Infostealers Threaten Cybersecurity: Recent Hacks and Insights
Pakistani Freelancers Building Cracking Websites for Stealer-Delivery

Image courtesy of Intrinsec
Key Findings
Information from WhoIs records of cracking websites reveals connections to Pakistani freelancers specializing in web development and advertising. These individuals operate under a pay-per-install model, reminiscent of the Cryptbot malware approach. The nameservers of the domain filescrack.com, registered by these freelancers, have been active since 2021 for over 300 cracking websites. The hosting provider 24xservice is linked to this network, with the range 216.143.0/24 predominantly hosting cracking websites. The geopolitical landscape indicates increased ties between Pakistan and China regarding intelligence sharing, complicating prosecution efforts due to the lack of an extradition treaty between the US and Pakistan. Although servers and domains can be seized, it is a temporary solution as new domains can be quickly established.
For further information, see Intrinsec's report.
Intrinsec’s CTI Services
Organizations face increasingly sophisticated threats, necessitating a proactive approach to threat detection and analysis. Intrinsec's Cyber Threat Intelligence (CTI) service provides contextualized intelligence to help organizations understand and mitigate cyber threats. The CTI team utilizes data from security monitoring services, incident response teams, and custom intelligence generated through heuristics, honeypots, and reverse-engineering.
Services offered include:
- Risk anticipation through operational feeds of Indicators of Compromise (IOCs) and threat intel reports.
- Digital risk monitoring, including data leak detection and remediation, external asset security monitoring, and brand protection.
For more details, visit Intrinsec's CTI services.
Hy-Vee Hacked: Infostealers Enable Stormous Group's 53GB Atlassian Data Heist
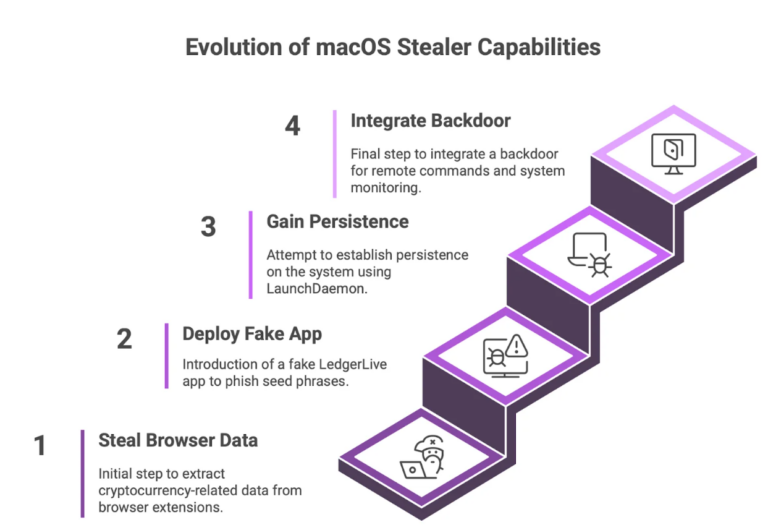
Image courtesy of InfoStealers
Hy-Vee, a major U.S. supermarket chain, was targeted in a significant data breach by the Stormous ransomware group. The attackers accessed Hy-Vee’s Atlassian accounts, specifically Confluence and Jira, using stolen credentials traced back to various Infostealer infections among Hy-Vee employees.
For detailed insights, refer to Atomic macOS Stealer now includes a backdoor for persistent access.
Infostealer Malware Threats
Rising Threats
Cybersecurity researchers have discovered datasets containing 16 billion login credentials across major platforms like Apple, Facebook, and Google, raising alarms about the prevalence of infostealer malware. This malware extracts sensitive data from devices, including usernames, passwords, and credit card information. Volodymyr Diachenko from SecurityDiscovery emphasizes the immediate threat: “Someone, somewhere is having data exfiltrated from their machines as we speak.”
Image courtesy of CNBC
The datasets were found indexed online without password protection, making them vulnerable to exploitation. The rise of advanced evasion techniques in modern infostealers has made detection increasingly challenging, contributing to a surge in high-profile attacks, such as a malicious campaign disclosed by Microsoft Threat Intelligence affecting nearly 1 million devices globally.
For additional context, see Cybernews report.
Mitigation Strategies
To combat the growing threat of infostealers, individuals are advised to:
- Regularly update passwords and employ multi-factor authentication.
- Be vigilant against malware hidden in illegitimate software.
- Organizations should adopt a zero-trust architecture to authenticate users and devices continuously.
Government initiatives have also intensified, with Europol collaborating with Microsoft to disrupt major infostealer threats, such as Lumma.
For comprehensive strategies, visit Palo Alto Networks.
SOC Threat Radar — July 2025

Image courtesy of Barracuda
Recent data from Barracuda Managed XDR indicates significant developments:
- A 35% rise in infostealer detections.
- A 56% increase in threats targeting Linux servers.
- A 13% uptick in suspicious logins for AWS consoles.
Infostealer Attacks
The rise in infostealer attacks correlates with credential theft, session hijacking, and cyber espionage. Notably, Interpol has taken down numerous IPs linked to various infostealer variants.
Linux Server Threats
Linux servers are increasingly targeted due to unpatched vulnerabilities. Organizations should ensure security patches are applied and implement robust backup and recovery plans.
AWS Console Logins
Unauthorized attempts to access AWS Management Consoles have risen, necessitating strong password policies and continuous monitoring for unusual activity.
For further insights, review the full analysis on Barracuda's blog.
For more information about how we can help your organization, please contact undefined, or visit undefined.

