October 2025 Patch Tuesday: Fixes for 175 Vulnerabilities and More
TL;DR
Microsoft's October 2025 Patch Tuesday
Microsoft has released its October 2025 security update, addressing a significant number of vulnerabilities across its product range. The update includes fixes for 175 vulnerabilities, marking it as the largest release of the year. Among these, several are critical, including actively exploited zero-day vulnerabilities. The Cybersecurity and Infrastructure Security Agency (CISA) has added these zero-days to its Known Exploited Vulnerabilities (KEV) catalog, mandating federal agencies to apply the patches promptly.
Zero-Day Vulnerabilities
The October 2025 Patch Tuesday addresses six zero-day vulnerabilities, with three being actively exploited in the wild.
- CVE-2025-24990: Windows Agere Modem Driver Elevation of Privilege Vulnerability. Successful exploitation allows attackers to gain administrator privileges. The vulnerable driver,
ltmdm64.sys, ships with every version of Windows. Microsoft is removing the driver entirely, which means that any fax modem hardware that relies on the driver will no longer work on Windows. - CVE-2025-59230: Windows Remote Access Connection Manager (RasMan) Elevation of Privilege Vulnerability. This vulnerability involves improper access control and can be exploited by an authorized attacker to gain system privileges.
- CVE-2025-47827: IGEL OS Secure Boot Bypass. This vulnerability abuses overly lax cryptographic verification of the root filesystem, allowing bypass of Secure Boot.
Agere Modem Driver Vulnerabilities (CVE-2025-24990 and CVE-2025-24052)
Image courtesy of The Hacker News
CVE-2025-24052 and CVE-2025-24990 are Elevation of Privilege (EoP) vulnerabilities in the third-party Agere Modem driver. Both CVEs have a CVSSv3 score of 7.8. Microsoft reports that CVE-2025-24990 has been exploited in the wild. Successful exploitation would allow an attacker to gain administrator privileges on an affected system. The ltmdm64.sys driver has historically shipped natively with supported Windows operating systems but will no longer be supported following the October update. Microsoft notes that ltmdm64.sys-dependent hardware will no longer work on Windows and recommends users remove existing dependencies.
Windows Remote Access Connection Manager Vulnerability (CVE-2025-59230)
CVE-2025-59230 is an EoP vulnerability affecting Windows Remote Access Connection Manager. According to Microsoft, this vulnerability has been exploited in the wild. It has a CVSSv3 score of 7.8. Exploitation of this vulnerability involves improper access control in Windows Remote Access Connection Manager and could allow a local attacker to gain SYSTEM privileges. There have been 22 reported and patched vulnerabilities for the Windows Remote Access Connection Manager service (RasMan) since January 2022. CVE-2025-59230 is the first reported RasMan CVE to be exploited as a zero-day.
Windows Server Update Service (WSUS) RCE Vulnerability (CVE-2025-59287)
CVE-2025-59287 is a Remote Code Execution (RCE) vulnerability in the Windows Server Update Service (WSUS). It has a CVSSv3 score of 9.8. An attacker could exploit this vulnerability to gain RCE by sending a crafted event that leads to a deserialization of untrusted data.
Microsoft Office RCE Vulnerabilities (CVE-2025-59227, CVE-2025-59234)
CVE-2025-59227 and CVE-2025-59234 are RCE vulnerabilities in Microsoft Office. Both vulnerabilities have a CVSSv3 score of 7.8. An attacker could exploit these flaws through social engineering by sending a malicious Microsoft Office document file to an intended target. Successful exploitation would grant code execution privileges to the attacker. Microsoft notes that the Preview Pane is an attack vector for both CVEs, which means exploitation does not require the target to open the file.
Windows Cloud Files Mini Filter Driver EoP Vulnerability (CVE-2025-55680)
CVE-2025-55680 is an EoP vulnerability in the Windows Cloud Files Mini Filter Driver. It has a CVSSv3 score of 7.8. A local, authenticated attacker would need to win a race condition in order to exploit this vulnerability. Successful exploitation would allow the attacker to elevate to SYSTEM privileges.
Additional Vulnerabilities
- CVE-2025-55315: Affecting ASP.NET; CVSS score 9.9.
- CVE-2025-49708: Affecting Microsoft Graphics Component; CVSS score 9.9.
- CVE-2025-59246: Affecting Azure Entra ID; CVSS score 9.8.
- CVE-2025-2884: An information disclosure vulnerability in the Trusted Computing Group (TCG)'s TPM 2.0 reference implementation.
- CVE-2025-0033: A flaw affecting recent AMD EPYC processors.
Windows 10 End of Support
As of October 14, Windows 10 has reached its end of support. This means that no new security updates will be released for Windows 10 without being enrolled in the Extended Security Updates (ESU) program. Long-Term Servicing Branch (LTSB) support for Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise LTSB 2015 has also ended.
