SVG Phishing Attacks: Evasive Techniques and CAPTCHA Exploits
Weaponization of SVG Images in Phishing Attacks
Threat actors are increasingly using Scalable Vector Graphics (SVG) to deliver malicious payloads in phishing attacks. These campaigns leverage the seemingly harmless nature of SVG files, embedding obfuscated JavaScript that redirects victims to malicious websites. According to a report by CSO Online, this shift in tactics has proven effective as many organizations underestimate the risks associated with these image formats.

Image courtesy of CSO Online
John Bambenek of Bambenek Consulting noted, "This is a fresh spin on the technique of using image files for delivering suspect content." The attackers utilize social engineering tactics with themes like 'ToDoList' and 'Missed Call' to lure victims into opening these SVG files.
The threat is compounded by security misconfigurations such as missing DomainKeys Identified Mail (DKIM) and relaxed Domain-based Message Authentication, Reporting & Conformance (DMARC) policies, which allow these attacks to bypass traditional defenses. Recommendations include enforcing SPF, DKIM, and DMARC to block spoofed emails and sanitizing SVG attachments.
For further reading, refer to the following sources: CSO Online, Ontinue Research, and Sophos Analysis.
Evolution of SVG Phishing Attacks
The recent surge in SVG phishing attacks has led to more sophisticated techniques, as detailed by Sophos researcher Andrew Brandt. These attacks now incorporate automated JavaScript, CAPTCHA for evasion, and even malware delivery. Attackers impersonate trusted services such as Microsoft SharePoint and Google Voice to maximize the effectiveness of their campaigns.
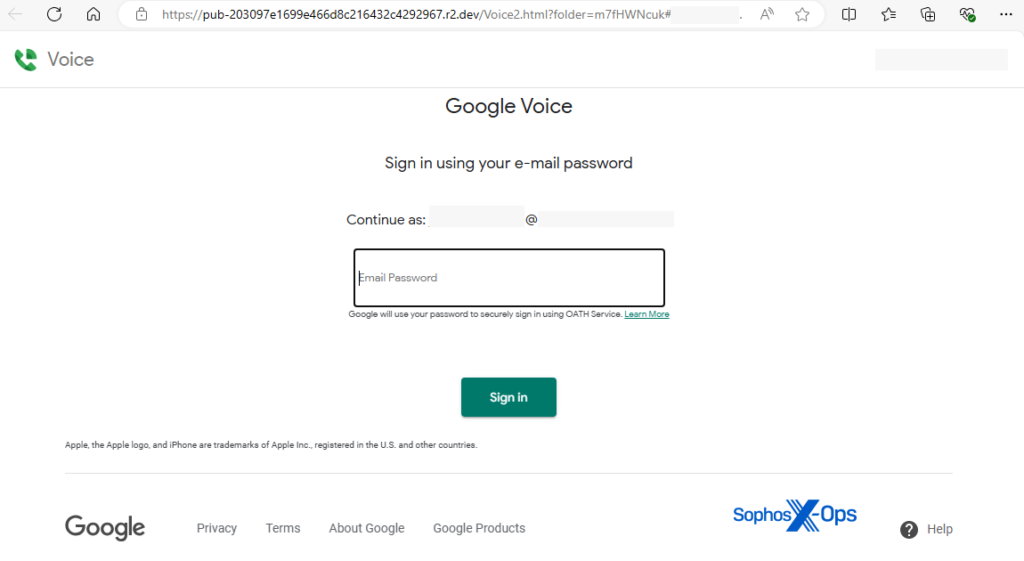
Image courtesy of Sophos
Key attack features include:
- Automation through JavaScript: SVG files auto-load phishing pages without requiring user interaction.
- Cloudflare CAPTCHA evasion: CAPTCHA gates complicate the analysis of the phishing sites.
- Multi-destination data exfiltration: Stolen credentials are sent to multiple locations simultaneously.
The use of SVGs for direct malware distribution is alarming. Sophos discovered SVG files containing base64-encoded data that leads to a ZIP archive housing malware, like the Nymeria keylogger. These findings underscore the need for robust defenses against these evolving threats.
For more information, check out Sophos Analysis, Cloudflare Research, and CSO Online.
SVGs as a Phishing Delivery Mechanism
Cloudflare's research highlights the flexibility of SVGs as a phishing delivery mechanism. The XML-based format allows for embedding JavaScript, transforming SVGs from simple images into active content capable of executing scripts. This capability poses significant risks as many security solutions fail to adequately inspect SVG files.
