Enhancing Cybersecurity with ThreatLocker's Zero Trust Solutions
ThreatLocker Network Control
ThreatLocker Network Control is an advanced endpoint firewall solution that provides comprehensive management over network traffic. This tool is designed to protect devices and data from cyber threats by employing custom-built policies that dictate network access based on various criteria such as IP addresses, keywords, and authentication methods. The solution allows for granular control over network access, which is critical for organizations adapting to a landscape where remote work blurs traditional network perimeters.
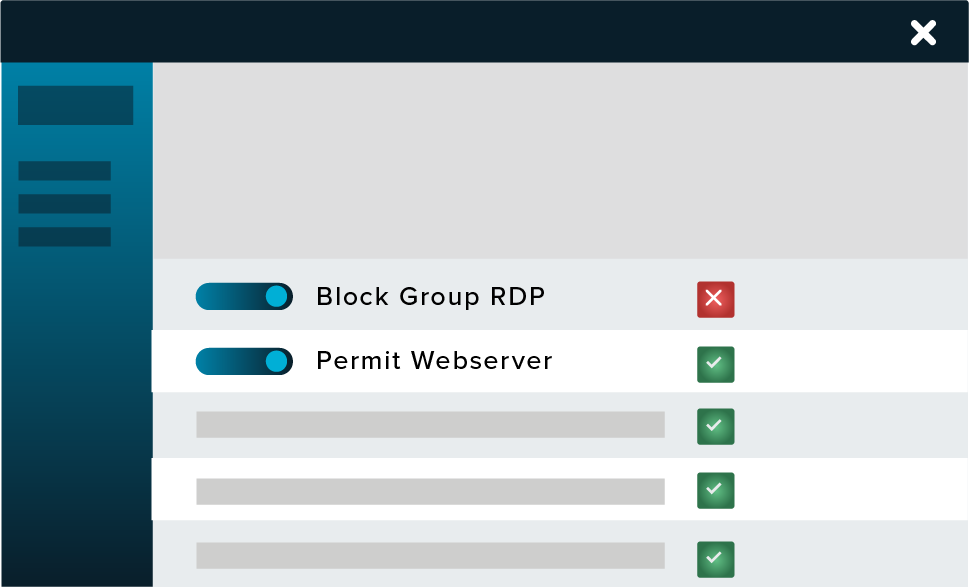
Image courtesy of ThreatLocker
How ThreatLocker Network Control Works
ThreatLocker employs dynamic access control lists (ACLs) to manage firewall policies effectively across all devices. Unlike traditional firewalls that require manual updates for changing locations or conditions, ThreatLocker automatically adjusts access permissions based on real-time data. Authorized devices can open ports on demand, which will close automatically after five minutes of inactivity. Unauthorized devices are unable to connect or even detect these open ports.
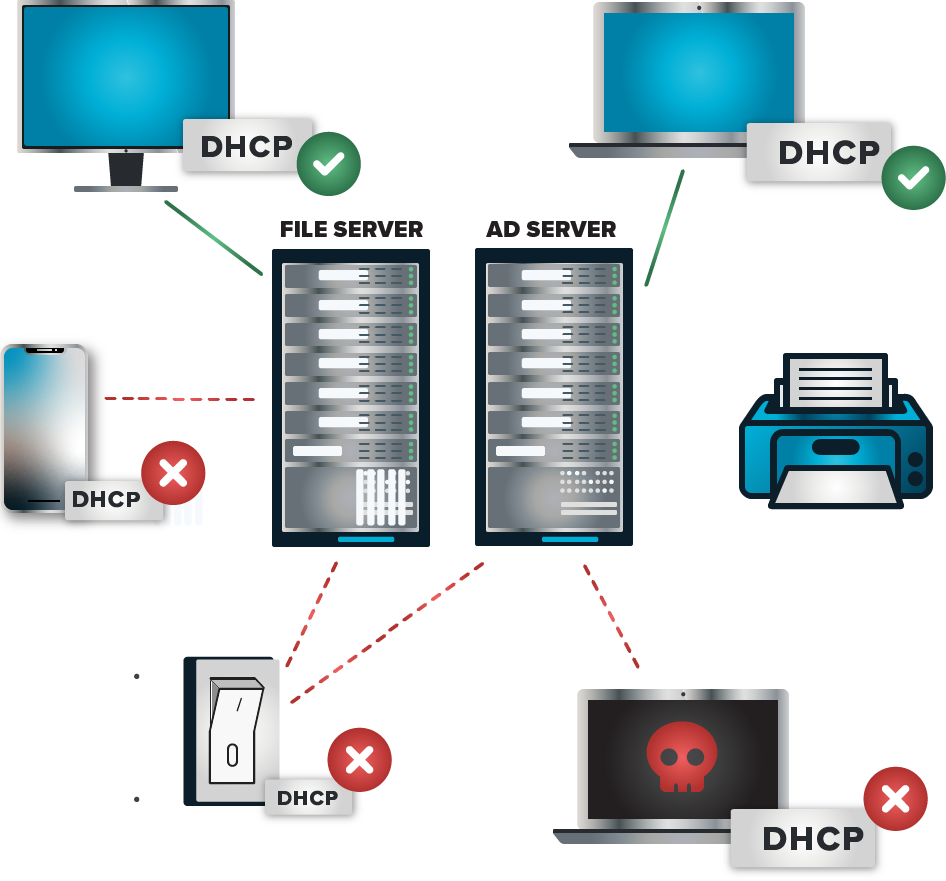
Image courtesy of ThreatLocker
Integration and Compatibility
ThreatLocker Network Control can operate alongside or replace traditional VPNs, depending on the organization's needs. It also coexists with Windows Firewall, providing an additional layer of security without disabling existing protections. This flexibility allows organizations to tailor their security strategies based on their unique operational requirements.
