New PHP-Based Interlock RAT Targets Multiple Industries via FileFix
New PHP-Based Interlock RAT Variant Uses FileFix Delivery Mechanism to Target Multiple Industries
The Interlock ransomware group has introduced a PHP variant of its remote access trojan (RAT) as part of a campaign leveraging a ClickFix variant known as FileFix. This new tool targets various industries since May 2025, according to a report by the DFIR Report in collaboration with Proofpoint.
"Since May 2025, activity related to the Interlock RAT has been observed in connection with the LandUpdate808 (aka KongTuke) web-inject threat clusters," the report states. The campaign begins with compromised websites, where a hidden script is injected into the HTML, often without knowledge of the site owners or visitors.
The embedded JavaScript acts as a traffic distribution system (TDS), redirecting users to counterfeit CAPTCHA verification pages. This process entices users to execute a PowerShell script that ultimately deploys the NodeSnake (aka Interlock RAT). The malware is designed for persistent access, system reconnaissance, and remote command execution capabilities.
New campaigns have observed the distribution of this PHP variant through FileFix, which leverages the Windows operating system's capabilities to instruct victims into executing commands via File Explorer's address bar. Once installed, the malware carries out reconnaissance of the infected host, exfiltrating system information in JSON format. It checks for privileges (USER, ADMIN, or SYSTEM) and establishes contact with a remote server to download and execute EXE or DLL payloads.
Persistence is achieved through changes to the Windows Registry, while lateral movement is facilitated via the Remote Desktop Protocol (RDP). A significant feature of the trojan is its use of Cloudflare Tunnel subdomains to mask the true location of the command-and-control (C2) server, ensuring communication remains intact even if the Cloudflare Tunnel is disrupted.
"This discovery highlights the continued evolution of the Interlock group's tooling and their operational sophistication," researchers noted. The shift to PHP from Node.js marks a notable change in their attack strategy.
Interlock RAT Functionality and Deployment
The Interlock ransomware group's deployment of its new PHP-based RAT via FileFix marks a significant shift in their operational tactics. Researchers from the DFIR Report, in collaboration with Proofpoint, confirm that this new variant is being distributed through compromised websites using hidden scripts to prompt victims into running a PowerShell script.
“The campaign begins with compromised websites injected with a single-line script hidden in the page’s HTML, often unbeknownst to site owners or visitors,” the DFIR report explains. This method utilizes heavy IP filtering to serve the payload, which prompts the user to interact with fake CAPTCHA checks to execute the malicious script.
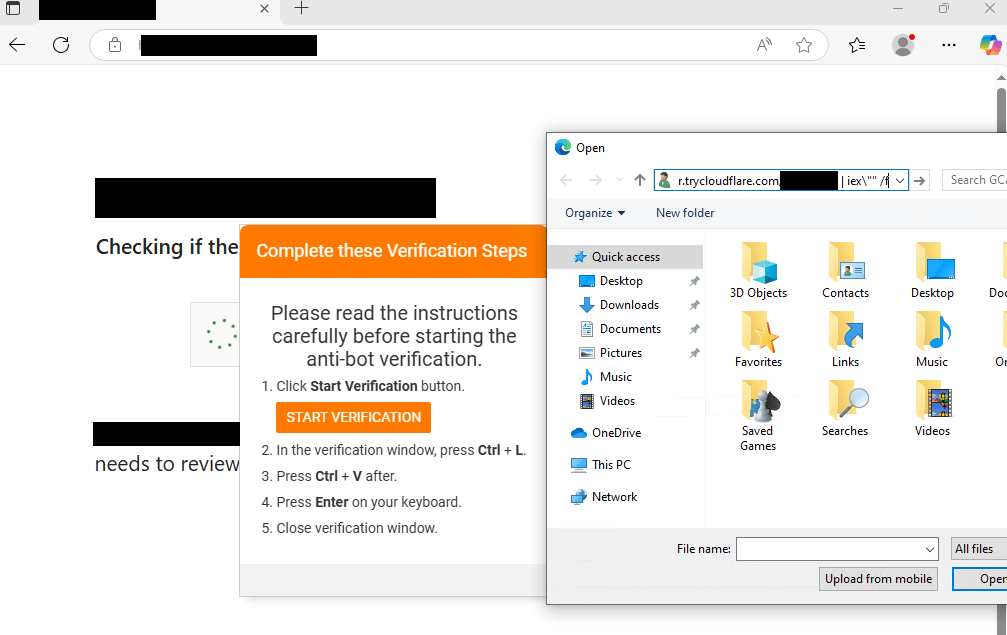
Image courtesy of Security Affairs
The PHP version executes through PowerShell and launches from an unusual path using a custom configuration file. FileFix, an evolution of ClickFix, exploits Windows File Explorer’s address bar to trick users into executing commands. Once installed, the Interlock RAT performs reconnaissance and exfiltrates system information, establishing a robust command and control channel with attackers' infrastructure.
“The Interlock RAT establishes a robust command and control (C2) channel with the attackers’ infrastructure,” the report continues. This variant also contains hardcoded fallback IP addresses, ensuring continuous communication even if the primary C2 is disrupted.
Interlock RAT supports various commands, including downloading and executing executables or DLLs, executing arbitrary shell commands, and setting up persistence via registry keys. This evolution of the RAT indicates a more sophisticated approach to cyber threats.
For further information on the evolving landscape of cybersecurity threats and tools, consider checking these resources: Malware Analysis, News and Indicators, Interlock ransomware group, and Cloudflare Tunnel.
Explore our services at Gopher Security for cutting-edge cybersecurity solutions tailored to your needs. Contact us for more information.

