Zimperium Reveals New Android Malware Evasion Techniques and Risks
Konfety Malware Overview
The new Konfety malware variant targets Android devices using advanced evasion techniques, complicating detection and analysis for security professionals. This malware employs an "evil-twin" tactic to conduct fraudulent activities by mimicking legitimate applications.
Key features of this variant include:
- Dual-App Deception: Both the benign and malicious versions share the same package name, enhancing the malware's evasiveness.
- ZIP-Level Evasion: The APK structure is tampered with, including unsupported compression and fake encryption flags, complicating reverse engineering.
- Dynamic Code Loading: Key functionalities are concealed in encrypted assets, only decrypted at runtime.
- Stealth Techniques: This includes hiding the app icon, mimicking legitimate apps, and using geofencing to adjust behavior based on the user's location.
- Ad Fraud Infrastructure: Utilizes the CaramelAds SDK for ad fetching and maintaining communication with attacker-controlled servers.
The sophistication of the Konfety malware is evident in its constant adaptation to evade detection.
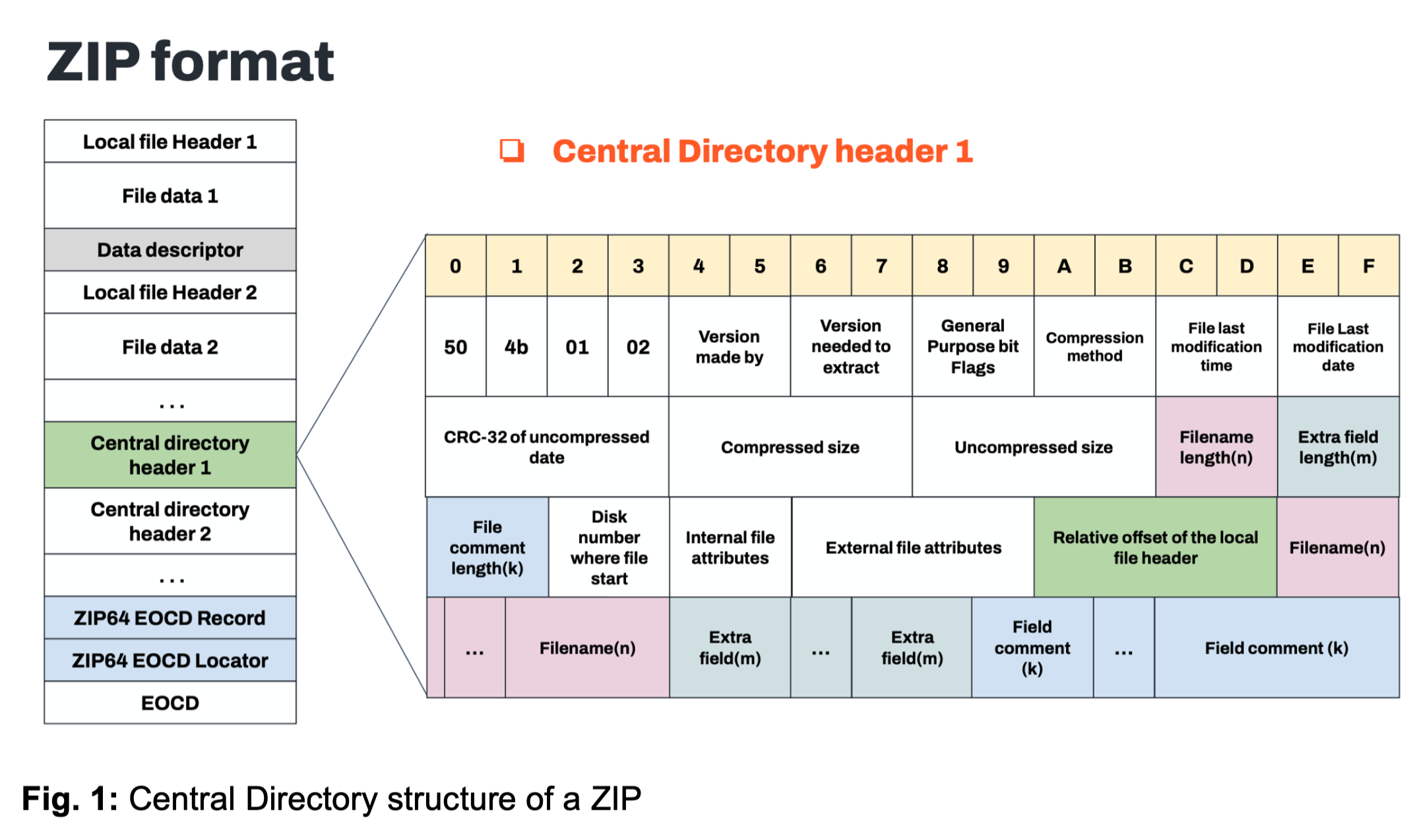
Image courtesy of Zimperium
Evasion via Malformed ZIP Packaging
Recent variants of Konfety employ advanced techniques to avoid detection, including:
- General Purpose Flag Enabled: This causes analysis tools to mistakenly identify the APK as encrypted, requiring a password for decompression.
