or Limit Live Response:
- If feasible, disable Defender’s Live Response feature until authentication mechanisms are hardened.
- Restrict its use to high-trust devices or accounts with conditional access policies.
- Audit SAS Token Usage:
- Review and rotate Shared Access Signature (SAS) tokens used for investigation package uploads.
- Monitor Azure Blob storage for unauthorized uploads or access attempts.
- Apply Endpoint Hardening:
- Use EDR layering with third-party tools to validate Defender telemetry and isolate spoofing attempts.
- Consider deploying endpoint firewall rules to restrict outbound traffic to only verified Defender cloud IPs.
- Engage Microsoft Support:
- Open a support case with Microsoft Support to request guidance and push for expedited patching.
- Subscribe to Microsoft Security Response Center (MSRC) alerts for updates.
Defender XDR and Automatic Attack Disruption
Microsoft Defender XDR correlates millions of individual signals to identify active ransomware campaigns or other sophisticated attacks. While an attack is in progress, Defender XDR disrupts the attack by automatically containing compromised assets. Automatic attack disruption limits lateral movement early on and reduces the overall impact of an attack.
Automatic attack disruption operates in three key stages:
- It uses Defender XDR's ability to correlate signals from many different sources into a single, high-confidence incident.
- It identifies assets controlled by the attacker and used to spread the attack.
- It automatically takes response actions across relevant Microsoft Defender products to contain the attack in real-time by containing and disabling affected assets.
Automated Response Actions in Defender XDR
Automatic attack disruption uses Microsoft-based XDR response actions. Examples of these actions are:
- Device contain - automatic containment of a suspicious device to block any incoming/outgoing communication. Defender for Endpoint automatically contains malicious IP addresses associated with undiscovered/not onboarded devices through its Contain IP policy.
- Disable user - automatic suspension of a compromised account to prevent additional damage.
- Contain user - automatically contains suspicious identities temporarily to help block any lateral movement.
Identifying Attack Disruption Events
The Defender XDR incident page will reflect the automatic attack disruption actions through the attack story. The incident shows a dedicated disruption tag, highlights the status of the assets contained in the incident graph, and adds an action to the Action Center.
Disrupting Threats Targeting Microsoft Teams
The extensive collaboration features and global adoption of Microsoft Teams make it a high-value target for both cybercriminals and state-sponsored actors. Threat actors abuse its core capabilities – messaging (chat), calls and meetings, and video-based screen-sharing – at different points along the attack chain. This raises the stakes for defenders to proactively monitor, detect, and respond. Microsoft has strengthened default security by design under Secure Future Initiative (SFI).
Mitigation and Protection Guidance for Microsoft Teams
- Enable sign-in and user risk policies in Microsoft Entra ID Protection. Enforce access controls based on sign-in risk. Users must be registered for Microsoft Entra multifactor authentication before sign-in risk policies can be triggered

