Malware Campaign DollyWay Breaches 20,000 WordPress Sites
Malware campaign 'DollyWay' breached 20,000 WordPress sites

A malware operation dubbed 'DollyWay' has been operating since 2016, compromising over 20,000 WordPress sites globally to redirect users to malicious sites. This campaign has evolved significantly, utilizing advanced evasion, reinfection, and monetization strategies.
According to GoDaddy researcher Denis Sinegubko, the latest version (v3) of DollyWay functions as a large-scale scam redirection system. Historically, it has also distributed more harmful payloads like ransomware and banking trojans. A recent report by GoDaddy explains that the operation was named after the tell-tale string found in some variations of the malware: define('DOLLY_WAY', 'World Domination').
Thousands of stealthy infections
DollyWay v3 primarily targets vulnerable WordPress sites by exploiting n-day flaws in plugins and themes. As of February 2025, it generates 10 million fraudulent impressions per month by redirecting visitors to fake dating, gambling, crypto, and sweepstakes sites.
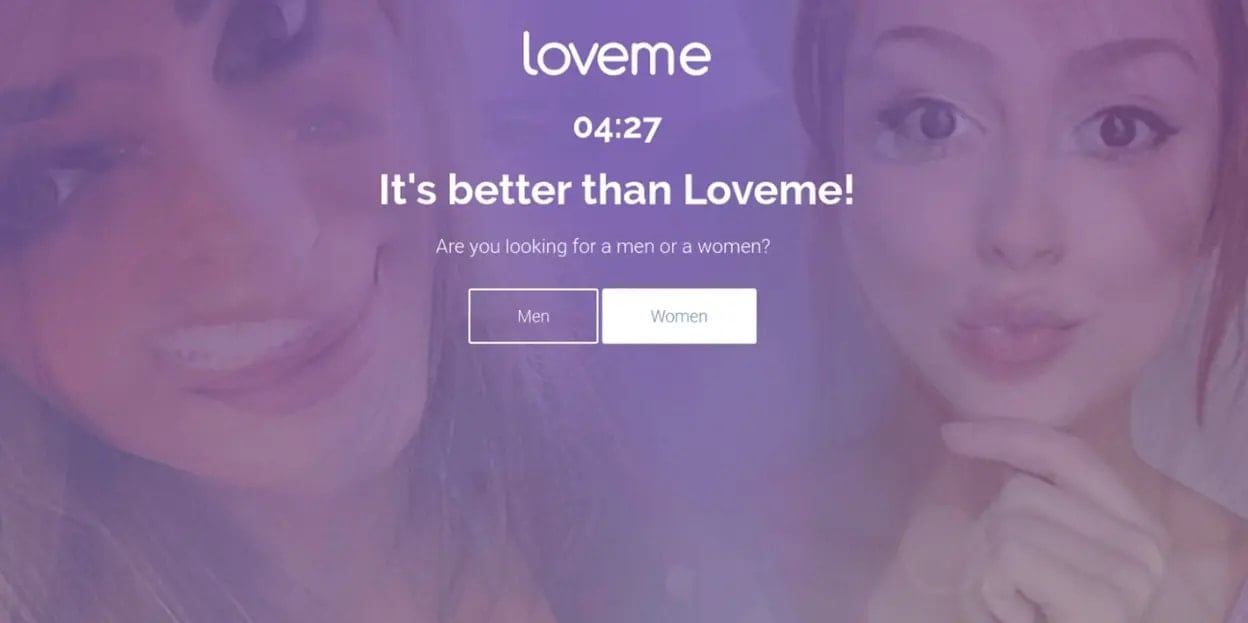
The campaign uses VexTrio and LosPollos affiliate networks to monetize its operations after filtering visitors through a Traffic Direction System (TDS). This system analyzes and redirects web traffic based on various factors such as location, device type, and referrer. Cybercriminals typically use TDS systems to send users to phishing sites or malware downloads.
The websites are infected via script injection with 'wp_enqueue_script,' dynamically loading a second script from the compromised site. This second stage collects visitor referrer data to help categorize redirection traffic, then loads the TDS script that validates target visitors for redirection.
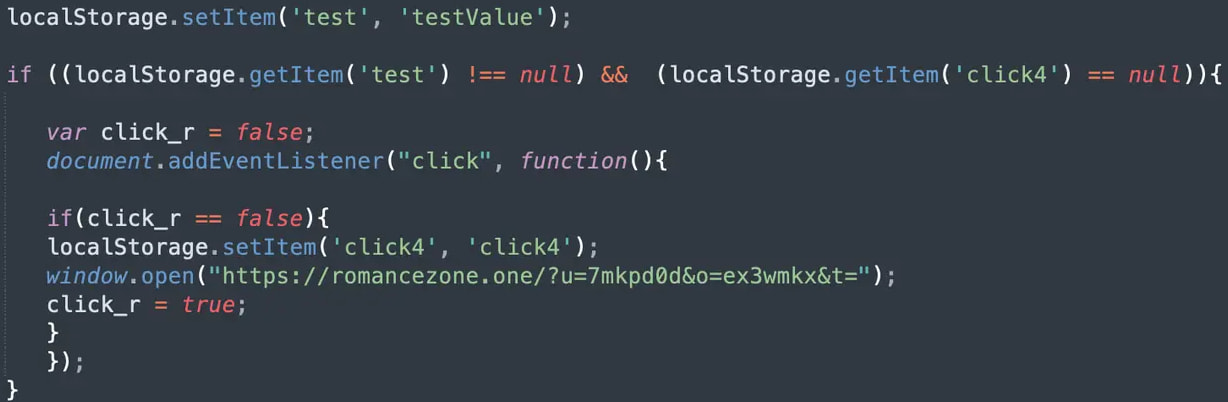
The malware uses affiliate tracking parameters, ensuring attackers receive payment for each redirection. Notably, the final redirect occurs only when the visitor interacts with a page element, evading detection by passive scanning tools.
Auto-reinfection ensures persistence
Sinegubko notes that DollyWay is a persistent threat, automatically reinfecting a site with every page load, complicating removal efforts. The malware spreads PHP code across all active plugins and adds a copy of the WPCode plugin, which contains obfuscated malware snippets.
The hackers hide WPCode from the WordPress plugin list, preventing administrators from detecting or deleting it. Additionally, DollyWay creates admin users with random 32-character hex strings, hiding these accounts from the admin panel and making them visible only through direct database inspection.
GoDaddy has shared a complete list of indicators of compromise (IoCs) associated with DollyWay to assist in defending against this threat.
WordPress Sites Turned Weapon: VexTrio and Affiliates
VexTrio's Traffic Distribution Service (TDS) has been linked to other operations, indicating a sophisticated cybercriminal enterprise designed to disseminate malicious content. VexTrio operates as a group of malicious adtech companies that distribute scams and harmful software via different advertising formats, including smartlinks and push notifications, according to Infoblox.
The malicious adtech companies under VexTrio include Los Pollos, Taco Loco, and Adtrafico, which form a commercial affiliate network. This network connects malware actors with advertising affiliates who promote various illicit schemes, including gift card fraud and phishing sites.
VexTrio's operations have faced setbacks, such as a November 2024 revelation that Los Pollos was part of their network, leading to changes in tactics among threat actors relying on this network.
DollyWay World Domination: Eight Years of Evolving Website Malware

