GLOBAL GROUP RaaS Introduces AI-Powered Negotiation Features
GLOBAL GROUP RaaS Adds AI-Powered Negotiation Feature for Ransom Demands
A newly surfaced Ransomware-as-a-Service operation, dubbed GLOBAL GROUP, has begun deploying an AI‐driven negotiation tool that elevates the psychological pressure on victims and streamlines extortion workflows for affiliates. Security researchers at EclecticIQ first identified GLOBAL GROUP’s activity in early June on the Ramp4u underground forum, where the threat actor known as “$$$” shared an onion link to a dedicated leak site and touted a forthcoming full-service RaaS platform.

Image courtesy of EclecticIQ
Subsequent analysis suggests that GLOBAL GROUP represents a rebranding of the Black Lock RaaS operation, itself the successor to the now-defunct Mamona ransomware, all under the direction of the same actor. GLOBAL GROUP’s infrastructure relies heavily on Initial Access Brokers (IABs) who sell footholds in high-value corporate networks.
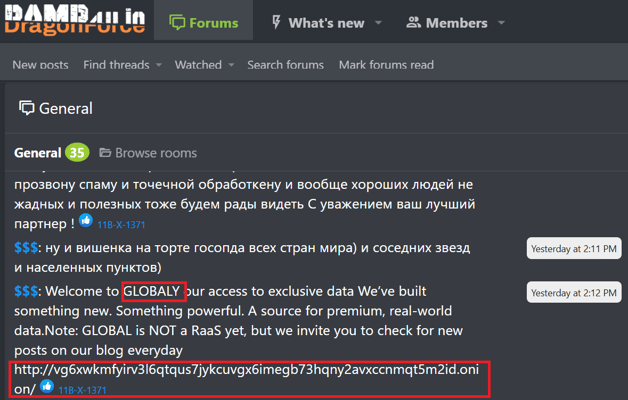
Image courtesy of GBHackers
These brokers provide remote access via compromised VPN appliances—most notably Fortinet, Palo Alto, and Cisco—alongside webshells for SAP NetWeaver environments and brute-force access to Microsoft Outlook Web Access and RDWeb portals. Once an affiliate secures entry, they deploy customized ransomware payloads that take advantage of chaos and speed to maximize damage before traditional endpoint defenses can react.
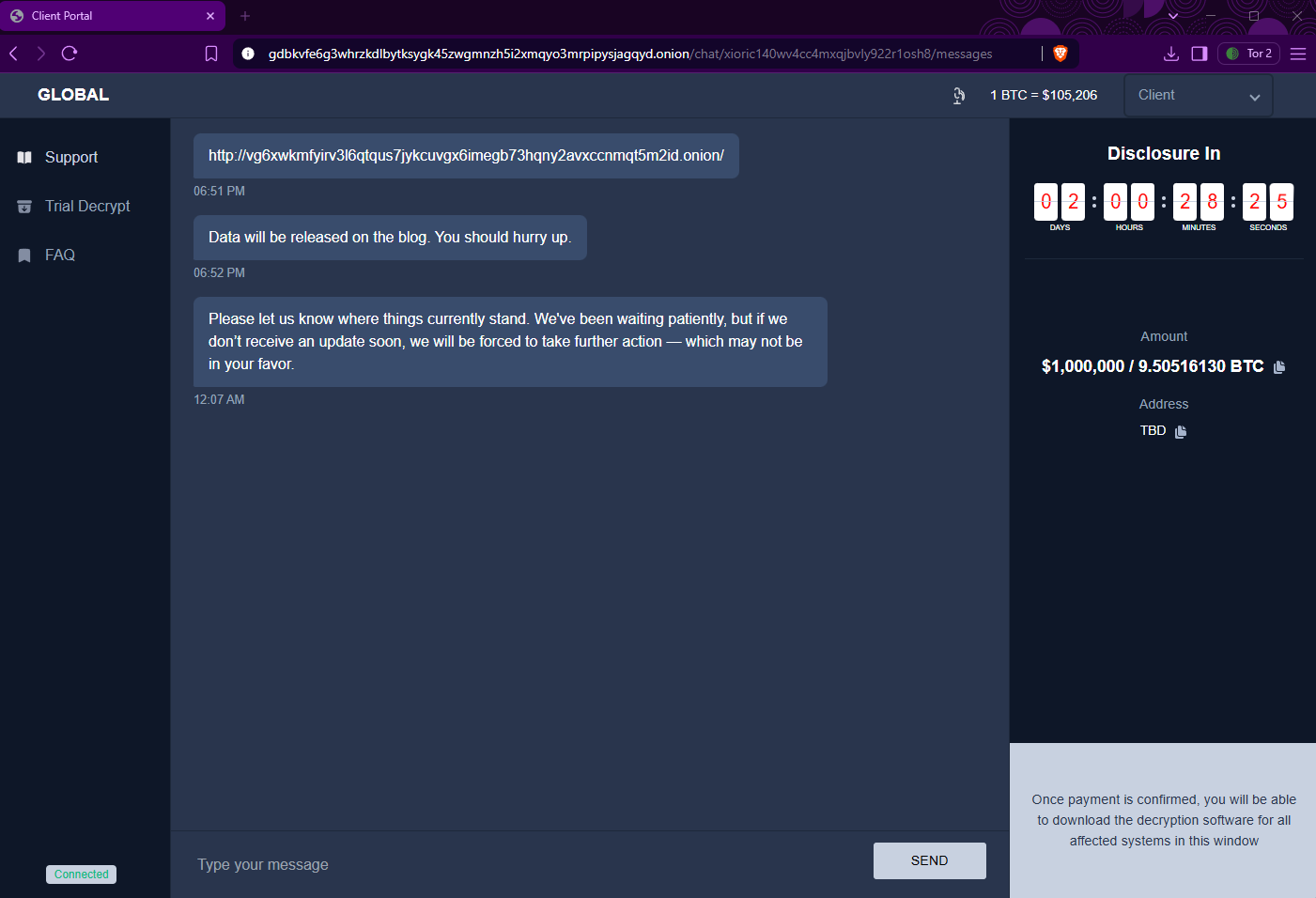