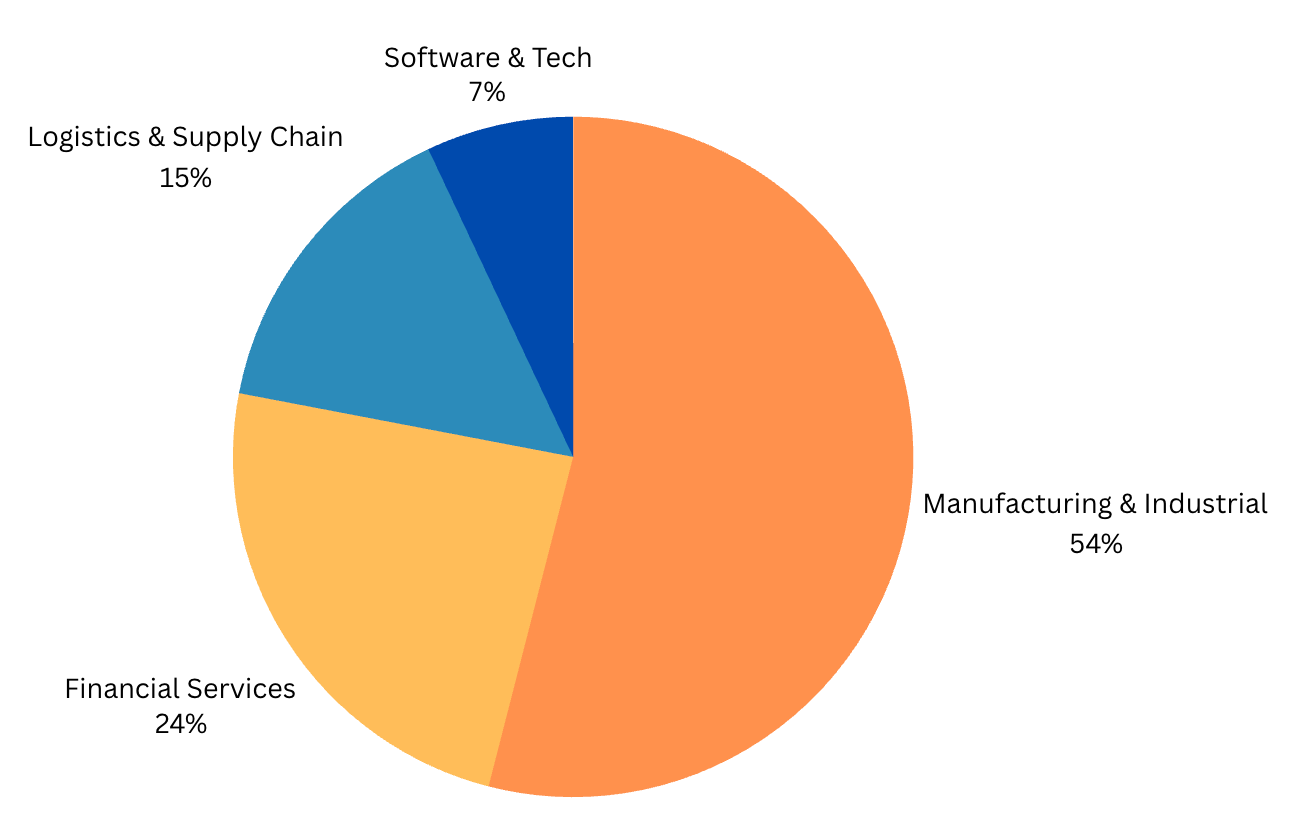
Image courtesy of Cloudflare
Phishing campaigns typically utilize SVGs in three ways:
- Redirectors: SVGs embed JavaScript that quickly redirects users to malicious sites when viewed.
- Self-contained phishing pages: SVGs contain full phishing pages encoded in Base64, making detection difficult.
- DOM injection: SVGs exploit weak Content Security Policies (CSPs) to run malicious code on legitimate websites.
The manufacturing and financial sectors are primary targets due to their high document volumes and interactions with third parties.
For further insights, refer to Cloudflare's Research, Sophos Analysis, and CSO Online.
Detection and Mitigation Strategies
Organizations must adopt robust detection and mitigation strategies to counter SVG-based phishing attacks. Cloudflare has implemented targeted detections for SVG files that contain malicious content. These detections assess embedded SVG for obfuscation, redirection, and script execution.
Image courtesy of Cloudflare
Key actions for organizations include:
- Set SVG files to open in text editors instead of browsers.
- Scrutinize unexpected emails and attachments.
- Utilize email security solutions that can detect malicious SVG files.
Enhancing email security with multi-factor authentication (MFA) can provide additional protection against unauthorized access.
For more details, explore Cloudflare Research, Sophos Analysis, and CSO Online.
Explore how our services at Gopher Security can help mitigate these threats and keep your organization secure. Contact us today at Gopher Security!

