Critical Vulnerability Found in WordPress Malware Scanner Plugin
WordPress Malware Scanner Plugin Contains Vulnerability
The Malcure Malware Scanner plugin has been identified with a high-severity vulnerability rated at 8.1 by Wordfence. This plugin, which is installed on over 10,000 WordPress websites, is susceptible to “Arbitrary File Deletion” due to a missing capability check on the wpmr_delete_file() function. Although an authenticated attacker requires only subscriber-level access to exploit this vulnerability, it poses significant risks.

Image courtesy of Search Engine Journal
According to Wordfence, “This makes it possible for authenticated attackers, with Subscriber-level access and above, to delete arbitrary files making remote code execution possible. This is only exploitable when advanced mode is enabled on the site.” There is currently no patch available, and users are advised to uninstall the plugin to mitigate risk.
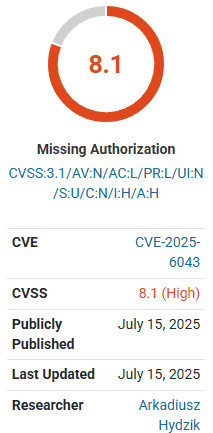
Image courtesy of Search Engine Journal
The plugin is temporarily unavailable for download as it is under review due to this critical vulnerability.
Additional WordPress Vulnerabilities
Another notable vulnerability is associated with the Malware Scanner WordPress plugin before version 4.5.2, where it fails to sanitize and escape some of its settings. This leads to Cross-Site Scripting (XSS) attacks when unfiltered_html is disallowed, particularly in multisite setups.
Severity and References
- CVE-2022-1995: CVE-2022-1995
- WPScan Vulnerability: WPScan Vulnerability
CVSS Score
- Overall Score: 4.8 / 10
- Attack Vector: Network
- Privileges Required: High
Best Practices for WordPress Vulnerability Scanners
Utilizing a WordPress vulnerability scanner is essential for maintaining site security. These tools alert users to known vulnerabilities in the WordPress core, plugins, or themes. It is crucial to regularly update vulnerable plugins and themes to avoid potential security breaches.
Recommended Scanners
- MalCare
- Test results: Great
- Price: Free
- Detects a wide range of vulnerabilities, including SQL injection and XSS.
- More information can be found at MalCare.
- Patchstack
- Test results: Great
- Price: Free
- Flags vulnerabilities and provides guidance on severity.
- WPScan
- Test results: Great
- Price: Free for 25 scans a day.
- One of the most comprehensive vulnerability scanners available.
- Wordfence
- Test results: Very Good
- Price: Free
- A popular security plugin that flags vulnerabilities effectively.
- Defender
- Test results: Average
- Price: Free
- Provides a good overview of vulnerabilities but may miss some obscure ones.
- Sucuri
- Test results: Bad
- Price: Free
- Limited vulnerability detection; primarily offers a list of available updates.
For a detailed comparison of various WordPress vulnerability scanners, including their test results, features, and pricing, visit MalCare.
Handling Detected Vulnerabilities
When a vulnerability is flagged, it is crucial to act quickly. Users should update their site, particularly if the issue is with a smaller plugin or theme. For larger plugins, testing updates in a staging environment is advisable to prevent disruptions on the live site.
For further assistance with website security and to explore comprehensive protection solutions, consider visiting Gopher Security.

