Comprehensive Cybersecurity: Offensive, Defensive, and Threat Intelligence
NopalCyber's Comprehensive Cybersecurity Solutions
NopalCyber offers a robust cybersecurity framework designed to provide both offensive and defensive measures. Their integrated approach includes advanced Managed Extended Detection and Response (MXDR) and Attack Surface Management (ASM) capabilities to protect organizations from diverse cyber threats.
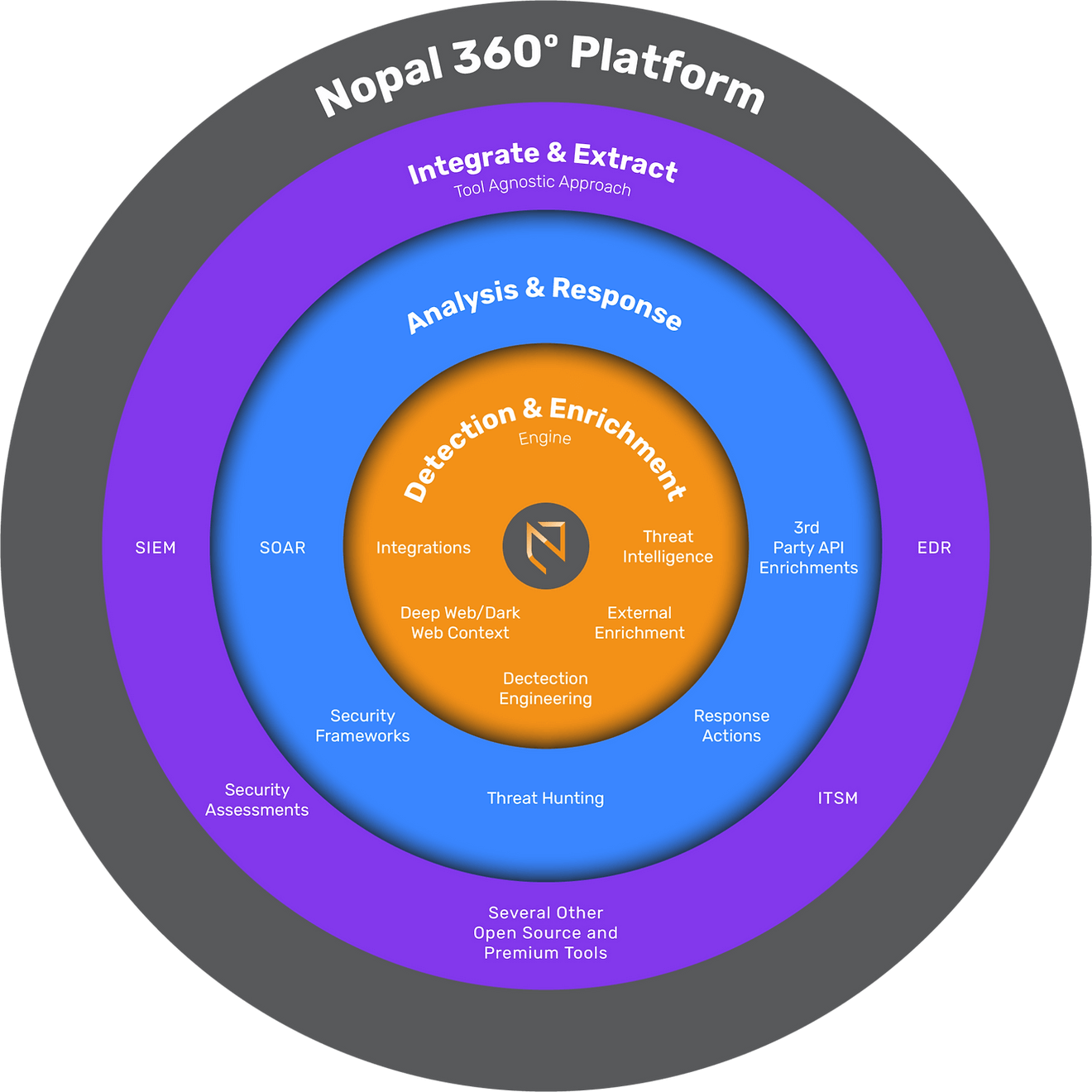
Image courtesy of NopalCyber
Security Coverage
NopalCyber emphasizes a 360° coverage strategy to combat today’s aggressive cyber attacks. Their services include:
- Vulnerability Assessment and Penetration Testing (VAPT): Identifying critical vulnerabilities and strengthening security posture.
