FBI Warns: Millions of Devices Infected by BadBox 2.0 Malware
Millions of Devices Infected by Badbox 2.0 Botnet

Image courtesy of Bleeping Computer
Over 1 million Internet-connected devices, including smart TVs, streaming boxes, and IoT devices, are infected with the Badbox 2.0 malware, according to the FBI. This malware turns consumer electronics into residential proxies for malicious activities. The botnet primarily affects devices manufactured in China, with widespread distribution across 222 countries, particularly in Brazil, the U.S., and Mexico.
The FBI warns that these devices often come preloaded with malware or become infected during firmware updates or through malicious apps from unofficial marketplaces. The malware allows cybercriminals to gain unauthorized access to home networks, facilitating activities such as ad fraud and credential stuffing.
Characteristics of Badbox 2.0
The Badbox 2.0 malware utilizes various methods to infect devices. These include:
- Pre-installed Malware: Devices may come with the Badbox 2.0 botnet embedded, particularly cheaper off-brand devices.
- Malicious Firmware Updates: Devices may be compromised during the setup process if they download harmful applications or updates.
- Exploitation of Unofficial App Stores: Apps that seem legitimate can harbor malware, which may not be present in versions found on Google Play.
Indicators of a Badbox 2.0 infection can include unexpected app marketplaces, requests to disable Google Play Protect, and excessive data usage. For more information on identifying compromised devices, see FBI PSA.
Devices Affected
Devices affected by Badbox 2.0 include:
- Smart TVs
- Streaming devices
- Digital projectors
- Aftermarket vehicle infotainment systems
- Digital photo frames
The FBI notes that many infected devices are generic, low-cost models that often lack proper certification, making them more susceptible to malware. If you've purchased devices from unrecognizable brands or at incredibly low prices, they could be infected.
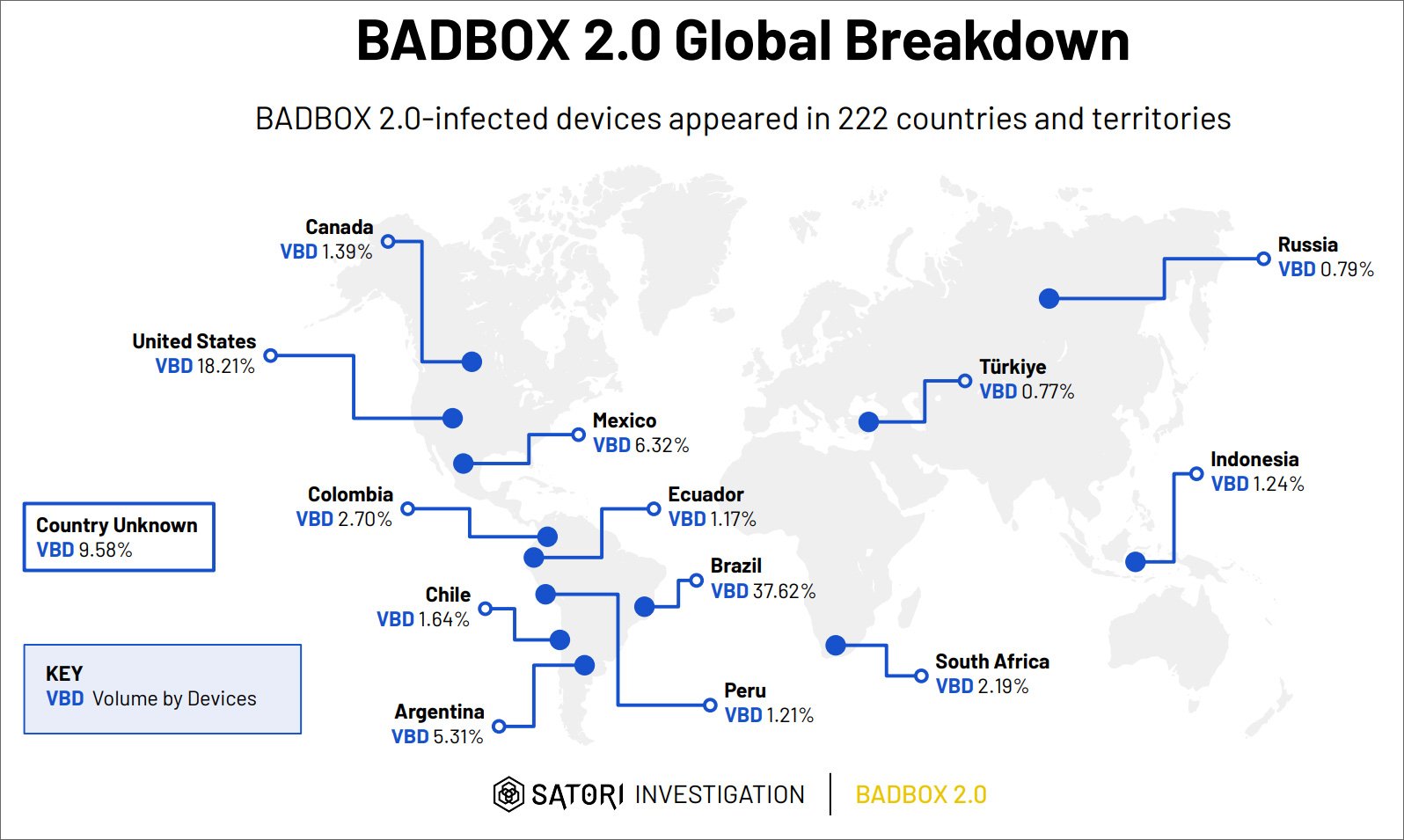
Image courtesy of Bleeping Computer
Recommendations for Protection
To protect against the Badbox 2.0 malware, the FBI recommends the following actions:
- Assess IoT Devices: Regularly evaluate all devices connected to your home network for suspicious activity.
- Update Software: Keep all operating systems, applications, and firmware updated to minimize exposure to vulnerabilities.
- Avoid Unofficial Apps: Do not download applications from unofficial sources that promise free content, as they may contain malware.
- Monitor Network Traffic: Keep an eye on unusual data usage patterns from your devices.
If you suspect your device is compromised, disconnect it from the internet and report the incident to the Internet Crime Complaint Center (IC3).
By staying informed and vigilant, consumers can better safeguard their devices from threats like Badbox 2.0. For comprehensive security solutions, consider exploring our services at undefined, [company url: undefined]. Stay protected with the right cybersecurity measures.

