Android Malware Konfety Uses Malformed APKs to Evade Detection

Image courtesy of Zimperium
A new variant of the Konfety Android malware employs a malformed ZIP structure along with various obfuscation techniques to avoid detection and analysis. This malware masquerades as legitimate applications that mimic popular products available on the Google Play Store, although it fails to deliver the promised functionality.
The malware's capabilities include redirecting users to malicious sites, installing unwanted applications, and generating fake browser notifications. Instead of providing genuine services, it uses the CaramelAds SDK to serve hidden advertisements while exfiltrating sensitive data such as installed apps, network configuration, and system information.
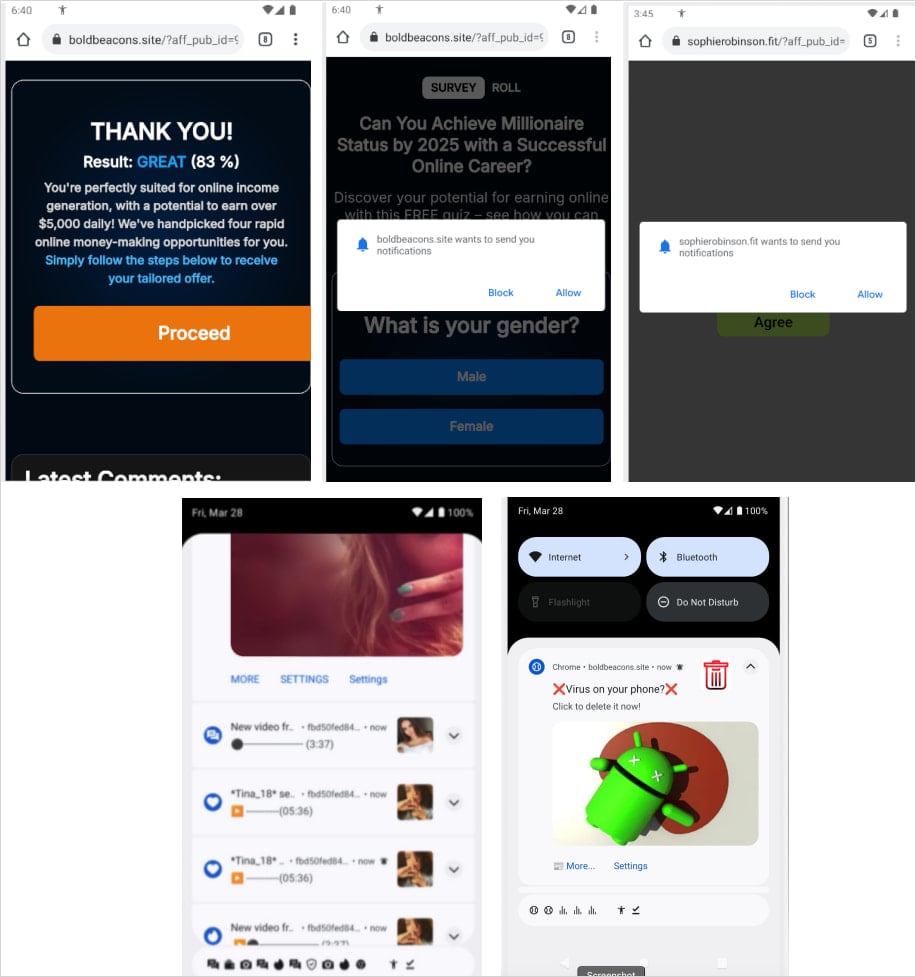
Image courtesy of Zimperium
Despite not being classified as spyware or a RAT, Konfety includes an encrypted secondary DEX file within the APK. This file is decrypted and executed at runtime, enabling hidden services defined in the AndroidManifest file and allowing for the delivery of more dangerous capabilities post-infection.
Evasion Tactics
Researchers at mobile security platform Zimperium identified that Konfety utilizes multiple methods to obscure its true nature and activities. The malware tricks users into installation by imitating legitimate app names and branding, distributing through third-party stores. This tactic is known as the "evil twin" or "decoy twin" method, as described by researchers at Human Security.
The operators promote Konfety on third-party app stores, targeting users who seek free versions of premium apps while avoiding Google tracking. The dynamic loading of code and manipulation of APK files are significant evasion strategies that hinder static analysis and reverse engineering tools.
The malware sets the General Purpose Bit Flag to 'bit 0', indicating encryption, even when it is not. This misleads analysis tools, prompting false password requests that block access to the APK's contents. Moreover, critical files are declared using BZIP compression, which is unsupported by analysis tools like APKTool and JADX, resulting in parsing failures.
