Broken Bow Public Schools Loses $1.8M in Phishing Scam
$1.8 Million Stolen From Broken Bow Public Schools in Phishing Scam
A significant cybersecurity breach occurred at Broken Bow Public Schools in Nebraska, leading to a loss of $1.8 million due to a phishing scam. The incident involved a fraudulent Automated Clearing House (ACH) transfer linked to an ongoing construction project.

Image courtesy of Troy Point
The school district received a sophisticated phishing email containing false payment instructions that appeared to be from a trusted vendor. As a result, the payment meant for a contractor was mistakenly sent to a fraudulent account. The district stated they had taken immediate action, launching a full investigation and collaborating with various authorities, including the Federal Bureau of Investigation, Nebraska State Patrol, and U.S. Secret Service.
Despite the setback, Broken Bow Public Schools has successfully recovered nearly $700,000 of the stolen funds through ongoing investigations and insurance claims. The district has assured the community that the construction project will continue without interruption and emphasized there would be no tax increases to cover the financial shortfall.
To prevent similar occurrences in the future, new protocols and safeguards regarding ACH transfers and financial transactions have been implemented within the district office. As the district noted in their statement, “We are committed to keeping our community informed and to taking every possible step to safeguard public funds.”
For more details, refer to the original news release.
How the Phishing Scam Unfolded
The phishing attack was characterized as a business email compromise (BEC) incident, where scammers sent a fake invoice that mimicked communication from a legitimate construction vendor. This highlights the sophisticated nature of these cybercrimes, as the fraudsters had clearly researched the school's ongoing construction project.

Image courtesy of Troy Point
The phishing email included detailed information that made it appear authentic, effectively deceiving school officials into authorizing the ACH transfer. This type of scam is prevalent, particularly targeting organizations during significant financial transactions, as corroborated by the FBI’s Internet Crime Report, which noted over 190,000 phishing complaints in 2024 with total losses exceeding $70 million.
Response and Recovery Efforts
Upon realizing the scam, Broken Bow Public Schools acted swiftly by contacting federal authorities. The collaboration with law enforcement has been crucial in recovering a portion of the lost funds, with the district actively working through its insurance provider to reclaim the remaining amount.
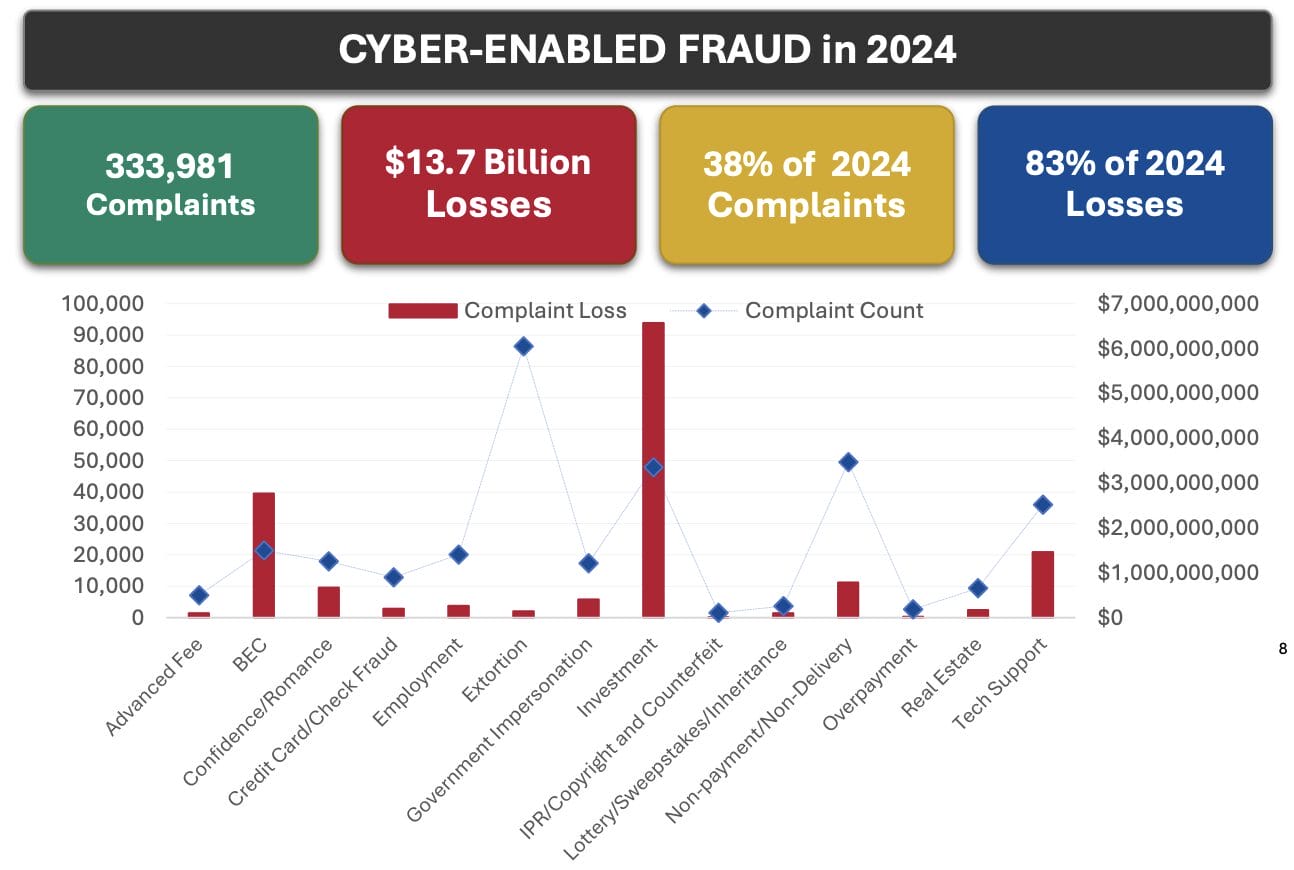
Image courtesy of Troy Point
The district has reassured stakeholders that the financial position remains strong, thanks to careful planning and budgeting. The construction project is set to continue as planned, with no disruption expected.
In light of this incident, it is imperative for organizations to adopt robust cybersecurity measures to protect against such threats. Simple verifications, such as direct communication with vendors before processing payments, can significantly mitigate risks.
For additional insights, visit the Nebraska Public Media coverage.
Potential customers are encouraged to explore our services at Gopher Security or contact us for more information on how we can help safeguard your organization against similar cybersecurity threats.

