Exploring AsyncRAT: The Evolution and Impact of Remote Access Trojans
AsyncRAT Overview and Variants
AsyncRAT is an open-source remote access trojan that emerged on GitHub in 2019. Its design incorporates a variety of typical RAT capabilities, including keylogging, screen capture, and credential theft. The simplicity and open-source nature of AsyncRAT have made it particularly attractive to cybercriminals, resulting in its widespread use in various cyberattacks. Over time, AsyncRAT has evolved into a fundamental component of modern malware, generating numerous variants and forks that enhance its functionality.
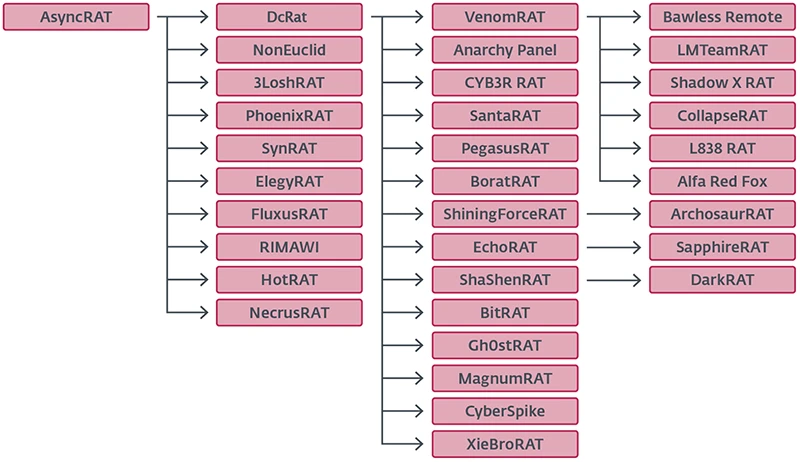
Image courtesy of Help Net Security
Evolution of AsyncRAT
ESET Research has analyzed the evolution of AsyncRAT, detailing how its modular architecture and improved stealth features contribute to its adaptability in modern threat environments. According to ESET researcher Nikola Knežević, “AsyncRAT introduced significant improvements, particularly in its modular architecture and enhanced stealth features, making it more adaptable and harder to detect in modern threat environments.”
The most popular forks include DcRat, VenomRAT, and SilverRAT. DcRat expands the feature set of AsyncRAT considerably, while VenomRAT enhances capabilities even further. Some less serious forks, such as SantaRAT and BoratRAT, were created as jokes but have been observed in actual attacks.
For a deeper analysis of AsyncRAT variations, see ESET’s detailed report.
AsyncRAT Forks and Their Features
The diverse landscape of AsyncRAT forks presents unique characteristics and functions. ESET's telemetry shows that DcRat accounts for 24% of unique sample infections, while VenomRAT follows with 8%. This indicates the prevalence of these variants in active cyberattacks.
Notable Variants
- DcRat: Enhances AsyncRAT’s features, utilizing MessagePack for efficient data serialization. It implements evasive techniques such as AMSI and ETW patching, blocking detection mechanisms and terminating processes on a denylist.