Key Features of ThreatLocker Network Control
- Centralized Management: Control all endpoints from a single platform, simplifying security operations.
- Dynamic Policies: Utilize dynamic ACLs to adjust network access without user intervention.
- Enhanced Security: Protect against unauthorized access while ensuring legitimate traffic can flow freely.
- Compliance Ready: Support compliance with standards like NIST, HIPAA, and PCI by implementing strict access controls.
For detailed information on how ThreatLocker can enhance your organization's cybersecurity posture, visit ThreatLocker’s Network Control.
Embracing Zero Trust with ThreatLocker
The Zero Trust model is increasingly important in today's cybersecurity landscape, where traditional perimeter defenses are no longer sufficient. ThreatLocker’s Network Control embodies this philosophy by ensuring that all devices and users must be verified before being allowed access to network resources.

Image courtesy of TechHQ
Challenges in Zero Trust Adoption
Despite the advantages of Zero Trust, many organizations face hurdles in its implementation. These include budget constraints, reliance on existing skills, and fears regarding the complexity of deployment. According to a survey, over a third of companies have yet to adopt Zero Trust strategies, indicating a significant gap that needs to be addressed.
Simplifying Zero Trust Implementation
ThreatLocker’s Network Control simplifies the adoption of Zero Trust by providing a user-friendly interface and necessary tools to manage endpoint security effectively. This solution allows organizations to transition from a perimeter-based security model to a comprehensive, continuous authentication framework.
By leveraging ThreatLocker, businesses gain complete control over network access, ensuring that only authorized devices can communicate with sensitive resources. This proactive approach mitigates the risks associated with cyber threats, allowing organizations to maintain a robust cybersecurity posture.
For more information about the Zero Trust model and how ThreatLocker can assist, refer to Embracing Zero Trust.
New Cybersecurity Solutions from ThreatLocker
At the Zero Trust World 2025 event, ThreatLocker announced several new cybersecurity solutions aimed at enhancing the efficiency and effectiveness of their platform. These innovations are designed to meet the growing demand for user-friendly and cost-effective security measures.

Image courtesy of Cyber Risk Leaders
Key Innovations
- ThreatLocker Insights: This tool provides real-time, actionable insights from millions of endpoints, enabling cybersecurity professionals to make informed decisions quickly.
- ThreatLocker Patch Management: Streamlines the software update process by consolidating alerts and ensuring safe deployments through rigorous testing.
- ThreatLocker User Store: A catalog of pre-approved applications that allows users to run necessary tools without compromising security.
- ThreatLocker Web Control: Simplifies web access management and enhances user experience by dynamically updating website categories.
- ThreatLocker Cloud Control: Protects Microsoft 365 tenants from phishing and token theft by validating connections from trusted networks.
- ThreatLocker Detect Dashboard: Provides an intuitive layout for monitoring incidents, facilitating quick responses based on detailed recommendations.
These solutions make cybersecurity management more straightforward and efficient, allowing organizations to focus on their core operations without compromising security.
For further details on ThreatLocker’s latest offerings, visit ThreatLocker Debuts New Cyber Security Solutions.
Call to Action
Explore how ThreatLocker can transform your organization's cybersecurity strategy. Visit ThreatLocker to learn more about our innovative solutions and request a demo today.

