Police Disrupt Diskstation Ransomware Gang Targeting NAS Devices
Police disrupt “Diskstation” ransomware gang attacking NAS devices

Image courtesy of BleepingComputer
An international law enforcement action dismantled a Romanian ransomware gang known as 'Diskstation,' which encrypted the systems of several companies in the Lombardy region, paralyzing their businesses. The operation, codenamed 'Operation Elicius,' was coordinated by Europol and involved police forces from France and Romania.
Diskstation targets Synology Network-Attached Storage (NAS) devices, commonly used by companies for centralized file storage, data backup, and content hosting. The ransomware operation has been active since 2021, using various names like "DiskStation Security" and "LegendaryDisk Security." Attacks primarily focused on NAS devices exposed to the internet, demanding ransom payments ranging from $10,000 to hundreds of thousands of dollars.
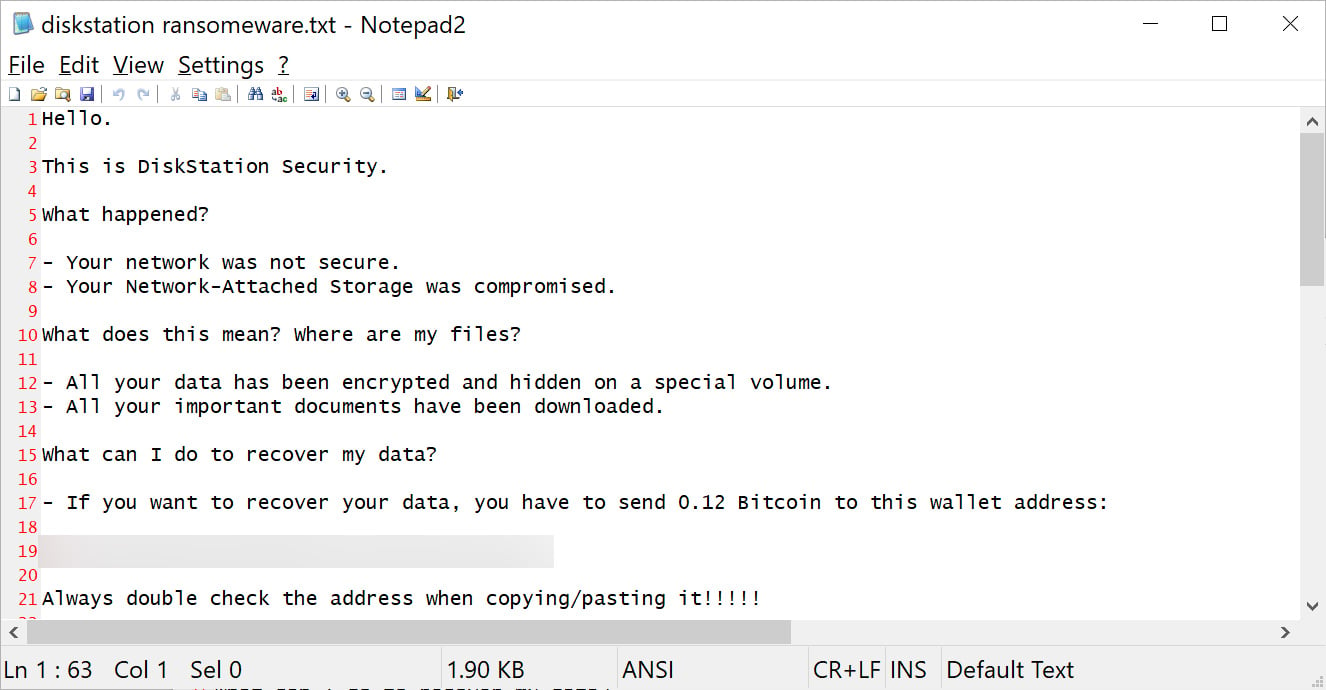
DiskStation ransom note
Source: BleepingComputer
The Postal and Cybersecurity Police Service noted that the targeted companies experienced severe outages due to data encryption, necessitating substantial ransom payments in cryptocurrency for data recovery. Victims included graphic and film production firms, event organizers, and NGOs focused on civil rights. Investigations led by the Milan Prosecutor's Office used forensic analysis and blockchain tracking to identify suspects, resulting in arrests in Bucharest.
To mitigate the risk of ransomware attacks, users are advised to keep their NAS devices updated, disable unnecessary services, limit internet exposure, and restrict access through VPNs.
INTERPOL disrupts over 22,000 malicious servers in global crackdown

Image courtesy of The Hacker News
In a global operation named Operation Synergia II, INTERPOL announced the takedown of over 22,000 malicious servers associated with various cyber threats, including ransomware. The operation, which ran from April to August 2024, targeted phishing and information stealer infrastructures with significant results, including the seizure of servers and electronic devices.
Key outcomes included the takedown of over 1,037 servers by Hong Kong police and the disruption of 291 servers in Macau. This coordinated effort underscores the continuous battle against cybercrime on a global scale.
Synology urges patch for critical zero-click RCE flaw

Image courtesy of The Hacker News
Synology has issued an urgent patch for a critical security vulnerability in its DiskStation and BeePhotos products, tracked as CVE-2024-10443 and dubbed RISK:STATION. This zero-click flaw allows attackers to execute root-level code on millions of devices without user interaction. It was showcased at the Pwn2Own Ireland 2024 hacking contest, emphasizing the importance of immediate software updates to protect against potential exploitation.
North Korean group collaborates with Play ransomware

Image courtesy of The Hacker News
A North Korean group has been linked to deploying the Play ransomware, marking a significant collaboration between state-sponsored actors and underground cybercriminal networks. The activity observed between May and September 2024 was attributed to a threat actor known as Jumpy Pisces. This collaboration marks a notable escalation in financial motivation among state-sponsored groups.
Four REvil ransomware members sentenced

Image courtesy of The Hacker News
In a rare occurrence, four members of the REvil ransomware group have been sentenced in Russia for their roles in hacking and money laundering. The court found them guilty, resulting in prison terms ranging from 4.5 to 6 years. This case highlights the growing legal repercussions for cybercriminals in Russia.
New Qilin.B ransomware variant emerges

Image courtesy of The Hacker News
Researchers have identified an advanced variant of the Qilin ransomware, named Qilin.B. This new version incorporates enhanced encryption methods, including AES-256-CTR and RSA-4096, making file decryption without the attacker's private key nearly impossible. Its sophistication and evasion tactics present a growing threat to organizations.
Why phishing-resistant MFA is essential

Image courtesy of The Hacker News
The Department of Homeland Security and CISA have issued a warning stressing the importance of implementing phishing-resistant multi-factor authentication (MFA) to combat ransomware attacks. Organizations are urged to move away from SMS-based OTPs in favor of more secure methods, highlighting the evolving threat landscape.
Lazarus Group exploits Google Chrome vulnerability
Image courtesy of The Hacker News
The Lazarus Group has exploited a zero-day vulnerability in Google Chrome to gain control over devices. Kaspersky reported that this attack chain targeted individuals within the cryptocurrency sector, emphasizing the ongoing risks associated with browser vulnerabilities.
Ransomware gangs use LockBit's fame to intimidate victims

Image courtesy of The Hacker News
Threat actors are manipulating the reputation of the notorious LockBit ransomware to exert pressure on victims. By disguising their ransomware as LockBit, attackers aim to instill fear and further control over their targets, complicating response efforts.
North Korean IT workers demand ransom for stolen data

