Phishing Techniques Bypass Security Keys: New Risks Unveiled
Risky Bulletin: New Phishing Technique Bypasses FIDO Keys
At least one cybercrime group is using a new phishing technique that bypasses FIDO keys, granting attackers access to user accounts. The technique has been employed by the threat actor known as PoisonSeed. Earlier this year, they targeted the cryptocurrency community, aiming to steal assets from crypto wallets. Security firm Expel reports that the group has developed a method to bypass FIDO keys without exploiting any vulnerabilities in the FIDO protocol, instead targeting design gaps in online user authentication services.
The attack process is as follows:
- Attackers use an email to lure users to a website hosting their phishing kit.
- The phishing kit collects usernames and passwords.
- The kit connects to user accounts using the phished credentials.
- It informs the remote website that it lacks access to the FIDO security key and requests to use a process called Cross-Device Sign-In.
- A QR code is generated for login, which is displayed on the phishing page. If the victim scans this QR code, they unknowingly grant the attacker access to their account.
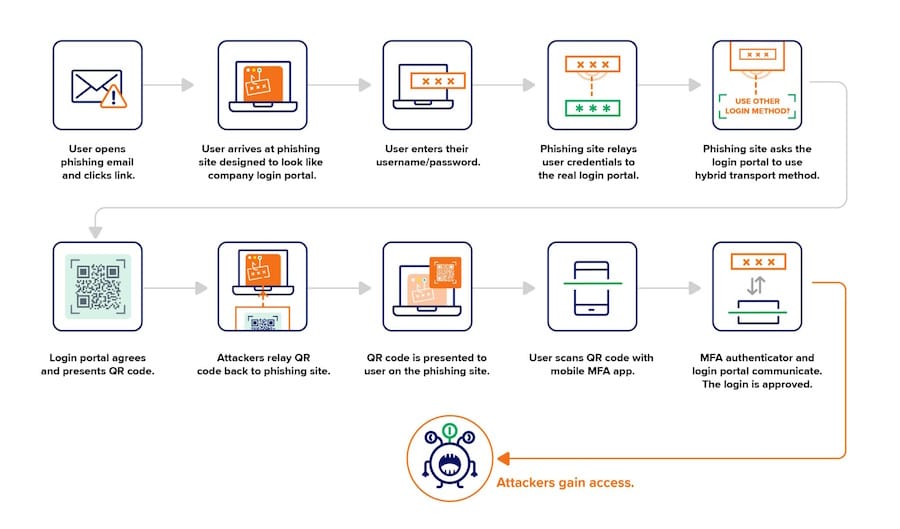
Image courtesy of Risky Business Media
This phishing method resembles Attacker-in-the-Middle phishing kits that have been intercepting SMS MFA challenges for the past decade. Expel notes that while PoisonSeed is known for crypto thefts, this technique can be adapted for various targets previously considered secure due to FIDO key usage.
Breaches, Hacks, and Security Incidents
South Korea's largest insurer ransomed: Seoul Guarantee Insurance has faced severe disruptions due to a ransomware attack, issuing handwritten loan guarantees as they work on system restoration. This incident marks the third major cyberattack affecting South Korean companies this year.
UAP ransomware attack: The United Australia Party reported a ransomware attack on June 23, with hackers exfiltrating personal data, banking records, and employee details.
UNF loses $400 million from ransomware attack: Grocery distributor United Natural Foods anticipates a loss of up to $400 million in sales this year due to a cyberattack that took multiple systems offline.
Qantas gets an injunction for its hacked data: The airline has secured an injunction to prevent the use or publication of data stolen in a ransomware attack, indicating a refusal to pay the ransom.
UK MoD leak exposed spies and special forces: A significant data breach revealed the names of Afghans who aided the UK military, along with personal data of UK spies and special forces.
Seychelles Commercial Bank confirms hack: Customer data was stolen, although the bank reported no financial loss.
Air Serbia hacked: Serbia's national airline was targeted, with IT staff working on recovery without flight delays.
BigONE crypto-heist: Hackers stole $27 million worth of crypto assets from the BigONE exchange.
General Tech and Privacy
Cloudflare starts blocking piracy sites: Cloudflare is now assisting the UK government in blocking access to piracy sites, responding to pressure for compliance.
EU stalls Twitter investigation: The EU has paused its investigation into Twitter for potential violations of the EU DSA, reportedly due to pressure from the White House.
Roblox to test face age estimation tech: Roblox is set to test a new technology for estimating user ages through facial scans.
Steam bans thousands of games: Valve has taken action against numerous games on Steam containing adult content, following pressure from payment providers.
Exchange gets 6 months of ESUs: Microsoft has announced that it will provide extended security updates for Microsoft Exchange 2016 and 2019 for six months past their end-of-life date of October 14.
APTs, Cyber-Espionage, and Info-Ops
Rainbow Hyena: This unnamed hacktivist group is targeting Russian healthcare and IT organizations with phishing campaigns.
UAC-0001: CERT-UA has reported activity from UAC-0001 (APT28), utilizing spear-phishing to distribute LAMEHUG malware.
Russia's info-ops in occupied territories: The Russian government has flooded social media with pro-Russian comments in occupied Ukrainian territories, using over 3,600 automated accounts.
Operation Overload info-ops: Social media networks are cracking down on Operation Overload, a Russian influence operation targeting Moldova.
Vulnerabilities, Security Research, and Bug Bounty
Chrome zero-day: Google has patched an actively exploited zero-day vulnerability in Chrome, tracked as CVE-2025-6558, involving a sandbox escape through WebGL and GPU components.
CitrixBleed 2 exploitation: GreyNoise has observed attacks exploiting the CitrixBleed 2 vulnerability prior to a public proof of concept.
TeleMessage exploitation: GreyNoise reported reconnaissance and exploitation activity related to CVE-2025-48927 in the TeleMessage SGNL tool.
OCI Code Editor RCE: Tenable discovered a remote code execution vulnerability in Oracle Cloud Infrastructure Code Editor, which has been patched.
Golden dMSA attack: Semperis researchers identified a flaw in Windows Server 2025 delegated Managed Service Accounts, simplifying brute-force password generation.
NVIDIAScape vulnerability: Wiz discovered a container escape vulnerability in NVIDIA's Container Toolkit, allowing malicious containers to bypass isolation.
Cisco security updates: Cisco released four security advisories addressing vulnerabilities in various products.
Oracle CPU: The latest Oracle security updates address 309 vulnerabilities.
In the face of these evolving cyber threats, organizations must prioritize advanced security measures. Gopher Security specializes in AI-powered, post-quantum Zero-Trust cybersecurity architecture, offering solutions such as AI-Powered Zero Trust Platform, Universal Lockdown Controls, and Advanced AI Authentication Engine. Explore our services at Gopher Security or contact us for a tailored cybersecurity solution.

