Konfety Android Malware: Evasion Techniques and Threat Analysis
Android Malware Konfety

Image courtesy of Zimperium
A new variant of the Konfety Android malware has emerged, utilizing a malformed ZIP structure and several obfuscation techniques to evade detection and analysis. This malware masquerades as legitimate applications available on Google Play, despite lacking the intended functionalities of these apps.
Malware Capabilities
The Konfety malware can redirect users to malicious websites, initiate unwanted app installs, and generate fake browser notifications. It harnesses the CaramelAds SDK to display hidden advertisements and exfiltrate sensitive information such as installed applications, network configurations, and system details.
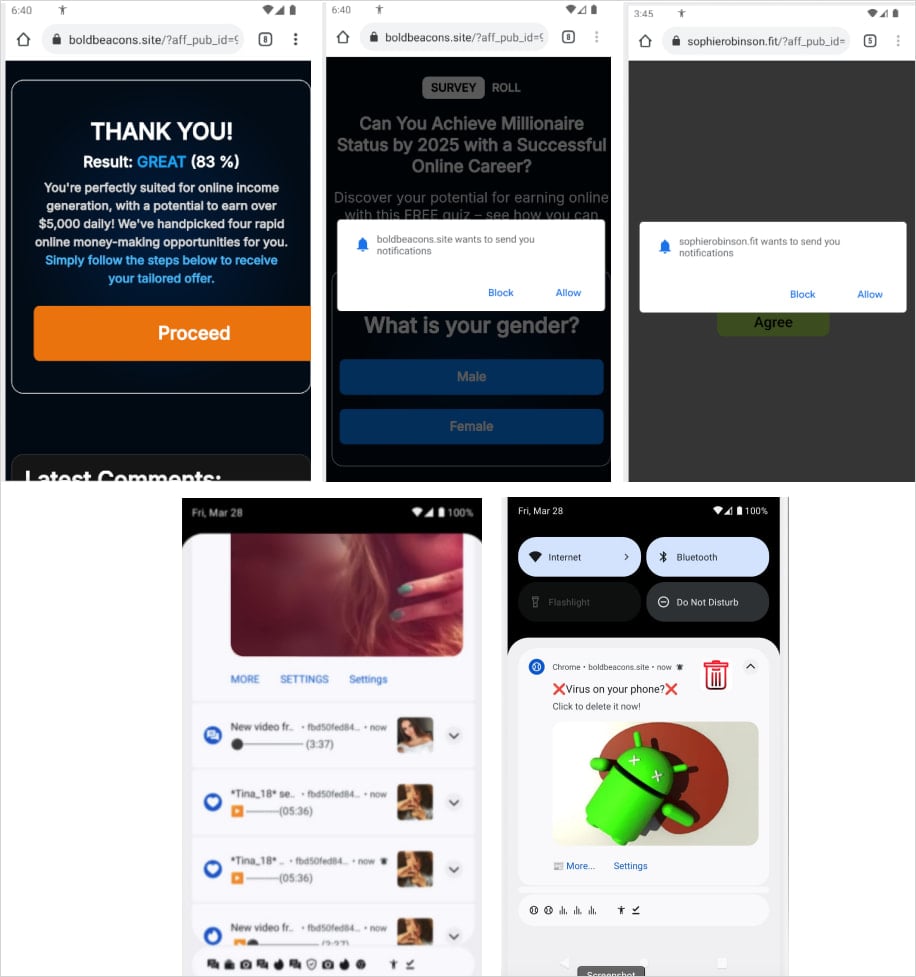
Image courtesy of Zimperium
Although Konfety is not classified as spyware or a remote access tool (RAT), it includes an encrypted secondary DEX file within its APK, which is decrypted and executed at runtime. This file contains clandestine services declared in the AndroidManifest file, enabling the malware to install additional modules dynamically.
Evasion Techniques
Researchers at Zimperium identified several methods employed by Konfety to enhance its evasion tactics:
- Evil Twin Applications: The malware uses branding and names of legitimate apps to trick users into installing it, often distributed through third-party stores.
- Dynamic Code Loading: This technique hides malicious logic in an encrypted DEX file that only gets decrypted and executed during runtime.
- Static Analysis Manipulation: Konfety alters APK files to confuse static analysis tools. For example, it sets the General Purpose Bit Flag to signal encryption, triggering false password prompts that delay or block access to the APK contents.
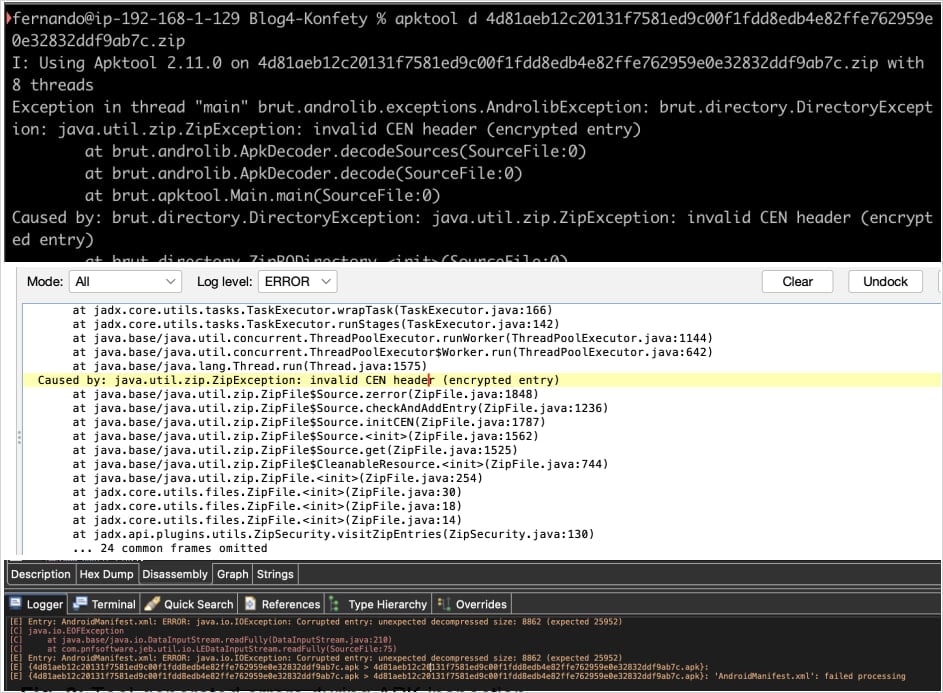
Image courtesy of Zimperium
- APK File Manipulation: Critical files in the APK are declared using unsupported BZIP compression, which is not recognized by many analysis tools, leading to parsing failures. Android's fallback mechanism allows the app to install and run seamlessly on devices.