The group’s new negotiation system is powered by bespoke AI chatbots that guide victims through a scripted extortion dialogue. Affiliates select from multiple language options, ensuring non-English-speaking criminals can interact with their targets as fluently as native speakers. Once engaged, the AI progressively tightens the time pressure, threatening data leaks and public shaming if victims delay. According to EclecticIQ, some victims have been presented with seven-figure demands—commonly exceeding one million U.S. dollars for decryption keys—and given as little as 48 hours to respond.
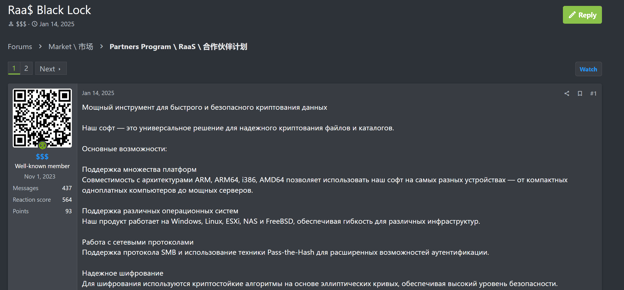
Image courtesy of GBHackers
Behind the scenes, GLOBAL GROUP’s leak site exposes compromised data sets belonging to healthcare providers in the United States and Australia, an industrial machinery firm in the United Kingdom, and other targets in regions such as Brazil. Researchers traced the site’s real IP to a Russia-based VPS provider long associated with Mamona’s operations, confirming the threat actor’s identity through repeated infrastructure reuse and operational security lapses.

Image courtesy of GBHackers
Affiliates of GLOBAL GROUP are promised an 80 to 85 percent share of ransom payments, a model designed to lure seasoned cybercriminals away from rival RaaS offerings. The platform’s affiliate dashboard allows operators to build cross-platform payloads for Windows, Linux, ESXi, and BSD, to configure encryption flags, and to initiate automated domain-wide deployments using SMB and malicious Windows services. This degree of customization, paired with the AI negotiation interface, signals a maturation of the RaaS market into a competitive “service economy” for cybercrime.
