Konfety: New Android Malware Evades Detection with Malformed APKs
Konfety Malware Overview

Image courtesy of Gadget Hacks
The Konfety malware strain is a sophisticated Android threat that employs advanced evasion techniques to avoid detection and analysis. Originating from Russia, the Konfety group has developed a method of ad fraud that leverages an intricate network of legitimate-looking applications to disguise its malicious activities.
Evasion Techniques
The malware's evasion tactics include the use of malformed APK files that disrupt the functionality of security analysis tools. Zimperium researchers found that Konfety manipulates the ZIP structure of APK files, marking files as encrypted even when they are not. This tactic misleads analysis tools, causing them to crash or misinterpret the files, making reverse engineering extremely difficult.
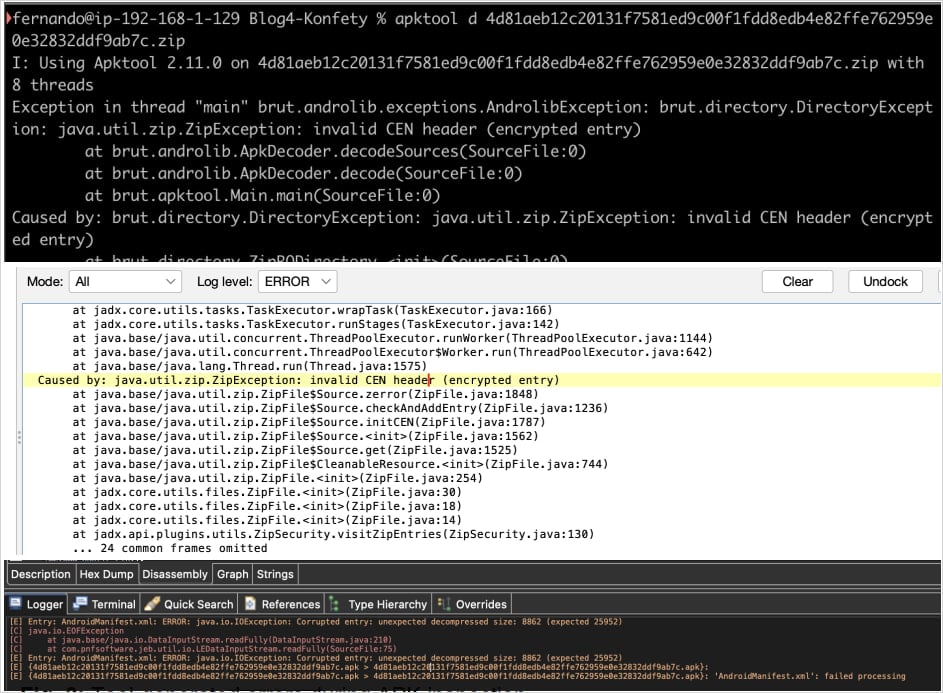
Image courtesy of Zimperium
Additionally, Konfety employs what researchers call “dual-app deception,” where a legitimate app on the Google Play Store coexists with a malicious version distributed through third-party sources. This technique allows the malware to exploit the trust established by its legitimate counterpart.
Functionality of Konfety
Once installed, Konfety can redirect users to malicious websites, push unwanted app installations, and generate spam notifications. It uses the CaramelAds SDK to fetch ads and conduct its activities while exfiltrating sensitive information like the device's installed applications and network configurations.