- Unsupported Compression Method (BZIP - 0x000C): The AndroidManifest.xml falsely declares the use of BZIP compression, leading to analysis tool failures.
These manipulations can prevent tools like APKTool and JADX from executing properly, further complicating the detection of the malware.
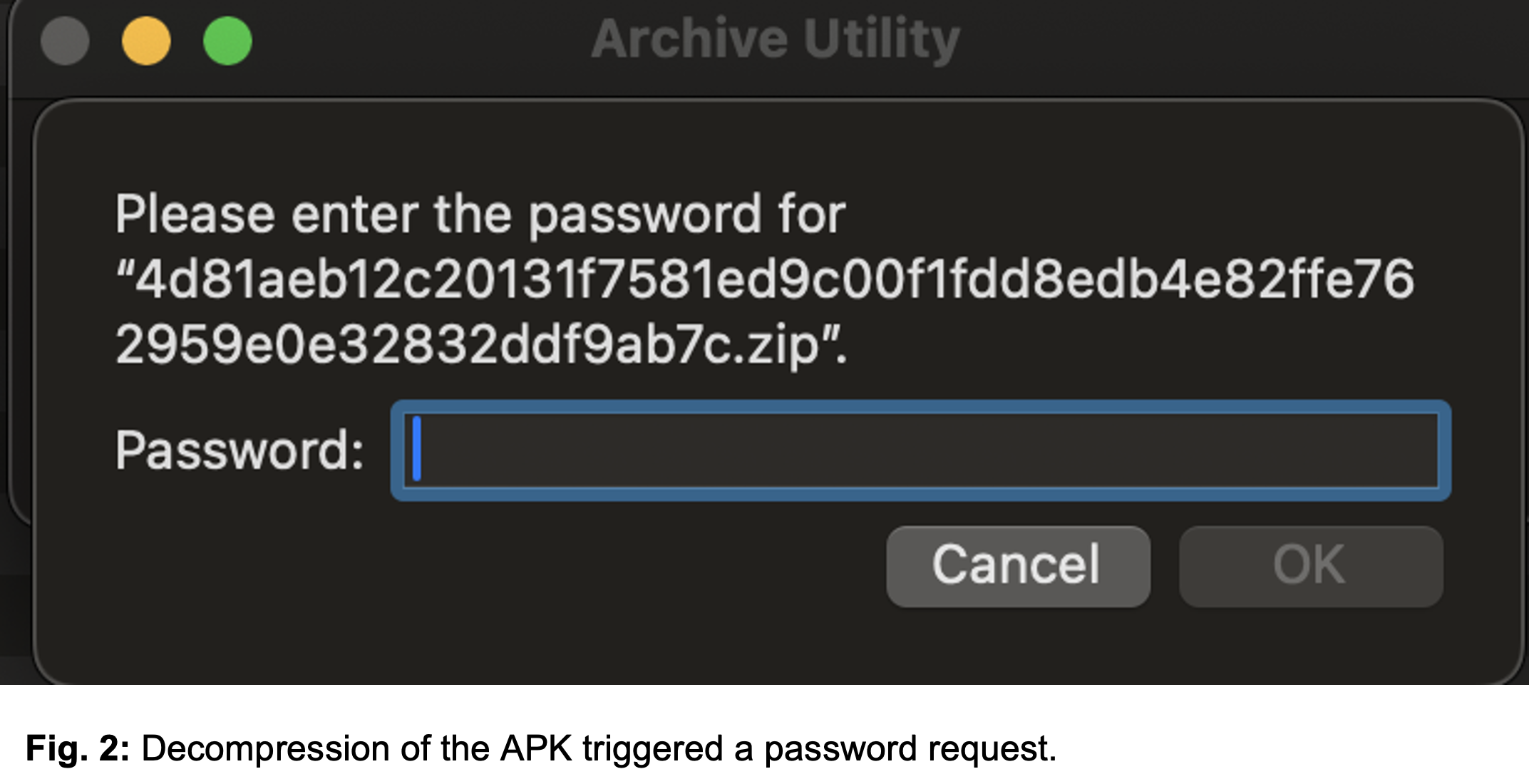