While law enforcement and cybersecurity firms increase pressure on ransomware syndicates, GLOBAL GROUP’s rapid victim accrual and seven-figure extortion demands illustrate that RaaS operations remain resilient and are now leveraging artificial intelligence to sustain and scale their profits. Continued monitoring of GLOBAL GROUP’s evolving tactics will be critical to developing more robust defensive strategies and disrupting the affiliate networks that fuel these sophisticated ransomware campaigns.
GLOBAL GROUP: Emerging Ransomware-as-a-Service, Supporting AI Driven Negotiation
On June 2, 2025, EclecticIQ analysts observed the emergence of GLOBAL GROUP, a new Ransomware-as-a-Service (RaaS) brand promoted on the Ramp4u forum by the threat actor known as “$$$”. The same actor controls the Black Lock RaaS and previously managed Mamona ransomware operations. GLOBAL GROUP targets a wide range of sectors across the United States and Europe.
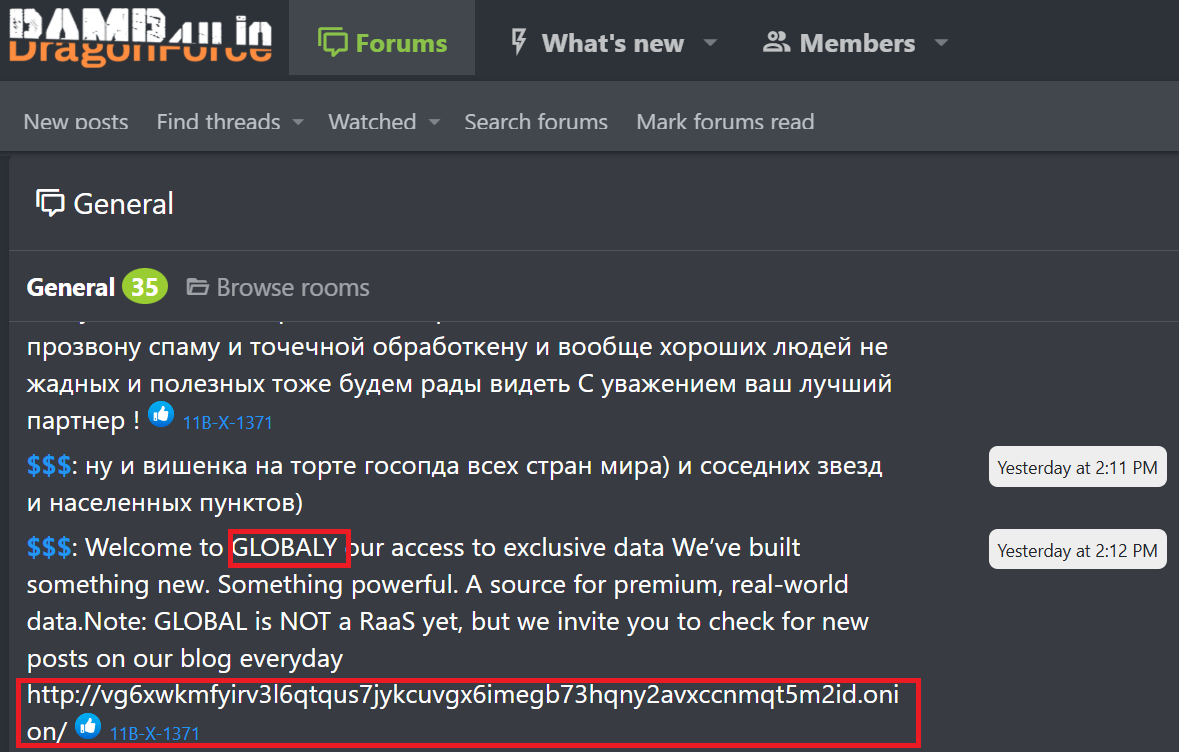
Image courtesy of EclecticIQ
EclecticIQ assesses with medium confidence that GLOBAL GROUP was likely established as a rebranding of the BlackLock RaaS operation. This rebranding aims to rebuild trust and expand the affiliate network by giving 80% of extorted ransom money to affiliates. GLOBAL GROUP operates a dedicated leak site (DLS) on the Tor network, and analysts traced the real IP address of the DLS to a Russia-based VPS provider called IpServer, previously used by the Mamona RaaS gang. The site already lists confirmed victims, including healthcare providers in the United States and Australia, and an automotive services firm in the United Kingdom.