- 24/7 Security Operations Center (SOC): Monitoring and responding to threats in real-time.
- Dynamic Cybersecurity Strategies: Tailored approaches that align with business objectives to enhance resilience against evolving threats.
For more details, visit NopalCyber Solutions.
Nopal360° MXDR Platform
The Nopal360° MXDR platform consolidates cybersecurity operations, integrating data from endpoints, networks, and security tools. Key features include:
- Ingestion of data from all sources to enhance threat detection.
- Integration of multiple security tools (MXDR, UEBA, EDR, etc.) for comprehensive coverage.
- Correlation and analysis of threat data to uncover hidden vulnerabilities.
This platform allows organizations to maximize their cybersecurity investments and improve overall security efficacy. Learn more at Nopal360°.
Image courtesy of NopalCyber
Cyber Intelligence Quotient (CIQ)
NopalCyber's CIQ metric quantifies cybersecurity posture, providing insights across various dimensions:
- Threat Detection & Response
- Cloud Security Posture
- Cyber Resiliency
- Vulnerability Management
The CIQ score allows organizations to visualize their security status and make informed decisions based on real-time data. More information can be found at Nopal CIQ.
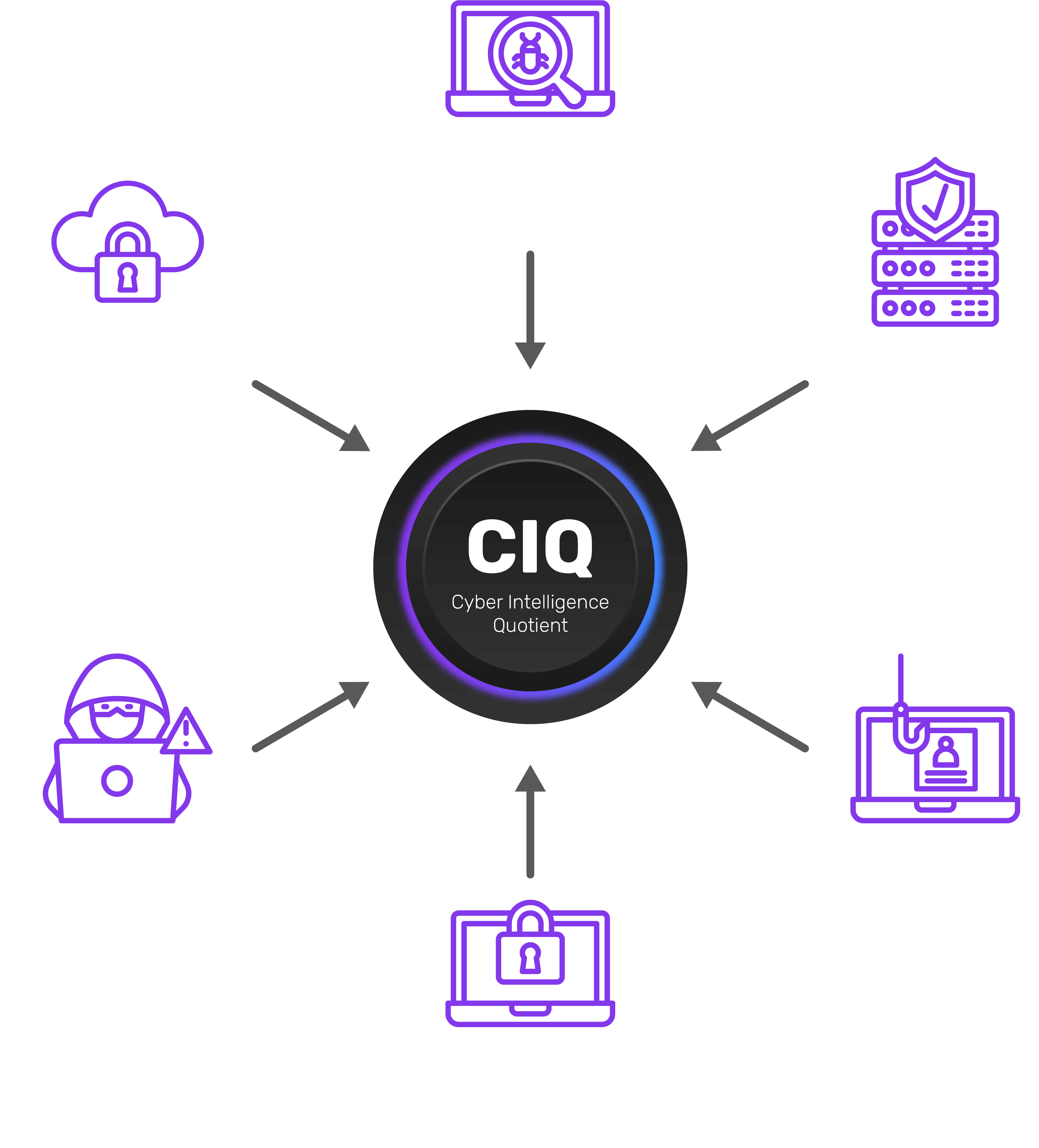
Image courtesy of NopalCyber
Client Testimonials
NopalCyber's expertise is reflected in client feedback. A CTO of a global SaaS platform stated, "NopalCyber has been pivotal in fortifying our security infrastructure with its comprehensive VAPT and application security services." Similarly, the CIO of a large hospital chain noted, "Their 24/7 SOCaaS and AppSec expertise have drastically improved our incident detection processes."
These testimonials highlight the effectiveness of NopalCyber's services in enhancing cybersecurity maturity across various sectors.
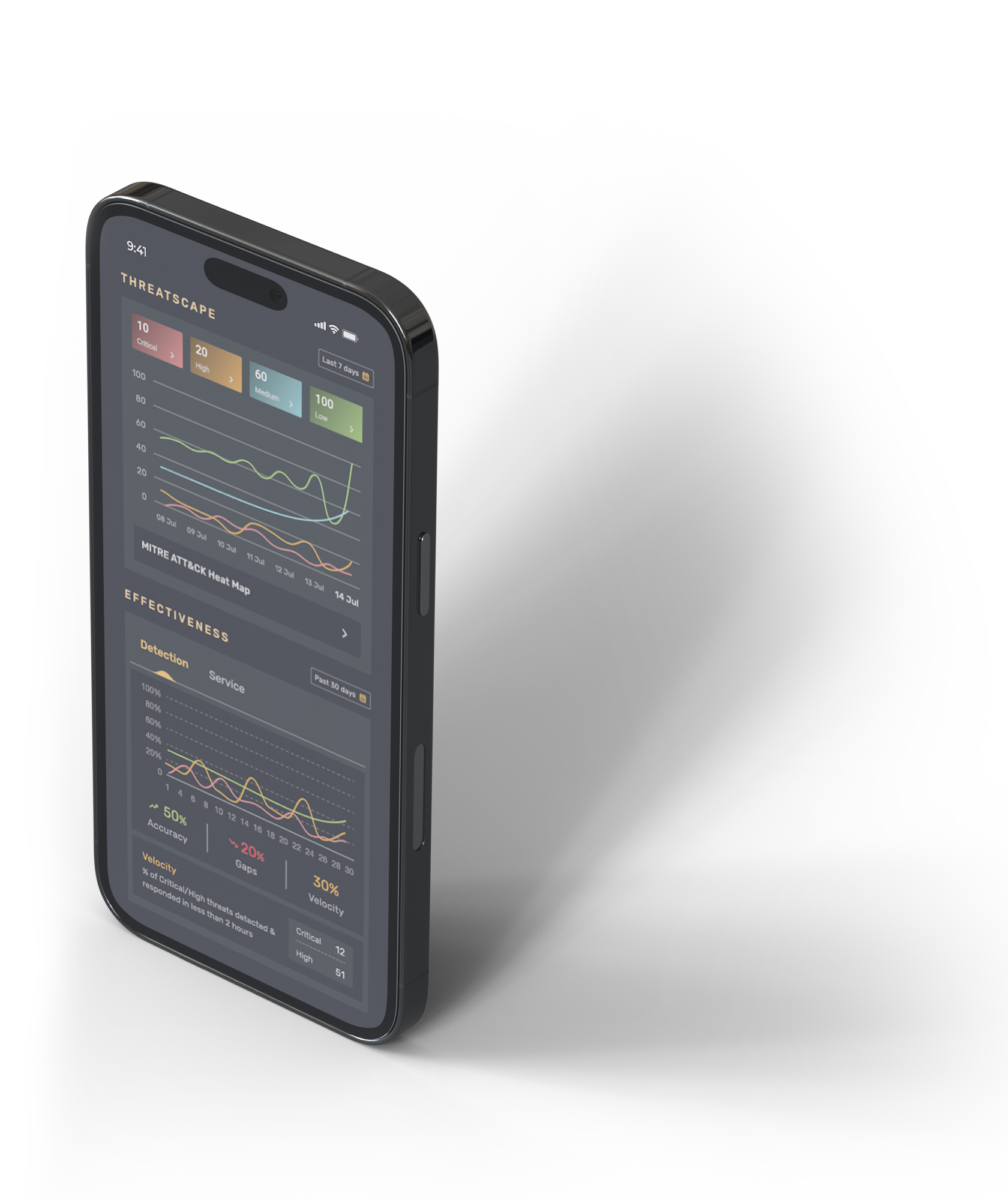
Image courtesy of NopalCyber
Threat Intelligence Overview
Threat intelligence is critical for organizations aiming to prevent and mitigate cyber threats. It provides actionable insights into potential threats, enabling security teams to adopt a proactive defense posture.
Key Characteristics
- Organization-specific: Tailored intelligence that focuses on the unique vulnerabilities of an organization.
- Detailed and contextual: Includes information about threat actors, their tactics, and indicators of compromise.
- Actionable: Provides insights for addressing vulnerabilities and prioritizing threats effectively.
For more on threat intelligence, visit IBM Cybersecurity.
The Threat Intelligence Lifecycle
The lifecycle includes six essential steps:
- Planning: Establishing intelligence requirements with stakeholders.
- Threat data collection: Gathering raw data from various sources.
- Processing: Standardizing and correlating data for easier analysis.
- Analysis: Extracting insights to meet intelligence requirements.
- Dissemination: Sharing findings with relevant stakeholders for action.
- Feedback: Reflecting on the process to inform future intelligence cycles.
This systematic approach enables organizations to enhance their security posture continually.
Types of Threat Intelligence
Organizations utilize different types of threat intelligence based on their specific needs:
- Tactical Threat Intelligence: Helps predict and detect ongoing attacks through common indicators of compromise.
- Operational Threat Intelligence: Provides a deeper understanding of threat actors’ behaviors and tactics.
- Strategic Threat Intelligence: Offers high-level insights into the global threat landscape and helps guide executive decision-making.
For a more detailed exploration of threat intelligence, refer to IBM Threat Intelligence.
