Novel Malware Targets Southeast Asian Governments via AWS Lambda
State-Backed HazyBeacon Malware Uses AWS Lambda to Steal Data from SE Asian Governments
Governmental organizations in Southeast Asia are facing a new threat from a previously undocumented Windows backdoor known as HazyBeacon. This campaign, tracked by Palo Alto Networks Unit 42 under the name CL-STA-1020, is focused on collecting sensitive information from government agencies, particularly regarding trade disputes and tariffs.
The initial access vector for this malware remains unknown, but evidence suggests the use of DLL sideloading techniques. The attackers deploy a malicious version of a DLL named "mscorsvc.dll" alongside the legitimate Windows executable, "mscorsvw.exe." Once launched, the malicious DLL establishes communication with an attacker-controlled URL, allowing command execution and the download of additional payloads.
HazyBeacon is notable for its use of Amazon Web Services (AWS) Lambda URLs for command-and-control (C2) operations. This method allows the malware to leverage legitimate cloud functionality, creating a scalable and difficult-to-detect communication channel. Security researcher Lior Rochberger commented on this technique: "AWS Lambda URLs are a feature of AWS Lambda that allows users to invoke serverless functions directly over HTTPS."
Defenders are urged to monitor outbound traffic to AWS endpoints, particularly those associated with Lambda URLs, especially when initiated by unusual binaries.
Exfiltration Techniques
The malware includes a file collector module that targets specific file extensions (such as doc, docx, xls, xlsx, and pdf) within a defined time range. This includes files related to recent tariff measures imposed by the United States. The attackers also utilize services like Google Drive and Dropbox for data exfiltration, blending their activities with normal network traffic.
In the analyzed incident, attempts to upload files to these cloud storage services were blocked. After data collection, the threat actors execute cleanup commands to erase traces of their activities, ensuring no evidence remains.
Behind the Clouds: Covert C2 Communication
Unit 42's investigation revealed that CL-STA-1020 employs AWS Lambda URLs as its C2 infrastructure, a novel technique that allows attackers to remain undetected. This method was first reported by Trellix in the context of advanced persistent threat (APT) activities. The AWS Lambda service runs code in response to events, and Lambda URLs extend this functionality by providing dedicated HTTPS endpoints.
The manipulation of AWS services provides tactical advantages, enabling threat actors to blend their C2 traffic with legitimate AWS communications. This approach complicates traditional detection methods, making it essential for organizations to develop context-aware baseline monitoring strategies.
Indicators of Compromise
Key indicators of compromise for the HazyBeacon backdoor include:
- SHA256 hashes for the malicious DLL (C:\Windows\assembly\mscorsvc.dll)
- SHA256 hashes for Google Drive file uploader utilities found in the ProgramData directory.
Organizations must enhance their monitoring of cloud resource usage and develop strategies to detect suspicious communication patterns with trusted cloud services.
For more detailed insights, security teams can leverage Palo Alto Networks' Advanced WildFire and Cortex XDR to improve their defense posture.
Sandman APT: A New Threat Targeting Telecommunications
Sandman APT, an unidentified threat actor, is actively targeting telecommunications providers in the Middle East, Western Europe, and South Asia. This threat actor employs a modular backdoor known as LuaDream, which utilizes the LuaJIT platform for its operations. LuaDream's architecture indicates it is an actively developed project, aiming for stealth and evasion.