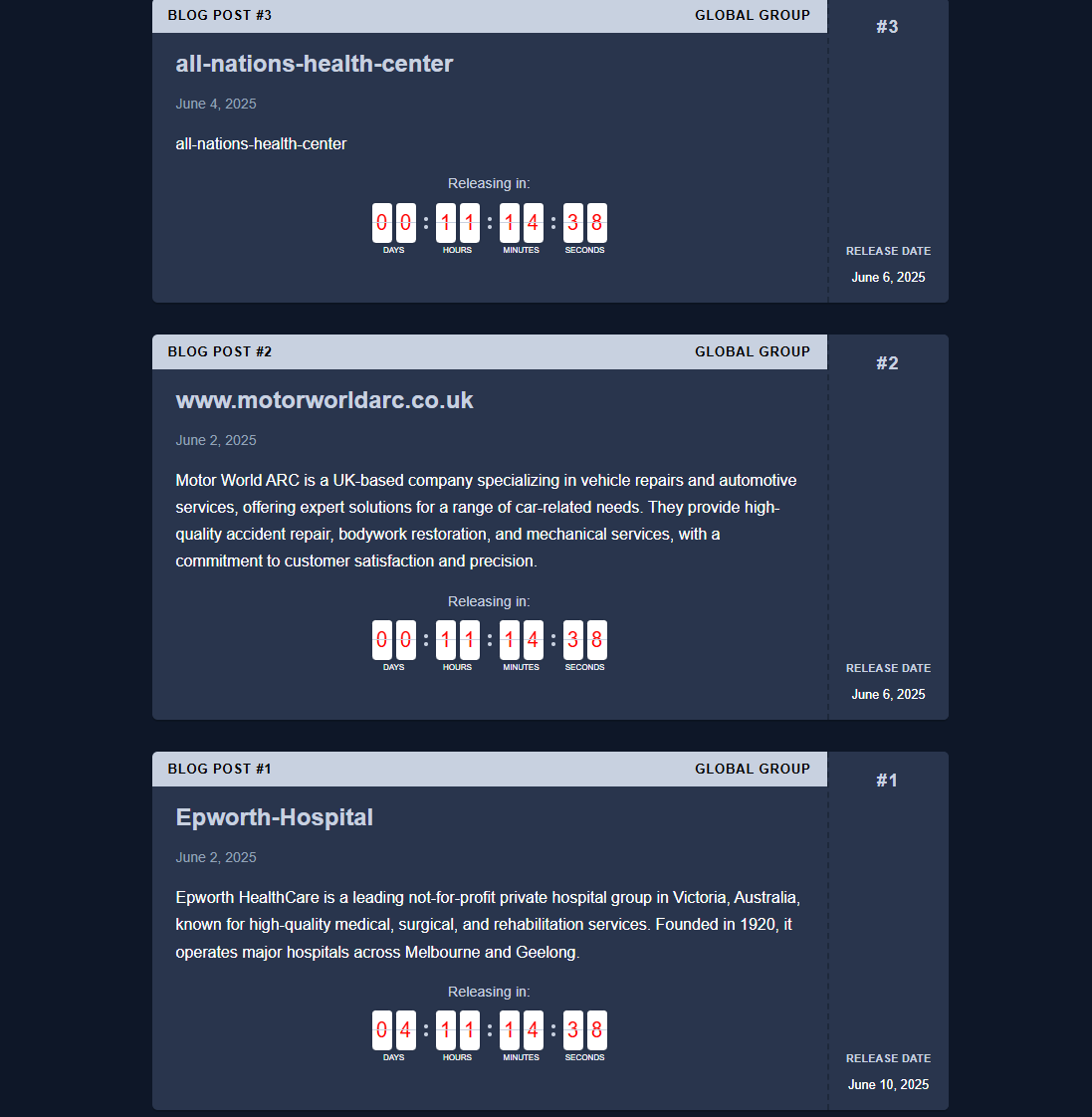
Image courtesy of EclecticIQ
GLOBAL GROUP heavily relies on Initial Access Brokers (IABs) to acquire access to vulnerable edge appliances, including those from Fortinet, Palo Alto, and Cisco. The group also uses brute-force tools for Microsoft Outlook and RDWeb portals, enabling high-privilege initial access and rapid ransomware deployment, often bypassing traditional EDR solutions.
