Interlock Ransomware Adopts FileFix Attack for Malware Delivery
New FileFix Delivery Method Used to Distribute Interlock RAT
Since at least February 2025, Arctic Wolf has observed the Interlock Remote Access Trojan (RAT) being deployed via social engineering techniques. The DFIR Report recently published a technical analysis of the Interlock RAT being delivered through a method called "FileFix." This method is similar to the previously documented ClickFix technique, which used fake CAPTCHA pages for malware distribution. While Arctic Wolf has not directly encountered FileFix, the findings from The DFIR Report align with their observations of ClickFix intrusions leading to Interlock ransomware as recently as April 2025.

Image courtesy of The DFIR Report
With the ClickFix technique, users are instructed to paste a command into a Run Dialog that downloads and executes malware. FileFix takes a similar approach but instructs users to use the file open dialog instead. This method primarily targets Windows users, though there have been reports of Linux variants as well.
Users should be educated on identifying social engineering techniques to help mitigate potential compromises. Legitimate websites typically do not request that users run commands on their local workstations, especially for CAPTCHA verification.
For further technical insights, refer to the full articles on The DFIR Report and Arctic Wolf.
Campaign Details
The FileFix social engineering attack consists of several steps:
- Victims are instructed to click a button to “Start Verification,” opening Windows File Explorer.
- The site prompts users to press Ctrl + L, selecting the address bar.
- Users are told to press Ctrl + V, pasting a malicious command that was automatically copied to their clipboard when they first navigated to the fake CAPTCHA site.
- The user then hits enter, executing the malicious command on their device.
Observed commands often involve encoded PowerShell scripts that download and execute malware.
Recommendations
- Block Commonly Abused Domains: Domains like trycloudflare.com are frequently exploited by threat actors to host malicious scripts. Organizations should consider blocking such domains at the firewall level.
- Disable the Run Dialog and CMD Execution: Microsoft allows disabling execution of commands via Group Policy or the registry. Users should test these changes before applying them broadly.
- Restrict Execution of Unsigned PowerShell Scripts: Organizations should configure Group Policy to limit PowerShell execution to signed scripts only.
- Implement App Control for Business or AppLocker Policies: These tools can limit the execution of unapproved scripts.
- User Awareness Training: Regular training should be provided to users about the risks of executing commands from untrusted sources.
For more details, visit the Microsoft documentation on Disabling Run Dialog and PowerShell Execution Policies.
Interlock Ransomware Adopts New FileFix Attack to Push Malware
Interlock ransomware operations have surged as hackers employ the FileFix technique to drop a remote access trojan (RAT) on targeted systems. This new method, observed by researchers at The DFIR Report and Proofpoint, leverages compromised websites to deliver payloads through fake CAPTCHA verification.
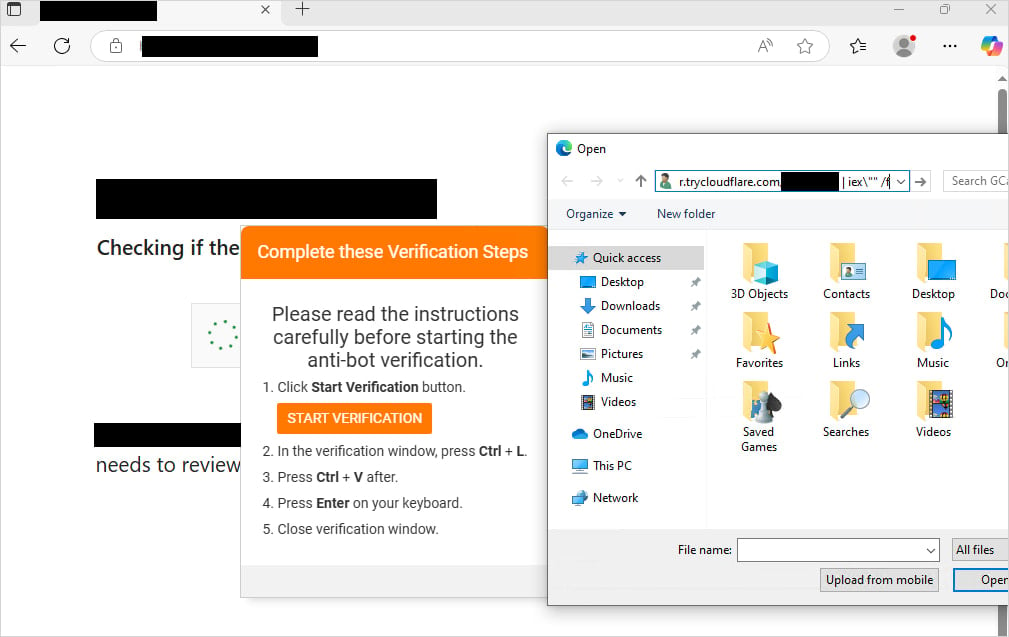
Image courtesy of The DFIR Report
The FileFix technique utilizes trusted Windows UI elements to trick users into executing malicious PowerShell or JavaScript code. The command is disguised as a file path using comment syntax, leading users to execute the command without any visible warning.
The DFIR Report details how the command and control (C2) server can send shell commands for further malicious activities, including lateral movement through remote desktop (RDP).
Interlock ransomware was first launched in September 2024 and has claimed several victims, including Texas Tech University and DaVita. The shift to FileFix indicates an adaptation to stealthier attack methods, enhancing the threat landscape.
For deeper insights, refer to the full articles on The DFIR Report and BleepingComputer.
FileFix Attack: New Social Engineering Threat Explained
Cybersecurity researcher mr.d0x has introduced the FileFix attack as a stealthier evolution of the ClickFix method. This technique exploits Windows File Explorer to execute malicious PowerShell commands and bypasses traditional security measures designed to alert users of potential threats.
The attack begins when victims arrive at a phishing page posing as a file-sharing notification. This approach enables attackers to leverage trusted UI elements while executing commands from browser child processes, complicating detection efforts.
For more information on the attack and its implications, explore resources on CyberPress and BleepingComputer.
New FileFix Attack Exploits Windows File Explorer to Run Malicious Commands
Cybersecurity researcher Mr. D0x has developed FileFix, which exploits Windows File Explorer’s address bar to execute malicious PowerShell commands. This attack method leverages HTML’s file-upload functionality to bypass traditional security warnings.
Image courtesy of CyberPress
The attack utilizes JavaScript to copy a malicious command to the clipboard and open File Explorer. When users paste the command into the address bar, they unknowingly execute the malicious payload while being presented with a deceptive file path.
Given the heightened risk posed by this technique, organizations must monitor unusual command executions from browser processes and educate users about the dangers of executing commands from the address bar.
For additional details on mitigation strategies, refer to Gopher Security, specializing in AI-powered, post-quantum Zero-Trust cybersecurity architecture, which provides solutions to secure environments against evolving threats like FileFix.


