Beware: Banking Trojan Uses Maintenance to Conceal Malicious Acts
Anatsa Banking Trojan
The Anatsa banking trojan has resurfaced, using a malicious app disguised as a PDF viewer to infect Android users. Over 50,000 users have unknowingly installed this dangerous malware, which targets banking applications. It has been reported by BleepingComputer that this trojan is capable of draining bank accounts through overlay attacks, where users think they are logging into legitimate banking apps while they are actually providing their credentials to attackers.

Image courtesy of Tom's Guide
Security researchers from Threat Fabric have tracked Anatsa for years, noting that it often hides in popular apps and utilities. The trojan can impersonate various banks, including JP Morgan, Capital One, and TD Bank, making it particularly dangerous.
To protect against Anatsa and similar threats, users are advised to stay vigilant and only download apps from trusted sources. For more information on how to safeguard your Android device, visit Tom's Guide.
Trojan-Banker.Win32.ClipBanker
Trojan-Banker.Win32.ClipBanker is a type of malware specifically designed to steal user account information related to online banking and e-payment systems. It operates on the Win32 platform, which is widely used in Windows operating systems. This malware transmits stolen data to the attacker using various methods, including email and FTP.
The tactics and techniques used by this trojan include:
- Execution: Utilizing the Windows Task Scheduler and the 'at' utility for executing malicious code.
- Persistence: Abusing scheduled tasks to maintain access to compromised systems.
- Credential Access: Attempting to access sensitive information stored in memory and private keys.
For detailed analysis and examples of this malware, refer to Kaspersky Threats and MITRE ATT&CK.
Online Banking Threats
Malware targeting online banking systems has been a significant issue for financial organizations. The emergence of various banking trojans highlights the methods cybercriminals employ to steal sensitive data. A notable example includes the Gumblar attack, which exploited vulnerabilities in websites to distribute malware.
Image courtesy of Securelist
The Gumblar attack method has become a preferred distribution system for numerous malicious programs, as seen in the monitoring of infected websites. One such malware variant, Trojan-Banker.Win32.Fibbit.a, utilizes a technique where it pretends that the banking website is undergoing maintenance, thus concealing its theft of credentials and funds.
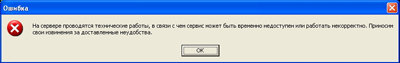
Image courtesy of Securelist
For further reading on online banking threats, see the reports on Krebs on Security and Securelist. Recommendations for mitigating these threats include using trusted software sources, employing up-to-date security measures, and ensuring safe online practices.