Analysts also observed that GLOBAL GROUP’s ransom negotiation panel features an automated system powered by AI-driven chatbots, allowing effective engagement with victims, particularly for non-English-speaking affiliates. The AI-driven negotiation functionality increases psychological pressure during negotiations, facilitating seven-figure ransom demands for decryption keys.
OPSEC Failure and Shared Malware Mutex Links GLOBAL GROUP to Previous Mamona Operations
Analysts assess with high confidence that the same actor operating under the persona '$$$' behind GLOBAL GROUP was also responsible for the now-defunct Mamona RIP ransomware operation. Analysts observed shared infrastructure evidence that links both operations, revealing the same Russian VPS provider called IpServer.
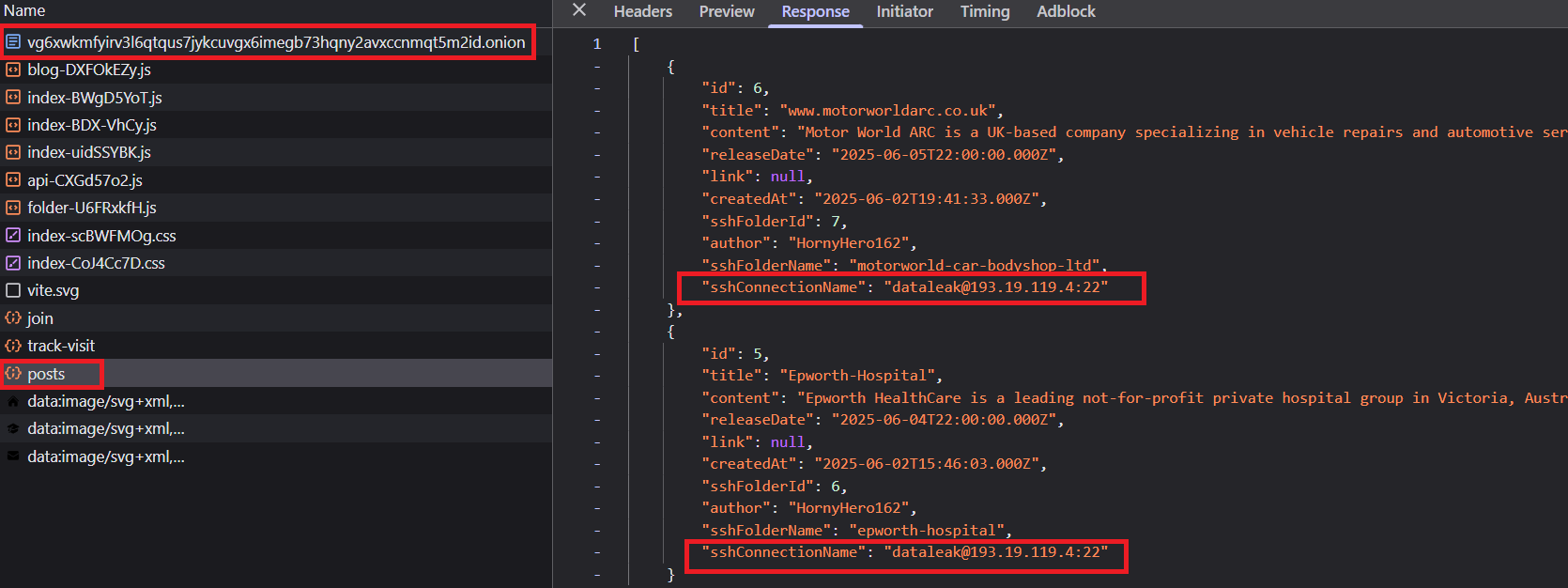
Image courtesy of EclecticIQ
Analysis of the GLOBAL ransomware sample confirms the group uses a customized variant of Mamona ransomware. Both malware strains utilize the identical mutex key Global\\Fxo16jmdgujs437. Unlike Mamona Ransomware, GLOBAL includes added functionality for automated domain-wide ransomware installation, employing SMB connections and malicious Windows service creation for scalable deployment.