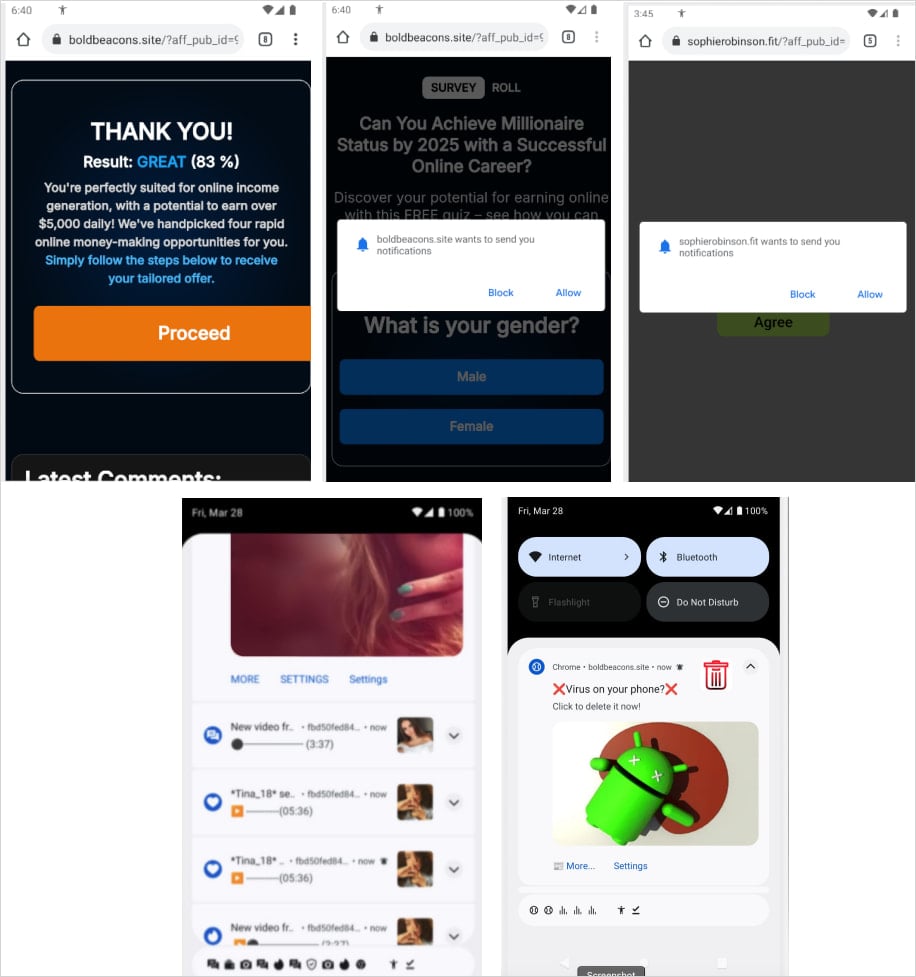
Image courtesy of Zimperium
The malware also hides its app icon and name after installation and utilizes geofencing to modify its behavior based on the victim's location. These methods complicate detection by making it challenging for security tools to identify the malicious activity.
Security Implications
The failure of Google Play Protect to adequately detect Konfety highlights a significant vulnerability in traditional security measures. Research indicates that existing antivirus applications may outperform Google Play Protect in identifying malware. The Konfety malware exploits this weakness by using the same package names as its legitimate twins, effectively masking its malicious behavior.

Image courtesy of TechRadar
The combination of ZIP-level manipulation, dynamic code loading, and infrastructure-based evasion techniques poses a formidable challenge to mobile security. As a result, traditional app store safety advice is becoming increasingly obsolete.
Adaptation of Threat Actors
The ongoing evolution of Konfety demonstrates how rapidly malware can adapt to evade detection methods. Researchers note that the threat actors behind Konfety are consistently altering their tactics to target different ad networks and update their evasion techniques. This adaptability is crucial in maintaining their fraudulent operations, which had peaked at generating 10 billion daily requests.
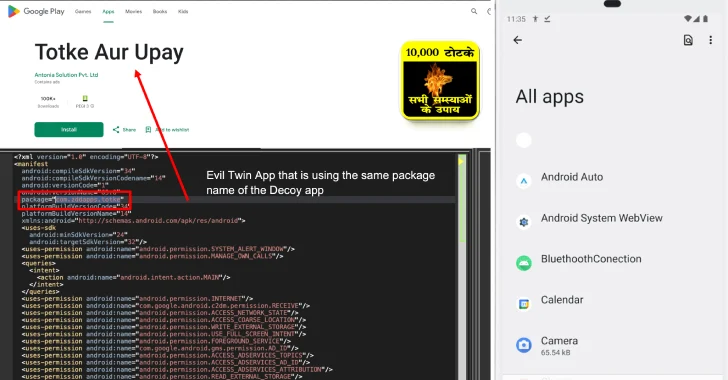
Image courtesy of The Hacker News
Recommendations for Users
To protect against threats like Konfety, users should avoid sideloading apps from third-party stores and ensure that Google Play Protect is enabled. It's crucial to scrutinize app permissions and verify the legitimacy of applications, especially those that appear too good to be true.
For enhanced security, consider using an additional antivirus solution alongside Google Play Protect. Staying informed about the latest security threats and employing a proactive approach to mobile security can help mitigate risks associated with advanced malware like Konfety.
To explore comprehensive mobile security solutions, visit [undefined] and contact us for expert assistance.

