North Korean Hackers Distribute XORIndex Malware via npm Packages
North Korean Actors Expand Contagious Interview Campaign with New Malware Loader
North Korean threat actors have escalated their Contagious Interview campaign by introducing a new malware loader named XORIndex. This loader has gathered over 9,000 downloads from June to July 2025, primarily targeting developers, job seekers, and individuals likely to possess cryptocurrency or sensitive credentials. The loader is designed to collect data and deploy second-stage malware, leading to potential cryptocurrency theft.
The malicious strategy involves publishing 67 new packages to the npm registry, collectively downloaded more than 17,000 times. Among these, 28 packages incorporated XORIndex, with others utilizing the previously identified HexEval loader, which has amassed over 8,000 additional downloads. Socket researchers are actively pursuing takedown requests for these packages and have sought the suspension of related npm accounts.
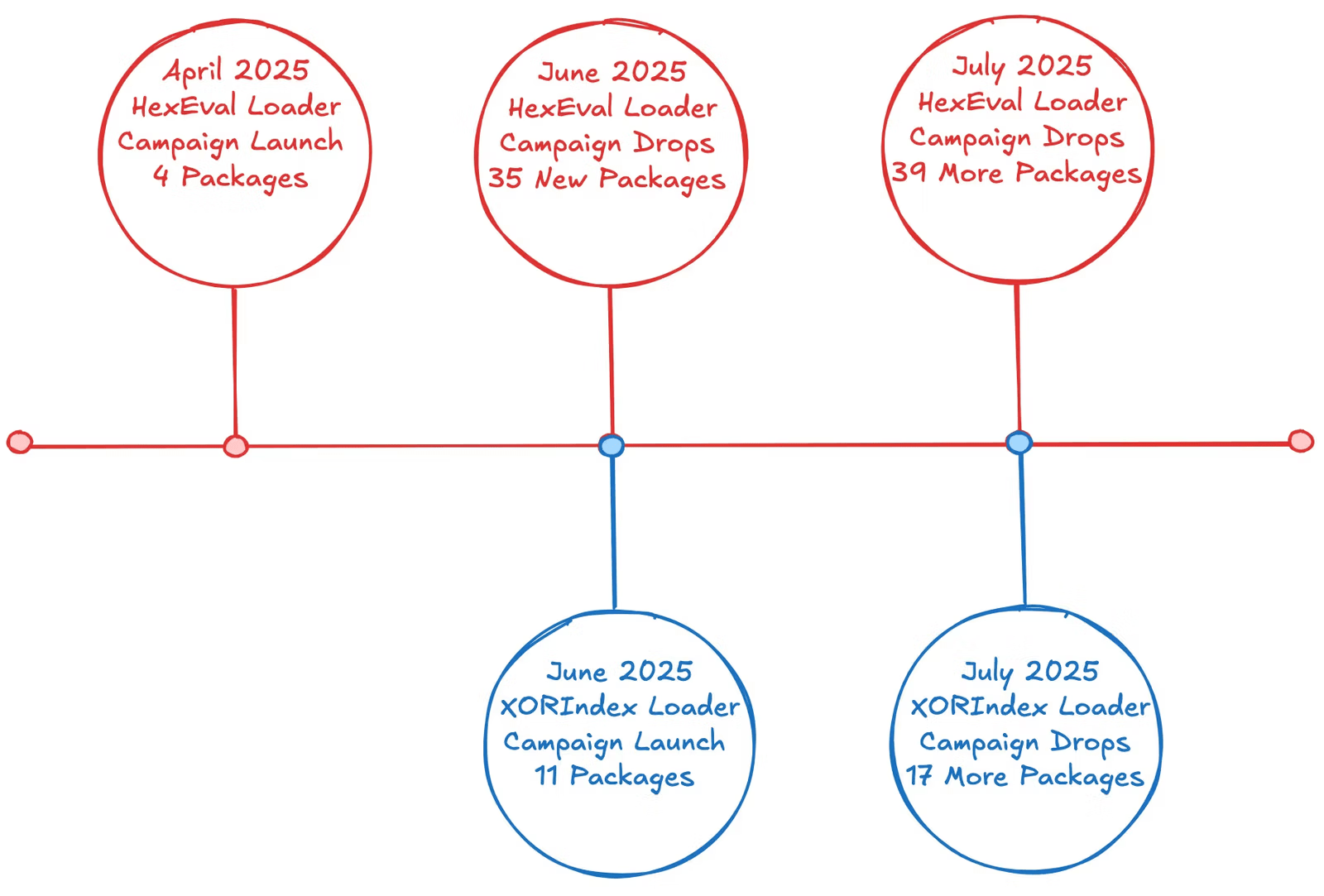
Image courtesy of Security Affairs
The development of XORIndex illustrates the ongoing sophistication of the Contagious Interview actors, who are committed to developing stealthier and more resilient software supply chain malware, capable of full system compromise. According to the researchers, they expect North Korean threat actors to continue reusing existing loaders like HexEval and XORIndex while introducing new obfuscation techniques.
For more details, refer to the Socket blog here.
Multi-Function Malware Loader
XORIndex is embedded in 28 malicious npm packages distributed across 18 npm accounts, registered with 15 different email addresses. Similar to HexEval, XORIndex performs various functions for the attackers. Upon installation, it collects local host telemetry, including hostname, current username, operating system type, and external IP address, which it exfiltrates to hardcoded command and control (C2) infrastructure.
This malware also loads BeaverTail, a common second-stage payload used in the North Korean Contagious Interview attacks. BeaverTail is designed to scan for data in known desktop wallet directories and browser extension paths, ultimately compromising cryptocurrency wallets, including wallet databases and macOS keychain credentials.

Image courtesy of TechRadar
BeaverTail subsequently attempts to load InvisibleFerret, a known third-stage backdoor related to this operation. The Contagious Interview campaign, first reported in November 2023, has evolved with multiple malware versions surfacing, underscoring the persistent threat posed by North Korean state-sponsored groups like Lazarus.
To learn more about the campaign, check out the Infosecurity Magazine article here.
Ongoing Contagious Interview Campaign
The Contagious Interview campaign continues to assert pressure on developers and tech professionals. The North Korean threat actors leverage job search platforms, such as LinkedIn, to pose as recruiters and entice developers with fake job offers. Victims are often led to download malicious software disguised as legitimate development tools.
The attack surface is considerable, with the malicious packages collectively attracting over 17,000 downloads. The malware deployed ranges from BeaverTail to XORIndex and HexEval, with attackers continually diversifying their approaches.
According to Socket researcher Kirill Boychenko, “The Contagious Interview operation continues to follow a whack-a-mole dynamic, where defenders detect and report malicious packages, and North Korean threat actors quickly respond by uploading new variants using the same, similar, or slightly evolved playbooks.”
For ongoing updates regarding this campaign, refer to the full report on The Hacker News here.