Image courtesy of Zimperium
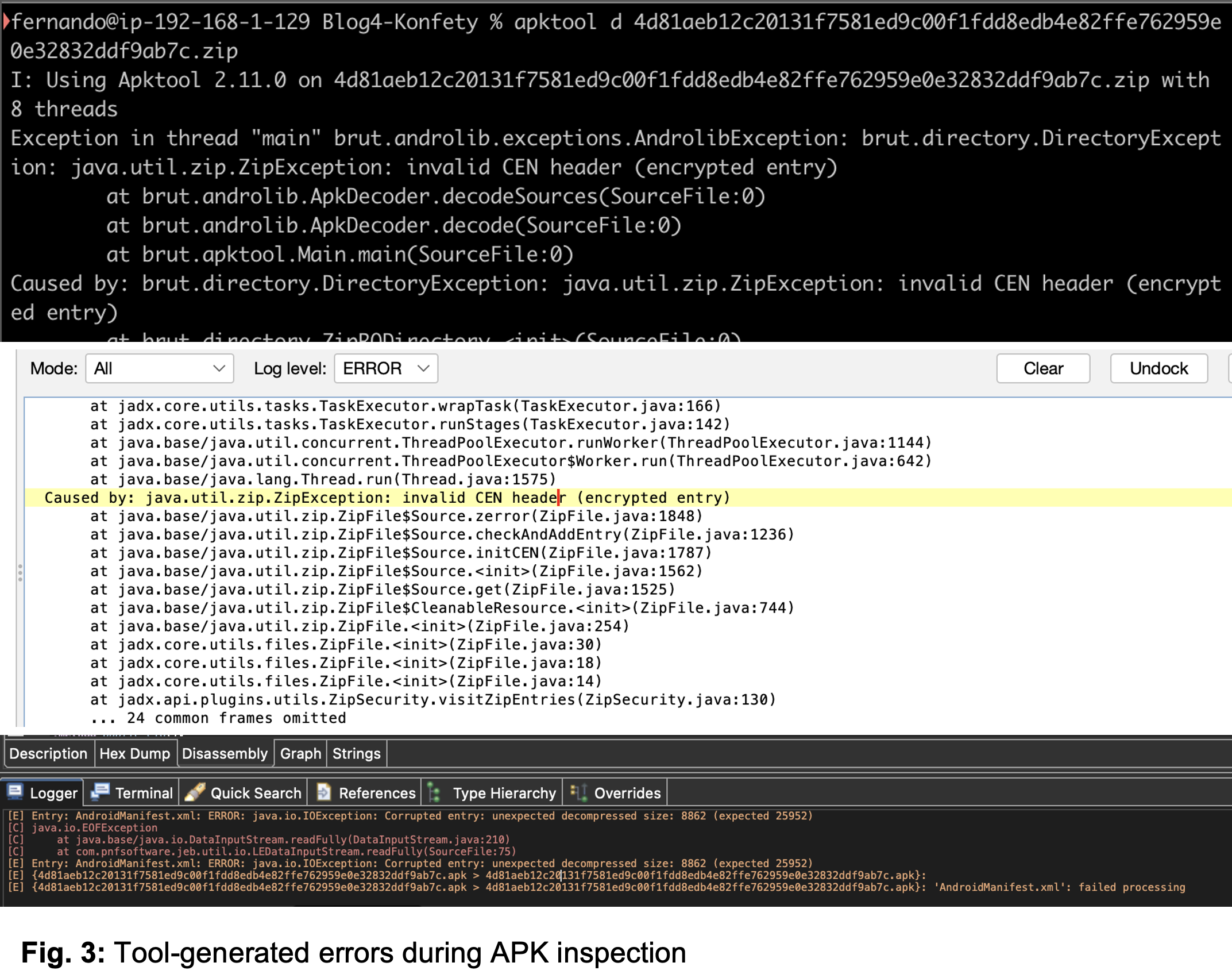
Image courtesy of Zimperium
The Konfety Malware Analysis
Konfety incorporates multiple layers of obfuscation to hinder detection efforts:
- Dynamic Code Loading: It loads additional executable code at runtime from encrypted assets, making it