Detecting Multi-Stage Attacks: Insights, Analysis, and News
Multi-Stage Cyber Attacks: Detection and Defense Strategies

Image courtesy of Splunk
Cybercriminals utilize multi-stage attacks, employing coordinated steps to infiltrate IT networks. These attacks typically involve identifying and exploiting vulnerabilities, escalating access privileges, and exfiltrating sensitive information. Understanding the stages of these attacks is essential for effective detection and defense.
Stage 1: Reconnaissance
The reconnaissance stage involves gathering intelligence about the target network. Attackers may perform network scanning or leverage open-source intelligence. Tools like network protocol analyzers and threat intelligence tools can help detect suspicious activities during this phase. Monitoring solutions such as Web Application Firewalls can track unusual traffic patterns.
Relevant links:
Stage 2: Initial Access
Using the information gathered from reconnaissance, attackers seek vulnerable entry points. This may involve exploiting outdated firmware or tricking unsuspecting users into downloading malicious payloads, often through social engineering tactics. Email filtering and endpoint protection tools are crucial for detecting unauthorized access attempts.
Relevant links:
Stage 3: Persistence
After gaining initial access, attackers aim to maintain their foothold within the network by installing malicious payloads. Behavioral analysis and endpoint monitoring tools can help detect unauthorized changes and abnormal access patterns.
Relevant links:
Stage 4: Lateral Movement
Attackers seek to compromise multiple systems by moving laterally within the network. Intrusion Detection Systems (IDS) can identify unusual traffic patterns indicative of lateral movement, helping to mitigate further breaches.
Relevant links:
Stage 5: Privilege Escalation
Privilege escalation allows attackers to access higher-level accounts typically held by key personnel. Continuous monitoring and identity access controls help to detect activities that may indicate privilege escalation attempts.
Relevant links:
Stage 6: Data Exfiltration
In the final stage, attackers exfiltrate sensitive data, often employing data loss prevention solutions and network traffic analysis to detect unauthorized data transfers. Any unexpected data access should trigger an immediate response.
Relevant links:
Latest Multi-Stage Attack Scenarios
Multi-stage cyber attacks can also take advantage of embedded content in documents, such as malicious links hidden in PDFs or Word files. Attackers may employ QR codes, which direct users to phishing sites when scanned. Tools like ANY.RUN Sandbox provide a safe environment to analyze these threats.
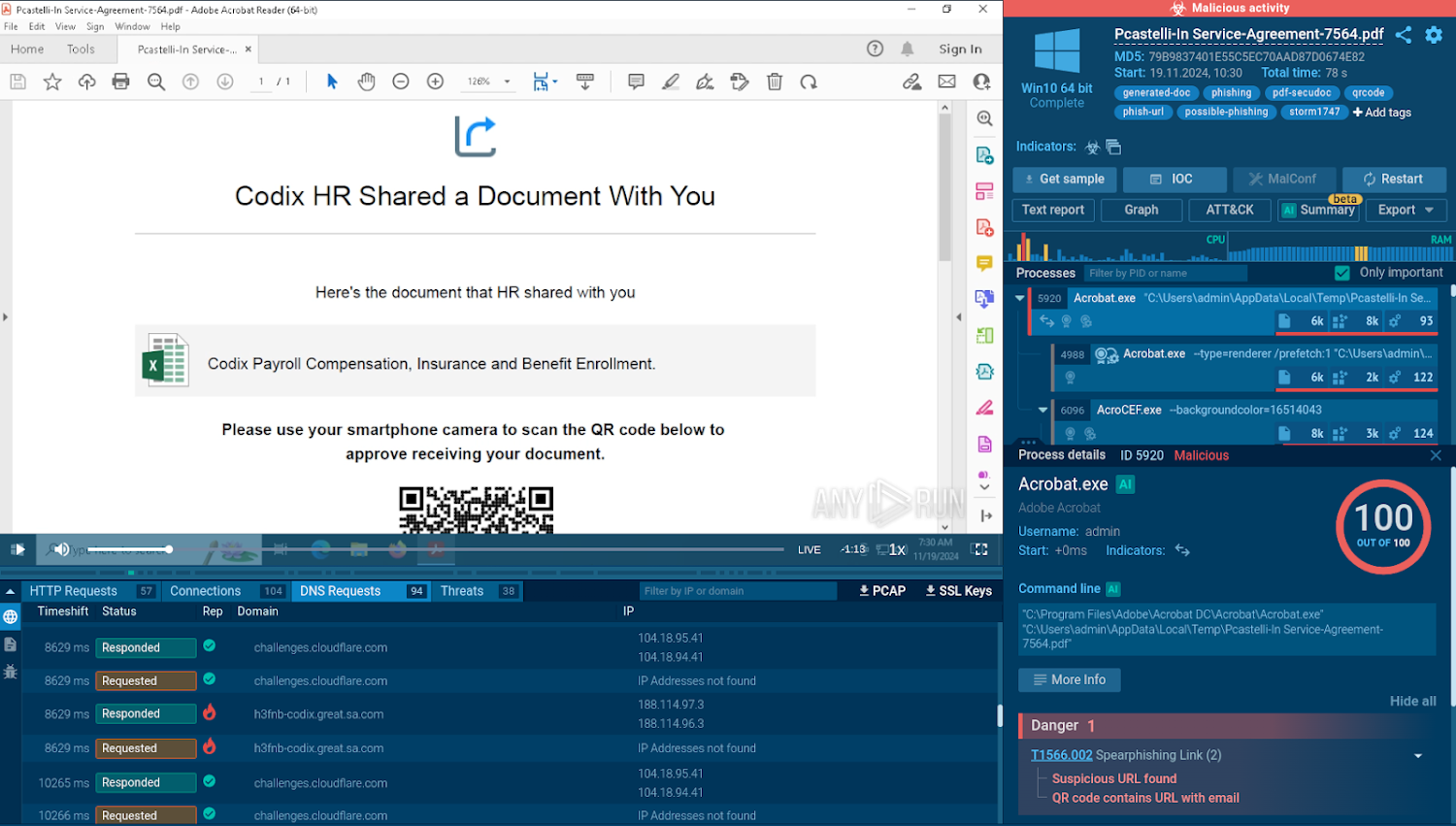
Image courtesy of ANY.RUN
URLs and Embedded Content
Attackers may hide malicious URLs in documents, leading unsuspecting users to phishing sites. ANY.RUN Sandbox allows users to safely interact with malicious files, analyzing how these attacks unfold.