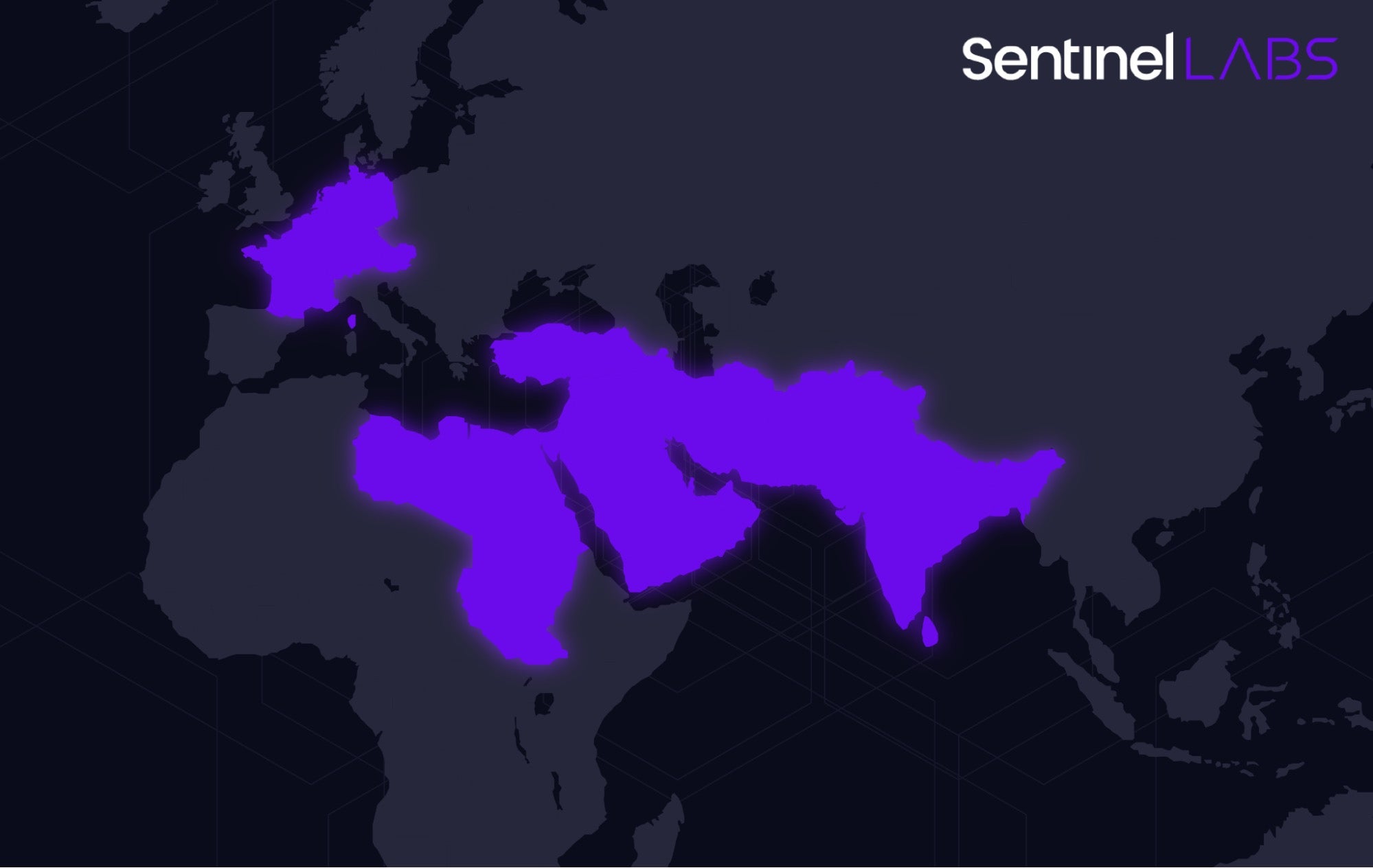
The Sandman APT's activities are characterized by strategic lateral movements within targeted networks. The attacker uses DLL hijacking to execute LuaDream by placing a malicious DLL, ualapi.dll, that masquerades as a legitimate component. This technique allows the malware to load without raising alarms.
Conclusion
The ongoing threat landscape features increasingly sophisticated actors like those behind HazyBeacon and Sandman APT. Their use of legitimate cloud infrastructure for malicious purposes underscores the importance of robust security measures in monitoring and analyzing unusual traffic patterns.
Organizations are encouraged to explore advanced detection and response solutions tailored for cloud environments to combat these evolving threats. For more information on enhancing your cloud security posture, visit Gopher Security .

