Retail Sector Faces Surge in Ransomware Attacks: A 2025 Analysis
Retail Ransomware Attacks Increase
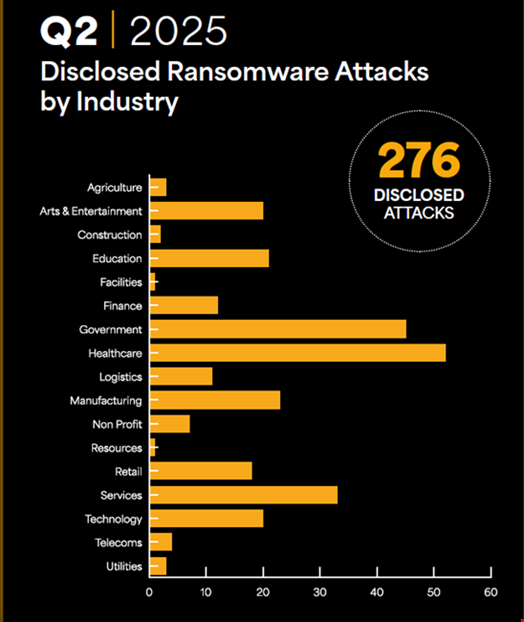
Publicly disclosed ransomware attacks on the retail sector globally surged by 58% in Q2 2025 compared to Q1, with UK-based firms being particularly targeted, according to a report by BlackFog. This spike in attacks follows high-profile breaches affecting retailers like Marks & Spencer (M&S), The Co-op, and Harrods, attributed to the threat actor known as Scattered Spider.
These incidents have led to significant operational disruptions and financial repercussions for the affected brands. For instance, M&S reported cyber costs exceeding £300 million. On July 10, UK law enforcement arrested four individuals linked to these attacks, underscoring the ongoing threat to the retail sector.
DragonForce Ransomware Group
The DragonForce ransomware group, emerging in late 2023, has quickly evolved into a Ransomware-as-a-Service (RaaS) model. This group recruits affiliate hackers to utilize their ransomware platform, taking a 20% cut from ransoms while managing malware development and payment negotiations. A DragonForce representative stated, “We are here for business and money.”
Recent attacks attributed to DragonForce or its affiliates include significant breaches at M&S, which faced widespread outages in late April 2025, and the Co-op, which experienced attempted breaches shortly thereafter.
Tactics of DragonForce
DragonForce employs sophisticated tactics for initial access, such as social engineering and phishing to gain credentials. In the M&S breach, attackers reportedly accessed the company's Active Directory database months prior to deploying ransomware, allowing them to use valid accounts for lateral movement within the network.
The group also utilizes PowerShell for executing payloads and automating tasks, often running malicious commands to disable security features. They have been observed using techniques like credential dumping from the LSASS process to gain domain administrator privileges.
Defense Strategies Against Ransomware
Organizations must adopt a multi-layered defense to mitigate the risk of ransomware attacks. Key strategies include:
- Implementing phishing-resistant multi-factor authentication and educating employees about social engineering tactics.
- Securing remote access points, such as VPNs and RDP servers, behind a Zero Trust Network Access (ZTNA) gateway.
- Protecting Active Directory and monitoring for suspicious credential retrieval.
- Deploying advanced Endpoint Detection & Response (EDR) tools configured to resist tampering.
- Regularly backing up critical data offline to prepare for potential recovery from an attack.
Gopher Security specializes in AI-powered, post-quantum Zero-Trust cybersecurity architecture, providing comprehensive solutions such as AI Inspection Engine for Traffic Monitoring and AI Ransomware Kill Switch. This technology converges networking and security across devices and environments, ensuring robust protection against evolving ransomware threats.
Explore our services at Gopher Security to enhance your organization's security posture.