GoDaddy Security researchers have linked multiple malware campaigns into a single operation known as "DollyWay World Domination." This operation has compromised over 20,000 websites globally in the past eight years. The latest campaign demonstrates sophisticated capabilities, including cryptographically signed data transfers and automatic reinfection mechanisms.
The malware works exclusively on WordPress sites, leveraging a distributed network of Command and Control (C2) and TDS nodes hosted on compromised sites. Historical campaigns have included aggressive payloads, but the current focus is on redirecting site visitors through injected redirect scripts.
Technical analysis of current campaign (DollyWay v3)
DollyWay v3 employs a sophisticated four-stage injection chain designed to evade detection:
Stage 1: Initial injection
The first stage uses WordPress's wp_enqueue_script function to append a link to a dynamically generated script whenever someone visits an infected domain. Each injection includes a unique 32-character hexadecimal parameter.
Stage 2: Dynamic loading and referrer collection
This stage dynamically loads the next script while collecting information for the TDS.
Stage 3: TDS script injection
At this point, the malware generates a script that loads from three random nodes (third-party infected sites) that act as TDS.
Stage 4: The redirect
The final scripts returned by the TDS nodes contain the actual redirect code, leading visitors to VexTrio/LosPollos links.
Persistent reinfection mechanism
The malware reinfects sites with each page load through complex procedures that disable security plugins, re-obfuscate injections, and create new malicious snippets. The presence of malicious admin users further complicates detection and removal efforts.
Malware Redirects WordPress Traffic to Harmful Sites

Recent investigations revealed a malware infection redirecting WordPress traffic to suspicious URLs. This form of malicious code was injected into the theme's functions.php, leading to the distribution of information-stealing malware.
The malware employs techniques to bypass detection by checking for specific cookies and filtering requests based on user agents. It uses complex regular expressions to filter requests and redirects users to potentially harmful domains.
Potential Impact of the Malware
The primary payload of this malware is redirecting users, but it may also create hidden backdoors for persistent access. Attackers can leverage this method to compromise sensitive data and inject further malicious content into the victim's website.
How Was the Site Likely Infected?
Infections may occur due to outdated plugins, poorly designed custom code, pre-existing backdoors, or compromised user accounts. The attackers behind such infections may aim to damage the website’s reputation, impact search rankings, exploit traffic, or inject further spam or malware.
Mitigation Tips for WordPress Website Administrators
Website administrators should monitor for unusual update prompts, review installed plugins, reset admin passwords, and enable multi-factor authentication.
For users, it is advisable to install specialized security software to prevent interactions with compromised websites.
Explore our services at undefined for more information on protecting your website against these threats. Contact us today for expert assistance in securing your WordPress site.


