Belk Data Breach: DragonForce Claims 150GB Theft, Legal Fallout
Belk Cyberattack Overview

Image courtesy of Security Affairs
Ransomware group DragonForce claimed responsibility for the cyberattack on Belk, a U.S. department store chain, which occurred between May 7 and May 11, 2025. The group reported that they stole 156 gigabytes of data during this incident. Belk's internal notification states, “Specifically, Belk was the victim of a cyber incident in which an unauthorized third party gained access to certain corporate systems and data between May 7-11, 2025.”
Belk is actively investigating the breach with third-party cybersecurity experts and has engaged law enforcement. The company restricted network access, reset passwords, and rebuilt affected systems in response to the attack. Data compromised includes personal information such as names and Social Security numbers.
Further details on the breach can be found from the following sources:
Data Breach Impact
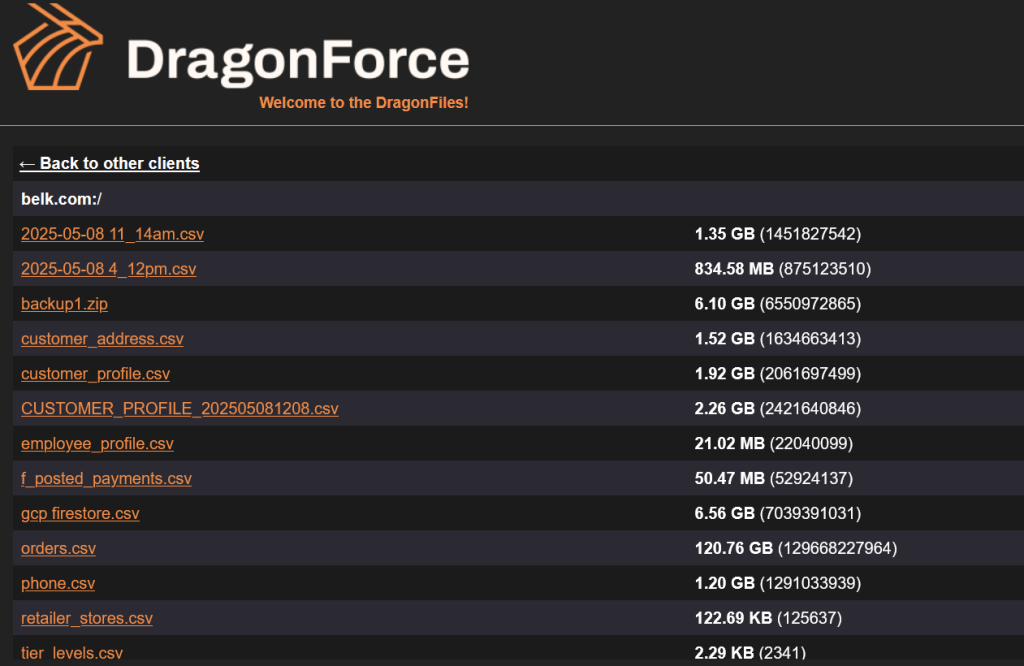
Image courtesy of Security Affairs
As reported, the breach has affected at least 586 individuals, compromising sensitive information. Belk has offered 12 months of free credit monitoring and identity restoration services to those impacted. The attack disrupted both online and in-store operations, leading to significant operational challenges.
Belk's response included working with cybersecurity experts to ascertain the breach's scope and initiating remedial actions. The company has not disclosed whether a ransom was paid to DragonForce, who is known for extorting victims for both data access and non-disclosure of stolen information.
For additional context on the attack, refer to:
- Cybersecurity Dive on Belk data breach
- Comparitech on DragonForce's claims
- Sophos research on ransomware evolution
Class Action Lawsuits
Belk is facing class action lawsuits in North Carolina, alleging that the company failed to adequately protect the personal information of its employees and customers. These lawsuits claim that the breach was concealed and that Belk did not take necessary steps to safeguard sensitive data.
For further legal developments, see:
DragonForce has been linked to other high-profile attacks on retailers, including Marks & Spencer and Harrods, indicating a trend of increasing cyber threats to the retail sector. This attack is part of a broader pattern, where DragonForce operates a Ransomware-as-a-Service model, allowing affiliates to utilize their tools for cyberattacks.
For more insights into ongoing cybersecurity threats, check:
- Cybersecurity Dive on retail attacks
- Comparitech's report on US retailer ransomware
Explore our services to ensure robust cybersecurity measures for your business. Visit our website for more information.

