Authorities Dismantle DiskStation Ransomware Gang Targeting NAS
Police Disrupt “Diskstation” Ransomware Gang Attacking NAS Devices

Image courtesy of TechRadar
A 44-year-old Romanian national has been arrested during a law enforcement operation to dismantle a ransomware campaign known as “Diskstation.” This group primarily targets Synology Network-Attached Storage (NAS) devices, which are essential for centralized file storage and sharing, data backup and recovery, and general content hosting. Since its inception in 2021, Diskstation has operated under various aliases, including DiskStation Security, Quick Security, LegendaryDisk Security, 7even Security, and Umbrella Security.
Police received multiple complaints from companies in Lombardy that suffered data encryption and were unable to operate without paying a ransom for decryption keys. The attacks have targeted organizations across sectors, including film production and civil rights protection, causing significant operational disruptions.
Operation Elicius

Image courtesy of BleepingComputer
Operation Elicius, coordinated by Europol, involved extensive forensic analysis of encrypted devices and blockchain tracking to identify ransom payments made in cryptocurrency. Investigations led to multiple raids in Romania, where several suspects were apprehended, including one caught in the act. The primary suspect, now in custody, faces charges of abusive access to computer systems and extortion.
Victims reported ransom demands ranging from $10,000 to hundreds of thousands of dollars. The investigation highlighted vulnerabilities in internet-exposed NAS devices, emphasizing the critical need for enhanced security measures.
Ransomware Attacks on Synology Devices
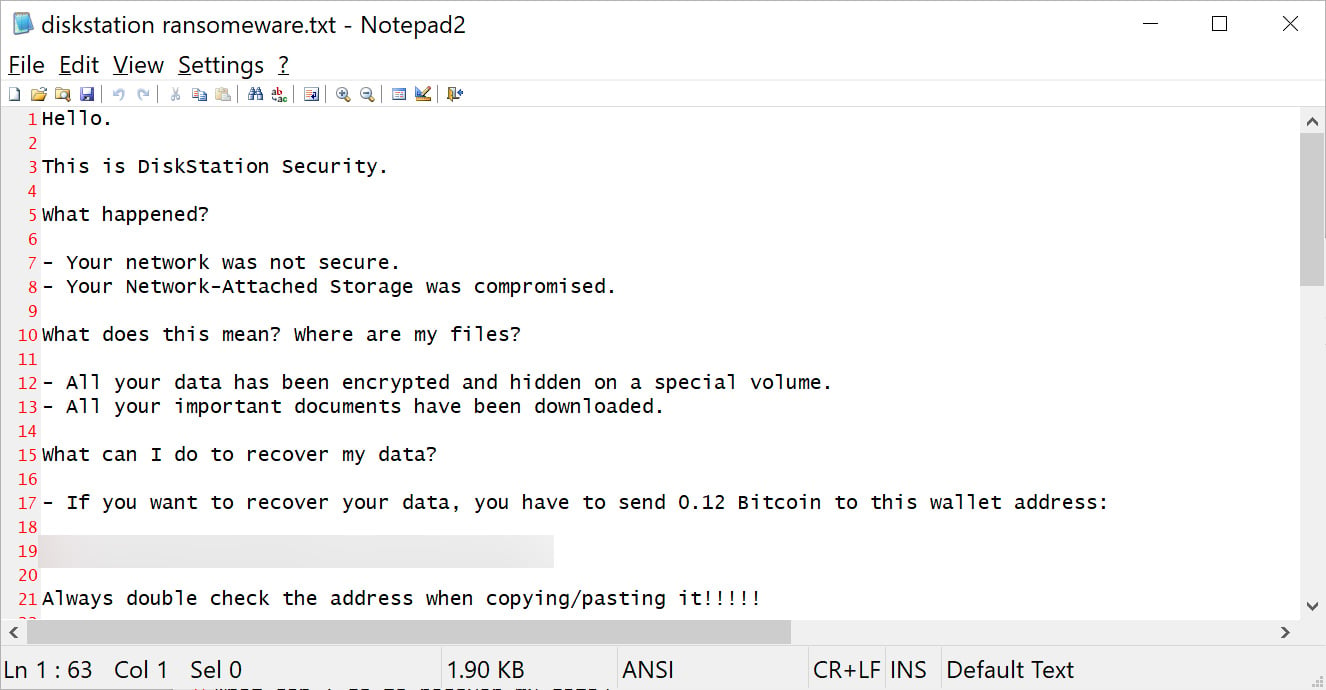
Image courtesy of BleepingComputer
Companies affected by Diskstation experienced severe outages due to the encryption of their data, which halted production processes. The victims included graphic design firms, film production companies, and international NGOs. To regain access to their data, victims were forced to pay substantial ransoms in cryptocurrency to the attackers.
Law enforcement agencies utilized digital forensics and blockchain analysis to trace the criminal network, demonstrating the effectiveness of a multi-pronged investigative approach. The use of advanced malware detection techniques helped uncover the methods employed by the cybercriminals.
Protecting NAS Devices from Ransomware
In light of the attacks, it is crucial for organizations using NAS devices to implement stringent security measures. Recommendations include ensuring devices operate on the latest firmware, disabling unnecessary services, and minimizing internet exposure.
Synology has provided guidelines to protect NAS devices from ransomware, advising users to enhance password security and regular data backups. Furthermore, enabling two-step verification and disabling remote services can significantly reduce risks.
Organizations can benefit from Gopher Security’s AI-Powered Zero Trust Platform, which offers comprehensive security solutions to protect devices from ransomware attacks. This includes micro-segmentation for secure environments, granular access control, and secure access service edge (SASE) capabilities.

Image courtesy of Cybersecurity News
Conclusion
Through international cooperation, law enforcement has successfully disrupted the Diskstation ransomware gang, underscoring the importance of robust cybersecurity measures. Organizations are encouraged to bolster their defenses against ransomware threats by leveraging advanced security solutions.
For organizations looking to enhance their cybersecurity posture and protect against ransomware attacks, Gopher Security offers innovative security solutions tailored to meet the needs of businesses across various sectors. Explore our services or contact us to learn more about how we can help secure your digital assets. Visit us at Gopher Security.