On June 7, 2025, a VirusTotal user uploaded a Golang-compiled variant of the GLOBAL ransomware, built in the Go programming language. This variant leverages a modern encryption routine, allowing it to encrypt large volumes of data in minutes across multiple operating systems.
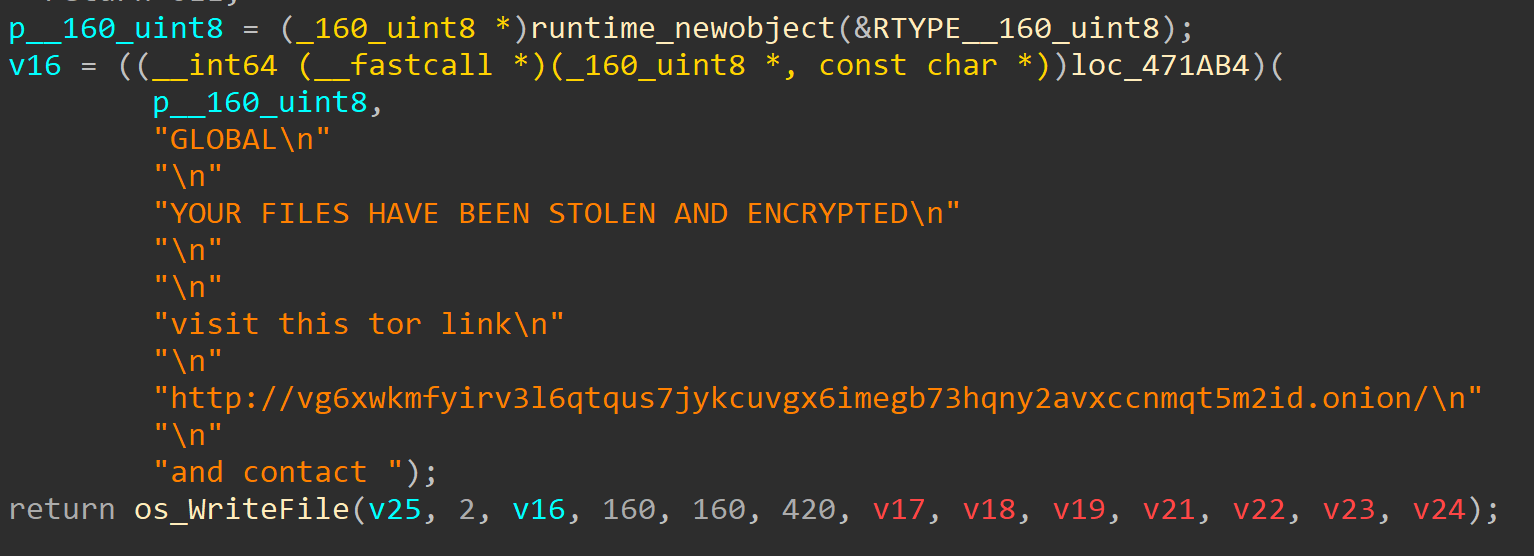
Image courtesy of EclecticIQ
GLOBAL GROUP Markets RaaS Platform with 85% Revenue Share
GLOBAL GROUP hosts promotional content showcasing a fully featured Ransomware-as-a-Service (RaaS) platform with a negotiation portal and an affiliation panel. Analysts assess that this promotional material aims to attract new affiliates by highlighting a competitive revenue-sharing model of 85%.