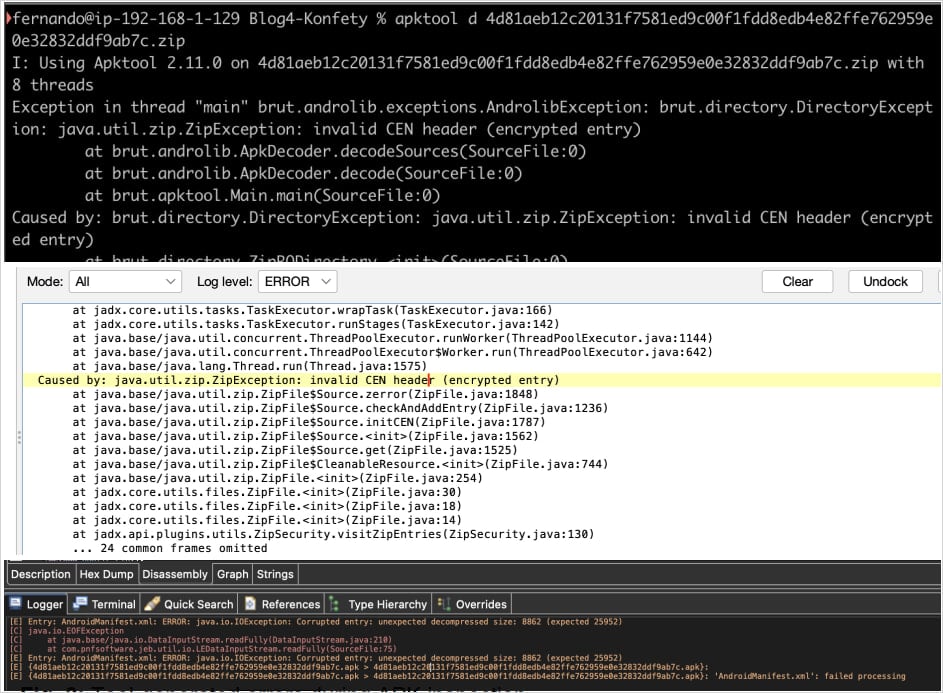
Image courtesy of Zimperium
Android defaults to its processing methods, allowing the malicious app to install and execute without issues. Once installed, Konfety hides its app icon and name, adapting its behavior based on the victim's location through geofencing.
CaramelAds SDK Abuse
The Konfety operation exploits the CaramelAds SDK, a mobile advertising tool, to facilitate its ad fraud activities. Satori researchers discovered that over 250 apps on the Google Play Store are linked to Konfety, each having an evil twin distributed outside official marketplaces. These evil twin apps utilize a modified version of the CaramelAds SDK to conduct fraudulent activities.
The SDK, while not inherently malicious, can be abused for ad rendering and sideloading additional APKs. The Satori Threat Intelligence Team noted that the peak volume of Konfety-related traffic reached 10 billion requests daily.
Image courtesy of Human Security
Konfety's evil twin apps mimic their corresponding decoy twins by copying package names and publisher IDs. These apps are typically spread through malvertising campaigns targeting users seeking modified applications.
Unsupported Compression Methods
Researchers at Zimperium have identified 3,300 samples of Android malware utilizing unsupported compression methods to bypass detection. The technique involves tampering with the compression method field in APKs, which can hinder analysis and decompilation by common tools.
Older versions of Android handle APK compression differently, making it possible for unsupported methods to be installed on versions above Android 9. Many analysis tools fail to process these samples, leading to a reduced likelihood of detection and analysis.
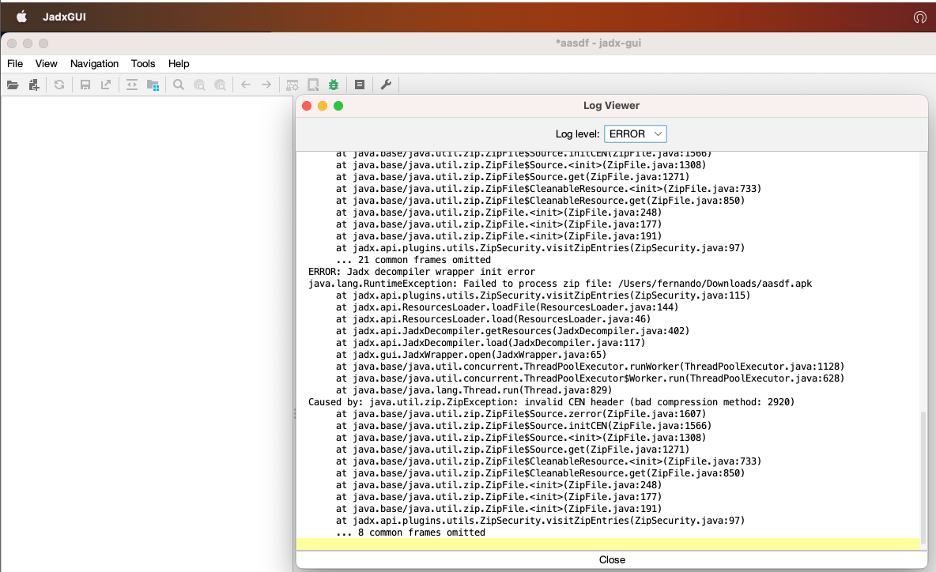
Image courtesy of Zimperium
The exploitation of these methodologies raises significant challenges for malware detection, as many antivirus engines do not adequately scan APKs with unsupported compression formats, allowing malicious applications to be installed unnoticed.
Recommendations for Users
To protect against threats like Konfety and other forms of Android malware, users should avoid sideloading apps from third-party stores. It is crucial to only download applications from trusted sources to minimize risk. Enabling Google Play Protect can add an additional layer of security by scanning for malware in existing and newly downloaded apps.
Furthermore, users should consider employing reliable antivirus solutions alongside Google Play Protect to enhance their defenses against malware threats.
For more insights on securing your Android device, consider exploring our services at undefined for comprehensive protection solutions against malware and other cyber threats.