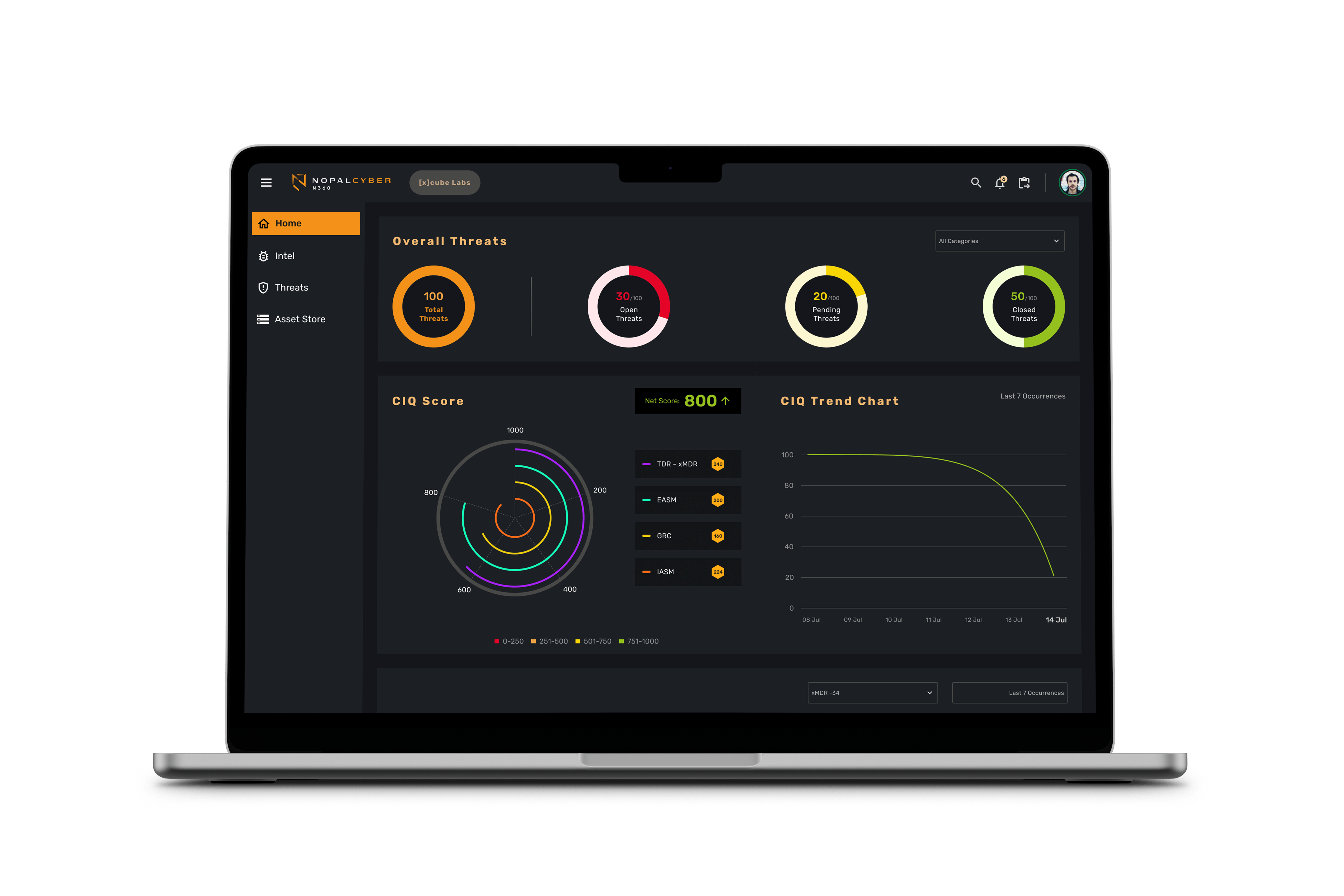
Image courtesy of NopalCyber