difficult to detect critical functionalities during scans.
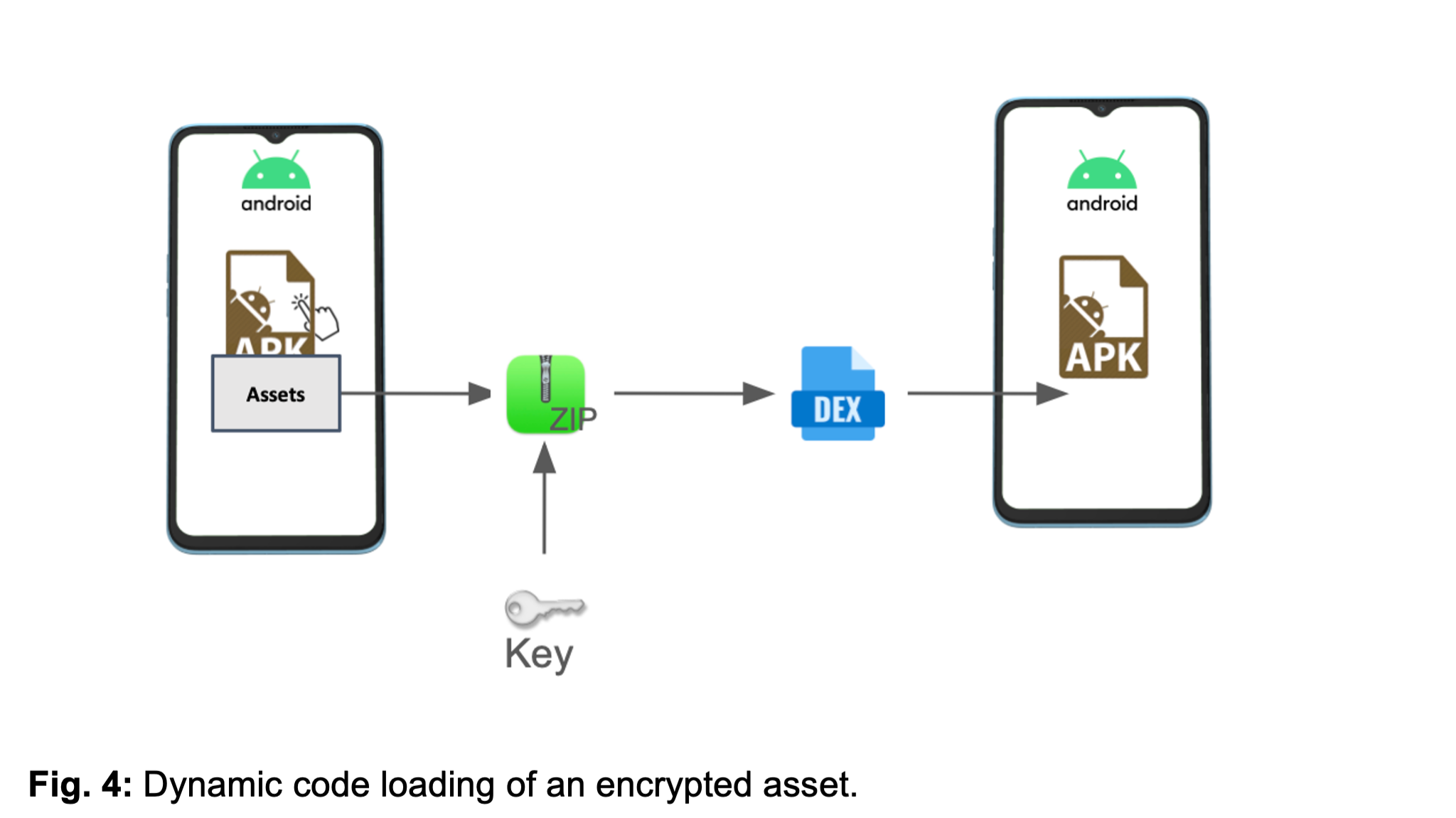
Image courtesy of Zimperium
- Decoy Applications: The malware mimics legitimate apps with the same package name, emphasizing its stealthy intent.
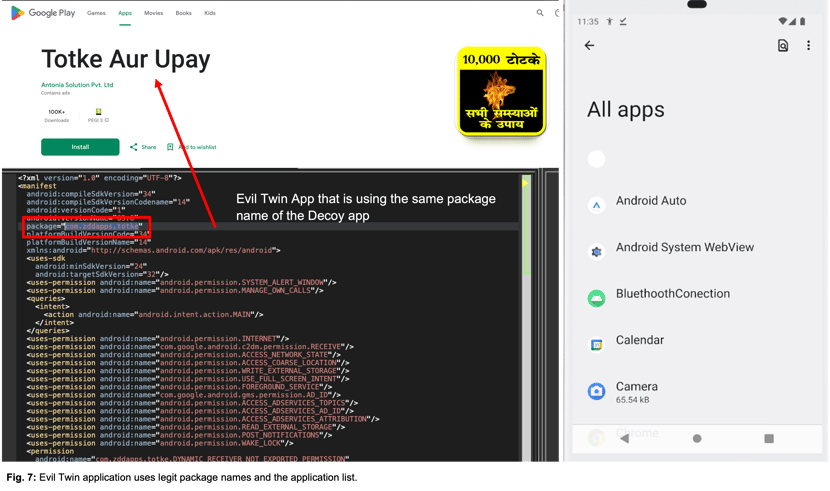
Image courtesy of Zimperium
Network Traffic Analysis
Through dynamic analysis, it was observed that the malware establishes a browser connection to malicious websites after the user accepts a User Agreement. This leads to a series of redirects designed to trick users into installing additional malicious applications or subscribing to unwanted notifications.