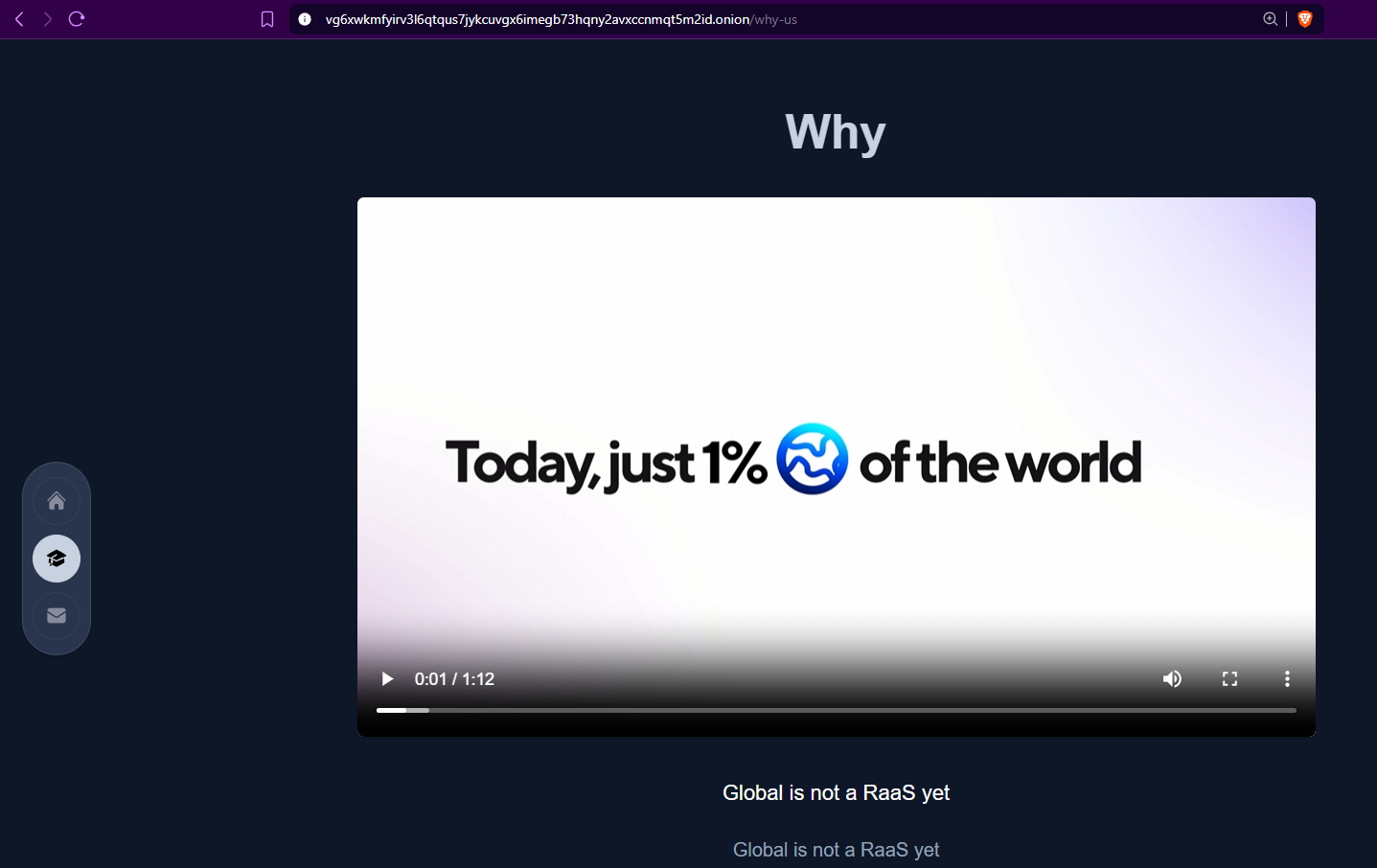
Image courtesy of EclecticIQ
The affiliate panel allows cybercriminals to manage victims, build ransomware payloads, and monitor operations. It supports cross-platform ransomware builds for ESXi, NAS, BSD, and Windows OS. The platform also promotes AI-powered negotiation to improve workflows.
Victims are directed to initiate negotiations via a dedicated Tor-based portal, which showcases a mature extortion ecosystem with automated victim onboarding via a custom chat interface on the Tor network.
*Image courtesy of [EclecticIQ](https://blog.eclecticiq.com/global-group-emerging-ransomware

