Large-Scale Lumma Infostealer Campaign Abuses GitHub for Malware
The Rise of Lumma Info Stealer
The Malware-as-a-Service (MaaS) model is providing cybercriminals with accessible and sophisticated tools for executing cyber attacks. One notable example is the Lumma info stealer, which has been operational since 2022, targeting sensitive data such as login credentials and banking information. This malware is distributed on dark web forums and has seen increased visibility with various command-and-control (C2) servers identified.
Lumma Info Stealer Background
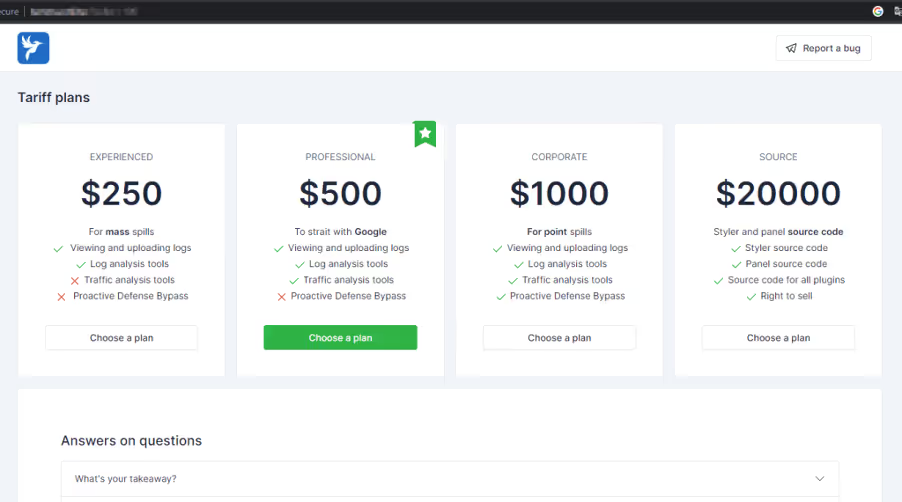
Lumma, also known as LummaC2, is marketed to threat actors with tiered subscription models, making it affordable for even novice attackers. Priced from USD 250, it has gained traction in marketplaces alongside other info stealers like Vidar and Racoon. The malware primarily targets cryptocurrency wallets and two-factor authentication (2FA) extensions, indicating a focus on high-value targets.
Attack Vectors and Distribution Methods
Lumma has been distributed through various deceptive methods, including masquerading as popular software like VLC or ChatGPT. Attackers also exploit phishing emails, often impersonating legitimate companies such as Bandai Namco to lure victims into executing malicious payloads. The malware targets Windows operating systems and multiple browsers, including Chrome and Firefox, to exfiltrate sensitive information.
Data Exfiltration Techniques
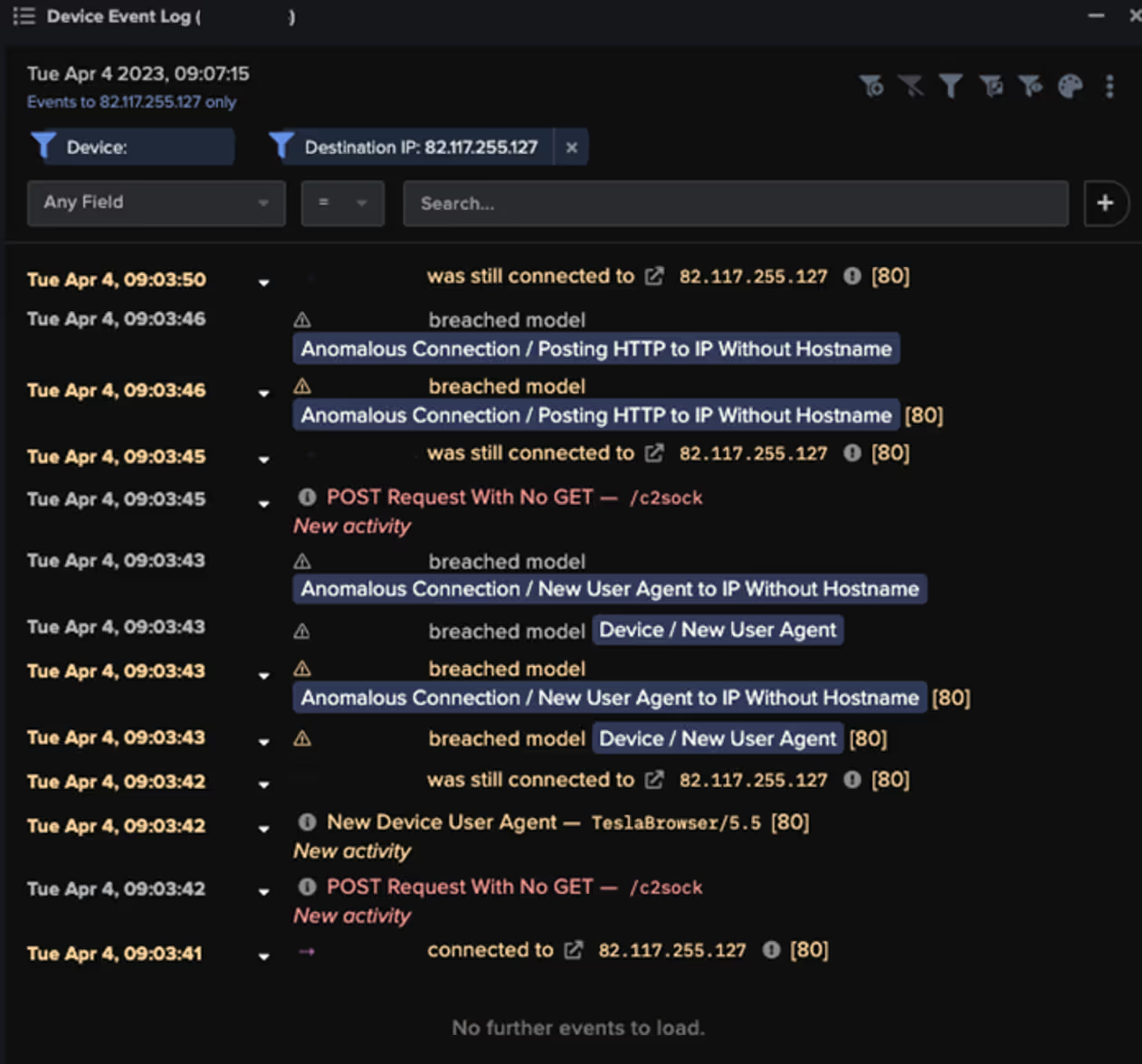
Once Lumma is successfully executed, it employs HTTP POST requests to transmit stolen data to its C2 servers. Darktrace observed various devices infected with Lumma communicating with known C2 infrastructure, revealing a pattern of data exfiltration activities. The malware is capable of accessing and stealing browser data, cookies, and sensitive information from applications like AnyDesk and KeePass.
Evasion Techniques and Defense Recommendations
Lumma employs various evasion techniques to avoid detection by security systems, including using obfuscation and encryption to mask payloads and leveraging trusted binaries like mshta.exe and wscript.exe to execute malicious code. Organizations are urged to adopt advanced security measures, such as Gopher Security's AI-Powered Zero Trust Platform, to enhance their defenses against evolving threats like Lumma.
Future Outlook
As cyber threats become more sophisticated, organizations need to focus on proactive risk management strategies. Gopher Security provides services like Cloud Access Security Broker and AI Inspection Engine for Traffic Monitoring to help businesses detect and respond to such threats effectively.
Explore our services at Gopher Security to safeguard your organization against the rising tide of cyber threats.