User Impact
Once installed, Konfety hides its icon and name, employing geofencing to modify its behavior based on the user's location. This malware's ability to redirect users to harmful sites and generate persistent spam notifications poses significant risks to Android users.
Mitigation Strategies
To protect against Konfety and similar threats, it is advisable to:
- Avoid installing APK files from third-party stores.
- Enable Google Play Protect on Android devices for malware scanning.
- Consider additional security measures such as installing reputable Android antivirus applications.
For comprehensive protection against sophisticated malware like Konfety, explore the solutions offered by Gopher Security.
Indicators of Compromise (IOCs)
Zimperium has compiled a list of IOCs for detecting this malware variant. For detailed detection and analysis, refer to the Zimperium repository.
Unsupported Compression Methods in Android Malware
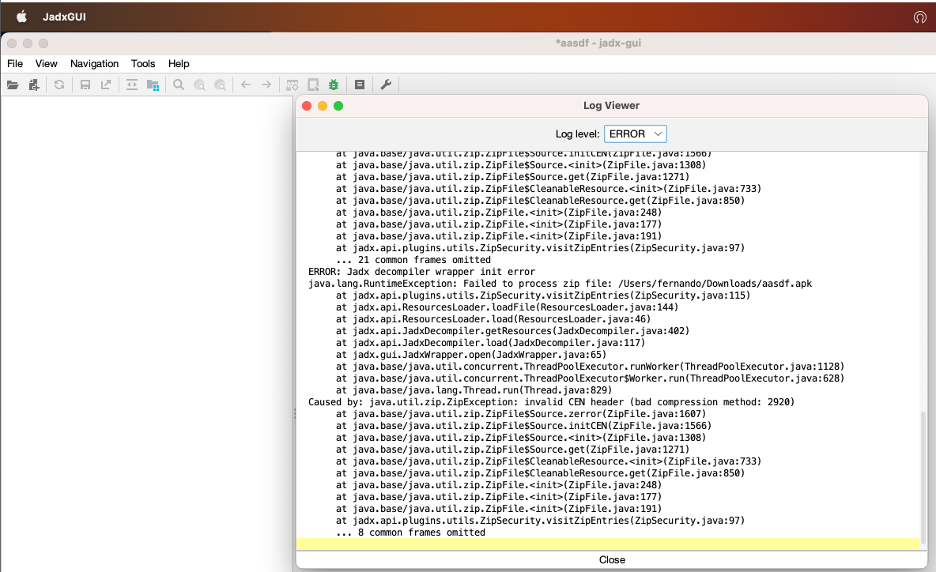
Image courtesy of Zimperium
Research from Zimperium has revealed that 3,300 Android malware samples utilize unsupported compression methods to evade detection. This technique significantly hampers the ability of decompilation tools to analyze these applications.
Techniques Employed
- Unsupported Compression Methods: Android APK files, which are ZIP archives, support only two compression methods: STORED (0x0000) and DEFLATED (0x0008). Malware developers exploit this limitation by using unsupported compression methods, leading to analysis failures in tools like APKTool and JADX.
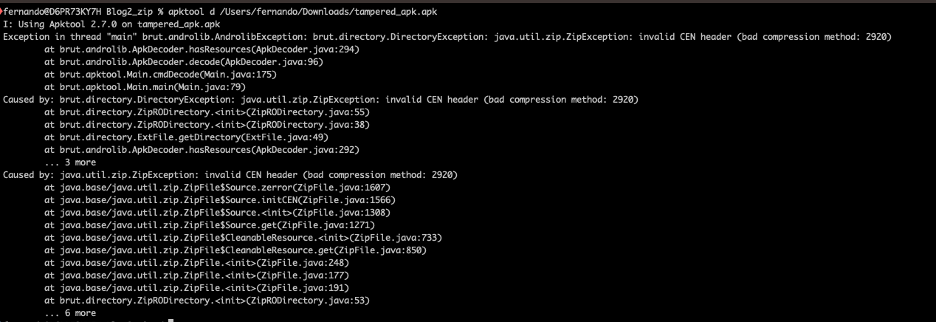
Image courtesy of Zimperium
- File Manipulation: Techniques such as long filenames exceeding 256 bytes can cause crashes in analysis tools. Additionally, malformed AndroidManifest.xml files can prevent correct parsing by these tools.
- Increased Complexity: Malware authors continuously tweak their applications to avoid detection. Many samples are so corrupted that they cannot be loaded by the Android OS, yet 71 malicious samples were identified that can still be executed.
Protection Against Such Threats
Zimperium's solutions, such as Mobile Threat Defense, provide on-device detection to mitigate risks associated with these sophisticated malware tactics.
For a robust defense against Android malware, consider the offerings from Gopher Security.
Explore our services or contact us for more information on how we can help secure your mobile devices.

