North Korean Hackers Deploy NimDoor macOS Malware via Fake Zoom Updates
MacOS Malware NimDoor Weaponizing Zoom SDK Update to Steal Keychain Credentials

Image courtesy of Cybersecurity News
A sophisticated MacOS malware campaign, named NimDoor, has emerged, targeting Web3 and cryptocurrency organizations through weaponized Zoom SDK updates. Attributed to North Korean threat actors likely associated with Stardust Chollima, this malware has been active since at least April 2025.
The attack begins with social engineering tactics, where threat actors impersonate trusted contacts on Telegram, inviting victims to schedule Zoom meetings via Calendly. Victims receive malicious emails containing AppleScript disguised as legitimate “Zoom SDK updates.”
The malware’s creators inadvertently left identification markers, including a typo that changed “Zoom” to “Zook” in script comments, which aids in detection. PolySwarm analysts identified NimDoor’s unique utilization of the Nim programming language, complicating static analysis due to its compile-time execution mechanisms.
Upon execution, NimDoor triggers a multi-stage infection deploying two distinct Mach-O binaries: a C++ binary responsible for payload decryption and data theft operations, and a Nim-compiled “installer” that establishes persistence components. The malware uses deliberately misspelled components like “GoogIe LLC” to evade suspicion while maintaining system persistence through LaunchAgent mechanisms.
Advanced Persistence and Communication Mechanisms
NimDoor introduces a unique persistence mechanism utilizing SIGINT/SIGTERM signal handlers, marking a significant evolution in MacOS malware. This approach ensures automatic reinstallation upon termination attempts or system reboots, enhancing operational longevity.
The malware establishes command-and-control communications through TLS-encrypted WebSocket protocols, with hex-encoded AppleScript components beacons transmitting every 30 seconds to hardcoded servers. These communications exfiltrate running process lists while enabling remote script execution capabilities, effectively creating a persistent backdoor into compromised systems.
The malware’s data exfiltration capabilities target critical assets including Keychain credentials, browser data across multiple platforms (Chrome, Firefox, Brave, Arc, Edge), and Telegram databases containing cryptocurrency wallet information and sensitive communications.
Technical Analysis of Execution Chain
The attack chain starts with social engineering, where attackers impersonate trusted contacts over Telegram and lure victims into scheduling Zoom calls. Victims receive phishing emails with malicious Zoom SDK update scripts that are booby-trapped AppleScript files. These scripts are heavily padded with thousands of lines to evade detection.
Once executed, these scripts download further payloads to the victim's machine. Researchers found two primary Mach-O binaries: one written in C++ and another in Nim. The C++ binary is responsible for writing an encrypted embedded payload to disk, while the Nim-compiled installer sets up persistence.
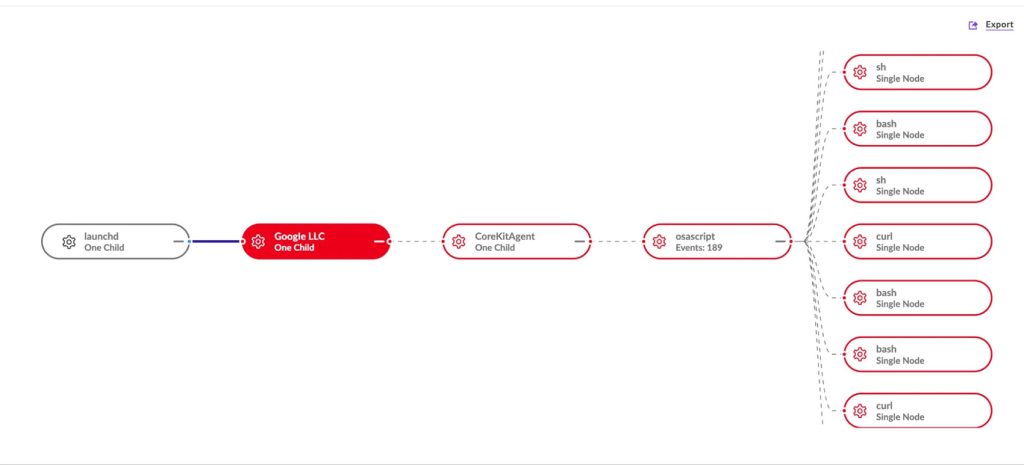
Image courtesy of SentinelLabs
Data Theft Mechanisms
Data exfiltration is accomplished through Bash scripts that scrape browser history, Keychain credentials, and Telegram data. Targeted browsers include Arc, Brave, Firefox, Chrome, and Microsoft Edge. The malware also steals encrypted local Telegram databases for potential offline cracking.
Persistence is achieved through clever naming conventions and usage of macOS LaunchAgents. For instance, the malware installs binaries with names like "GoogIe LLC," substituting a capital "i" for a lowercase "L" to blend in with legitimate Google files. Another binary, "CoreKitAgent," monitors system signals to reinstall itself if terminated.
Recommendations for Mitigation
Users should avoid running scripts or software updates received through unexpected emails or messages. Keeping macOS and all installed applications updated with the latest security patches is crucial. Utilizing reputable endpoint security tools can help detect suspicious behaviors like process injection or malicious AppleScripts. Regularly reviewing login items and LaunchAgents can reveal unauthorized entries maintaining persistence.
To protect against threats like NimDoor, it’s essential to adopt strong, unique passwords and enable multi-factor authentication where possible.
For detailed insights into the malware's architecture and countermeasures, refer to the complete technical analysis by SentinelLabs.

