New Phishing Technique Bypasses FIDO MFA, Endangers Security
Phishing Techniques and FIDO Security
FIDO Downgrade Attack
Recent findings indicate that phishers are employing a new technique to downgrade FIDO multifactor authentication (MFA) rather than bypassing it entirely. This technique is attributed to a group known as PoisonSeed, which has been reported to use phishing emails to lure users to fake login pages, specifically targeting services like Okta.
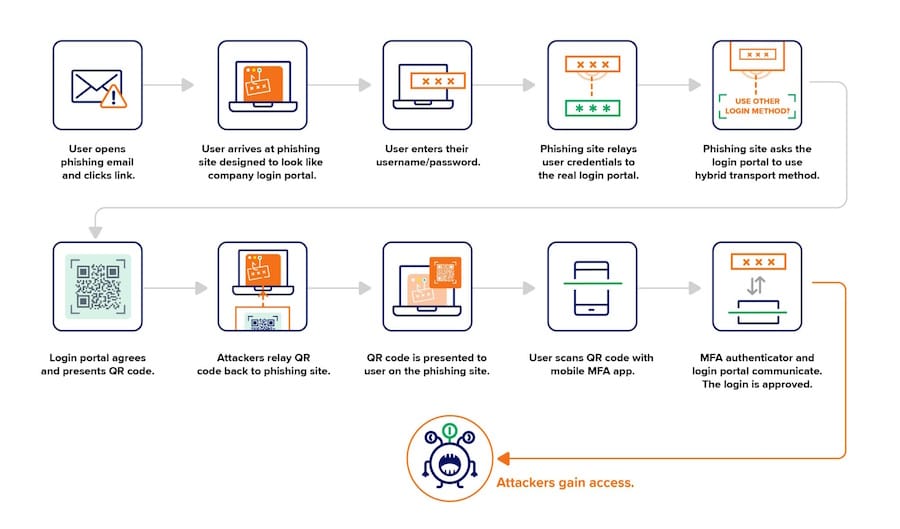
Image courtesy of Risky Business Media
The process begins when a user enters their credentials on a fraudulent site, and the attackers simultaneously log into the real service using the same credentials. Upon this successful entry, the phishing site initiates a cross-device sign-in, capturing a QR code displayed by the legitimate service. When the victim scans this QR code using their mobile device, they inadvertently grant the attackers access to their accounts.
The attack hinges on the design of authentication flows in online services, exploiting weaknesses rather than flaws in the FIDO protocol itself. According to security analysts, the attack can be classified as a downgrade rather than a bypass, emphasizing the importance of strictly adhering to FIDO security specifications to mitigate such risks. Gopher Security's AI-Powered Zero Trust Platform can help organizations strengthen their authentication processes by ensuring compliance with best practices in MFA.
For more detailed analysis, see Phishers have found a way to downgrade—not bypass—FIDO MFA and Risky Bulletin: New phishing technique bypasses FIDO keys.
Device Code Flow Phishing
The Device Code Flow technique poses significant risks to FIDO implementations. This method allows attackers to leverage the OAuth 2.0 Device Authorization Grant to initiate phishing attacks that are difficult to detect. When a user interacts with the original authentication page, the phishing process is executed in the background, making it nearly impossible for the victim to realize they are being attacked.
The streamlined process involves a headless browser that automates the generation of a device code and enters it on the legitimate site without any input from the user. This effectively bypasses the 10-minute token validity limitation and leverages the user's active session, further complicating detection efforts.
For a deeper understanding, refer to Phishing despite FIDO, leveraging a novel technique based on the Device Code Flow.
Mitigation Strategies for FIDO Security
To combat these advanced phishing techniques, organizations must adopt robust policies and technologies. Implementing Gopher Security's Universal Lockdown Controls can help ensure that only authorized users can access sensitive systems, while the Advanced AI Authentication Engine enhances the verification process by analyzing user behavior and context.
The integration of Post Quantum Cryptography in Gopher Security's architecture ensures resilience against future threats, protecting against potential attacks that might exploit quantum computing advancements.
Security analysts should remain vigilant and consider disabling Device Code Flow where feasible. Continuous monitoring through tools like the AI Inspection Engine for Traffic Monitoring can detect anomalies that may indicate a phishing attempt, reinforcing overall security posture.
For additional insights, see How To Bypass Multifactor Authentication and explore Gopher Security’s offerings at Gopher Security.