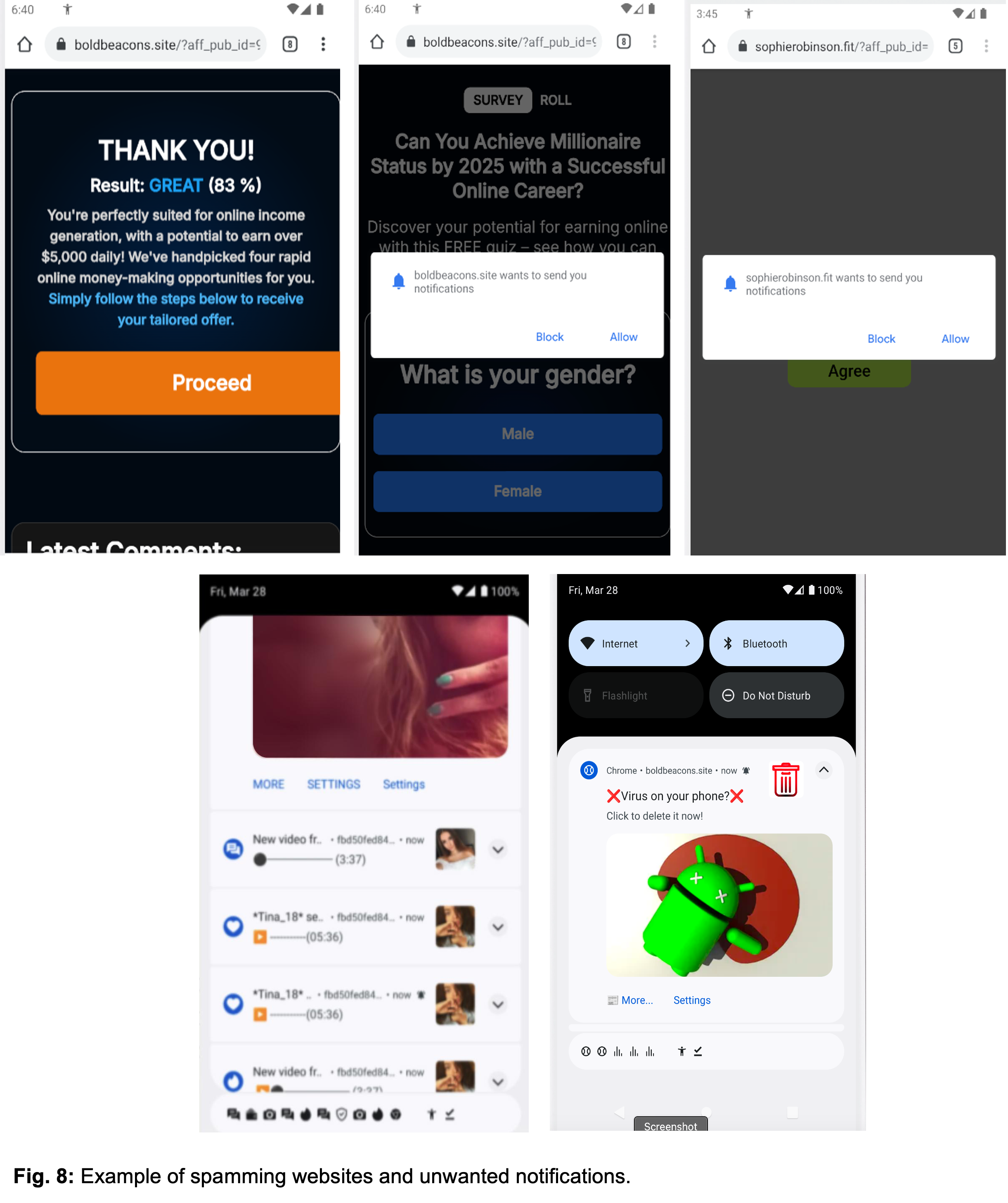
Image courtesy of Zimperium
Zimperium Protection Against Konfety
Zimperium's on-device Mobile Threat Defense (MTD) solution provides comprehensive protection against Konfety malware. The platform continuously adapts to evolving threat landscapes, ensuring that users remain secure from sophisticated malware such as Konfety.
For further information on how Zimperium can safeguard your mobile environment, visit Zimperium.
Unsupported Compression Methods
Zimperium researchers identified that 3,300 Android malware samples use unsupported compression methods to bypass detection. This technique limits analysis capabilities and is particularly effective against tools like JADX and APKTool.
Image courtesy of Zimperium
Zimperium's Detection Capabilities
Zimperium maintains dynamic on-device threat detection engines that protect against malicious apps installed using unsupported compression methods.
Zimperium MTD's enhanced phishing detection can also prevent phishing attacks, offering robust protection against the full attack chain.
Explore how our solutions can secure your devices and protect your business from evolving mobile threats. For more information, visit Zimperium.