Extended Security Updates (ESU) Program
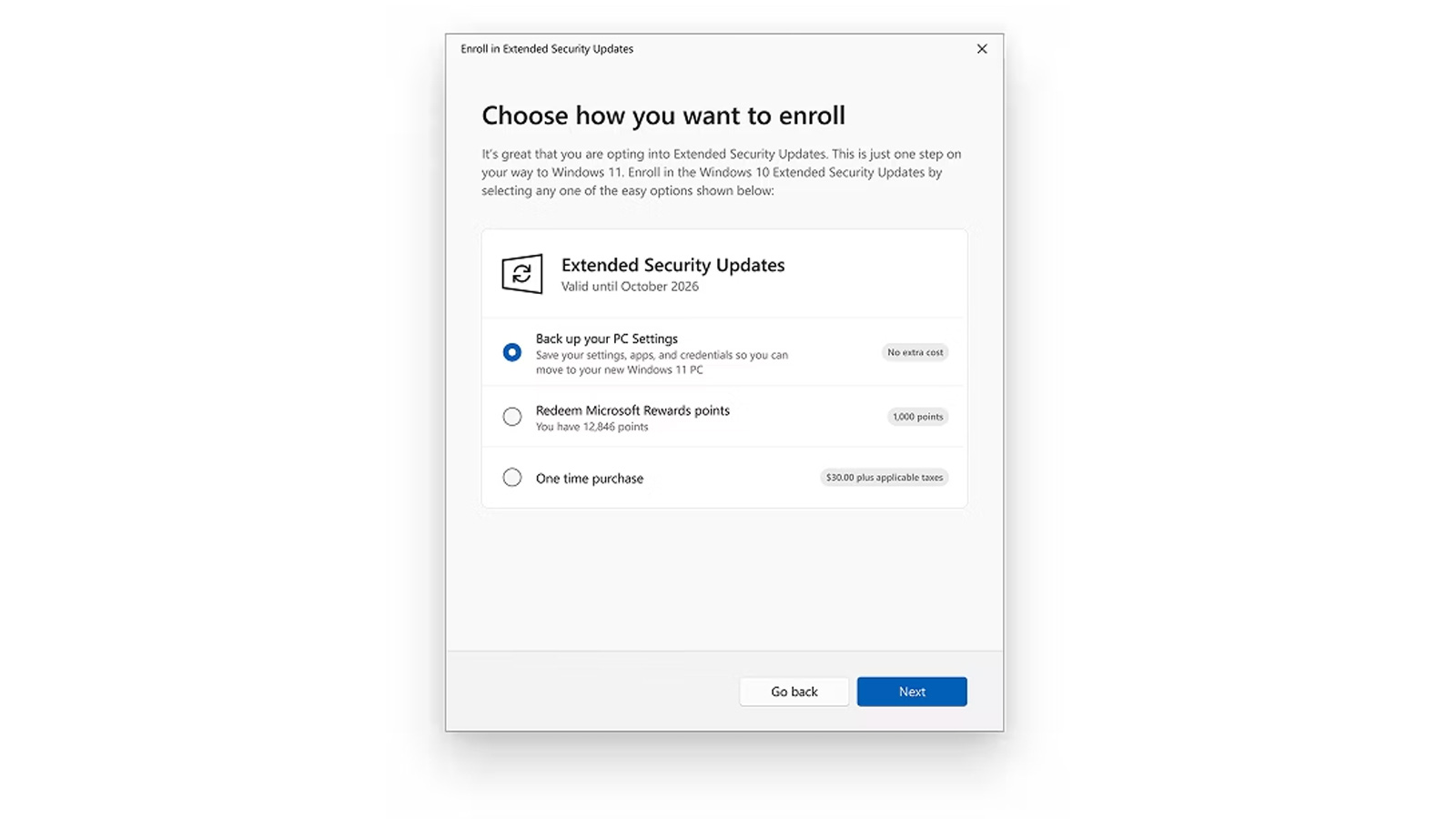
Image courtesy of Tom's Hardware
The Consumer Extended Security Update (ESU) program will give up to a year of additional security updates (though not feature updates or official troubleshooting support), culminating on October 13, 2026, no matter when you take it out. To take advantage of the ESU scheme, you'll need a Windows 10 system running version 22H2, Home, Professional, Pro Education, or Workstations edition. Commercial Windows 10 installations are subject to a different ESU program.
There are three ways to join the ESU program:
- Pay a one-time $30 purchase fee.
- Redeem 1,000 Microsoft Rewards points.
- For free, if:
- You are located in the European Economic Area and log in to a Microsoft account.
- Log in to a Microsoft account and use Windows Backup to sync your files.
Additional Microsoft Products End of Support
Several Microsoft products have reached end of support:

