Emerging Cyber Risks for Financial Firms: Supply Chains & Security
Financial Cybersecurity Risks
Vendor Vulnerabilities
Financial institutions are increasing their defenses against direct cyberattacks; however, third-party risks from vendors remain a significant threat. According to Black Kite’s report, while financial organizations are improving their security measures, many vendors do not meet the same standards. This discrepancy exposes banks and insurers to potential breaches through their vendors. Ferhat Dikbiyik, Chief Research and Intelligence Officer at Black Kite, emphasized the necessity for addressing these third-party vulnerabilities. Attackers are increasingly targeting vendors, which serve as potential entry points into financial organizations. The report reveals alarming statistics: 92% of vendors assessed received low grades in information disclosure risk, and 65% lack adequate patch management, leaving them vulnerable to exploits.
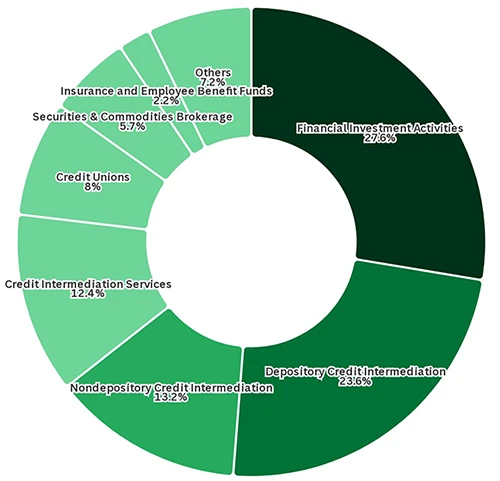
Image courtesy of Help Net Security
Key recommendations for Chief Information Security Officers (CISOs) include identifying all vendor relationships, assessing vendor security postures regularly, and monitoring vendor risk over time. By focusing on third-party risk management, financial institutions can enhance their defenses against potential breaches.
For more detailed insight, see the full report from Help Net Security.
The Evolving Threat Landscape
Cyber threats targeting supply chains are increasingly sophisticated. Ransomware attacks have become more focused, with attackers targeting logistics providers and manufacturers. For instance, the 2024 ransomware attack on Change Healthcare compromised 6TB of patient data, highlighting the vulnerabilities in the healthcare supply chain. Attackers are exploiting weak multi-factor authentication (MFA) and leveraging third-party credential theft to infiltrate networks.
Emerging threats in supply chains include software supply chain attacks, where cybercriminals inject malicious code into applications. Additionally, artificial intelligence is being used to automate attacks, making them more difficult to detect. Internet of Things (IoT) devices are also under threat, as many lack robust security measures.
For further reading, refer to The Hacker News.
Strategies for Supply Chain Protection
Organizations must adapt to the evolving cybersecurity landscape by implementing proactive security strategies. Continuous Threat Exposure Management (CTEM) frameworks can help identify and mitigate security gaps within supply chains. Regular penetration testing and External Attack Surface Management (EASM) tools are critical for uncovering vulnerabilities.
Compliance with regulations such as NIST and the Cybersecurity and Infrastructure Security Agency (CISA) guidelines is essential for maintaining a secure environment. Additionally, adopting AI-driven threat detection can enhance the ability to identify and respond to vulnerabilities.
For a deeper look into effective strategies, visit ProWriters.
Impact of Regulatory Changes
The introduction of new U.S. tariffs on technology and hardware could heighten cybersecurity risks within supply chains. Rising costs may force businesses to seek alternative suppliers that may not meet stringent security standards. This shift could lead to increased vulnerabilities and potential cyber espionage attempts.
Organizations must remain vigilant against the implications of these tariffs, ensuring that their vendors adhere to robust cybersecurity practices. Regular assessments and audits of third-party vendors are crucial in mitigating these risks.
Explore more on the implications of tariffs at Reuters.
Third-Party Cyber Risk Management
Understanding and managing third-party cyber risk is vital for organizations that rely heavily on vendors. Continuous monitoring technologies offer real-time insights into vendor security postures, allowing organizations to act swiftly when vulnerabilities arise. The majority of data breaches originate with vendors, necessitating a proactive approach to risk management.
Tools like Bitsight for Third-Party Risk Management enable organizations to continuously monitor vendor security, ensuring adherence to cybersecurity best practices. This approach allows for tailored assessments and prioritization of resources based on vendor criticality.
For a comprehensive overview of third-party cyber risk, refer to Bitsight.
To explore our services and enhance your cybersecurity posture, visit Gopher Security.