Relevant links:
Multi-Stage Redirects
Multi-stage redirects can involve sequences of URLs that mislead users through trusted domains before reaching malicious sites. These tactics complicate detection, as they often employ CAPTCHA challenges to hinder automated defenses.
Relevant links:
Email Attachments
Email attachments remain a prevalent vector for multi-stage attacks. Modern attackers often use archives to conceal malicious payloads, increasing trust in the files.
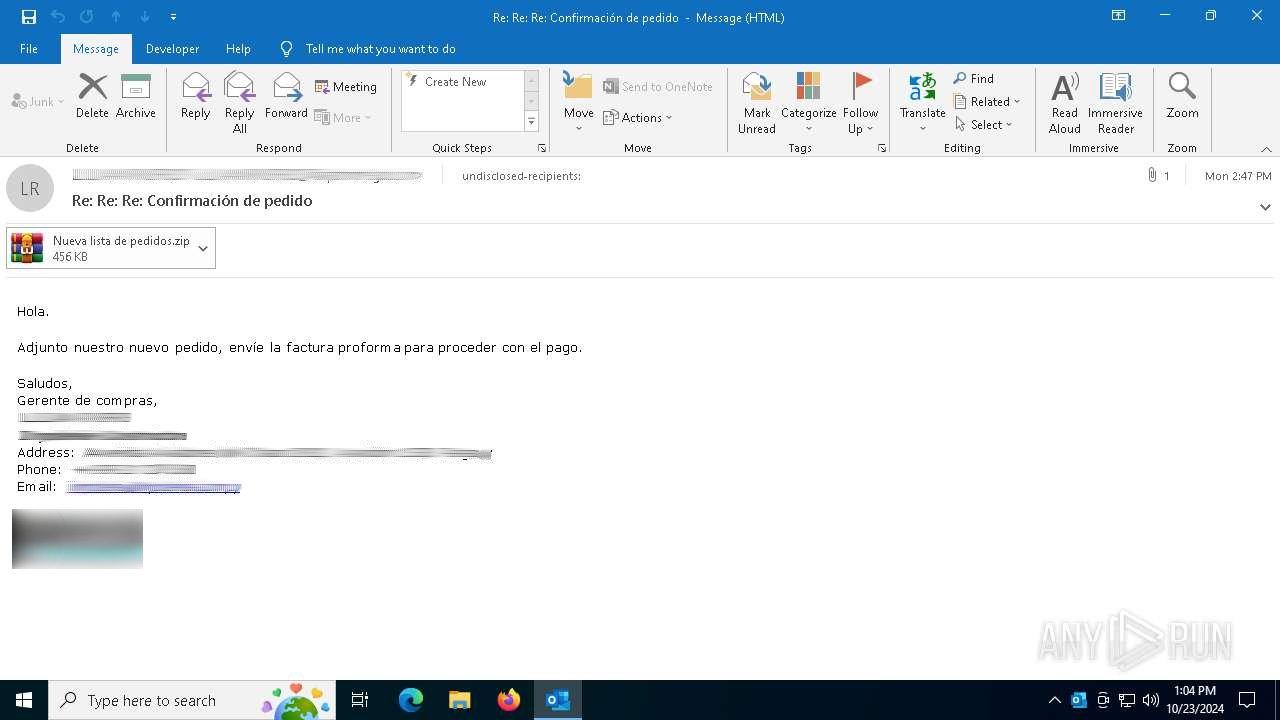
Image courtesy of ANY.RUN
By analyzing these attack scenarios with the right tools, such as ANY.RUN, organizations can improve their defenses against multi-stage cyber threats.
Explore our services at Company Name to enhance your security posture and stay ahead of cyber threats.