- VenomRAT: Offers an extensive feature set, functioning almost independently from its predecessor. It integrates multiple plugins directly into the client, which reduces reliance on external modules.
- SantaRAT and BoratRAT: These forks are more novelty than serious threats, highlighting the range of AsyncRAT's evolution.

Image courtesy of ESET
Identifying AsyncRAT Variants
Identifying the various forks of AsyncRAT relies on analyzing configuration settings and values within the malware's code. Most samples contain a Version field that identifies the specific fork, which is usually encrypted using AES-256. If this field is absent, other clues may be found in the Salt values or embedded certificates.
ESET’s research provides methodologies for identifying AsyncRAT servers, including sending crafted packets to C&C servers. Further insights can be derived from the malware’s code structure and functionality.
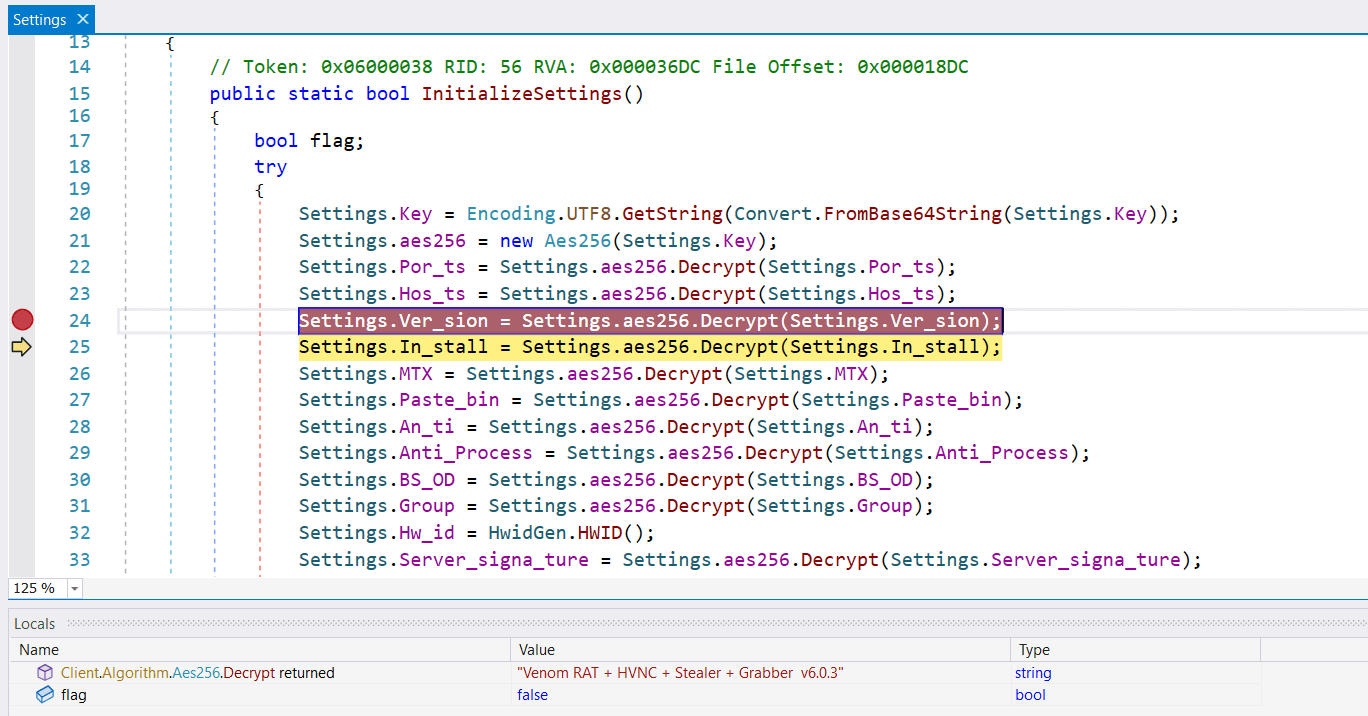
Image courtesy of ESET
Lesser-Known Variants and Their Capabilities
Less common AsyncRAT forks continue to emerge, each with unique plugins that extend functionality beyond the original RAT capabilities. Some noteworthy examples include:
- NonEuclid RAT: Features plugins such as WormUsb.dll, which targets PE files for infection, and Brute.dll, which brute forces SSH and FTP.
- JasonRAT: Displays odd naming conventions and employs Morse code for string obfuscation.
- XieBroRAT: Targets browser credentials and provides interaction with Cobalt Strike servers.
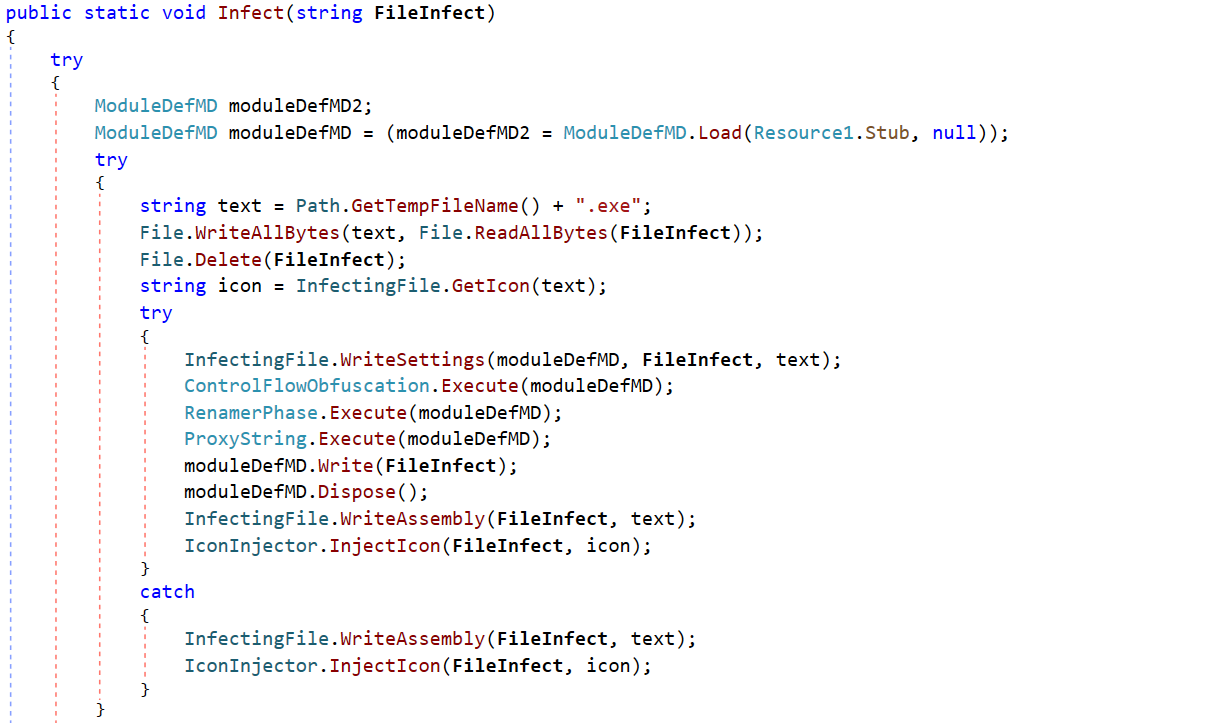
Image courtesy of ESET
Conclusion
The pervasive nature of AsyncRAT and its forks highlights the challenges in cybersecurity. The open-source framework lowers the barrier for aspiring cybercriminals, enabling the rapid development and deployment of sophisticated malware. As threats evolve, proactive detection strategies and behavioral analysis will be critical in combating emerging risks.
For more information on malware threats and how to protect against them, visit our website at Gopher Security.
Explore our services or contact us for assistance in safeguarding your digital assets.

