Advanced BEC Campaign Targets Microsoft 365 with MFA Circumvention
Advisory: Persistent MFA Circumvention in an Advanced BEC Campaign on Microsoft 365 Targets
Mitiga has identified a sophisticated Business Email Compromise (BEC) campaign targeting Microsoft 365 organizations. The attack exploits weaknesses in Microsoft 365's multi-factor authentication (MFA), Microsoft Authenticator, and Microsoft 365 Identity Protection, effectively nullifying the security that MFA is supposed to provide.
Background
The attempted BEC attack revealed that the attacker had access to sensitive information that could only have been obtained by compromising a user in the organization. Mitiga reported unauthorized access to an executive’s Microsoft 365 account from multiple locations, including Singapore, Dubai, and San Jose, California. The initial access was gained through an adversary-in-the-middle phishing technique.
Microsoft 365 MFA Weaknesses Analysis
Despite MFA being a critical control, Microsoft does not allow customers to configure enhanced controls that could improve security. For example, when accessing resources from a new IP address or requesting elevated permissions, Microsoft does not require a new MFA challenge if a session has previously been authorized with MFA. This lack of flexibility allows attackers to maintain access even after the initial compromise.
One surprising aspect is the Privileged Identity Management (PIM) feature, which allows users to elevate permissions without requiring an MFA re-challenge. This means that if an account is compromised, attackers can become administrators easily. Furthermore, attackers can add a new Authenticator app without an MFA re-challenge, which creates persistency in accessing the account.
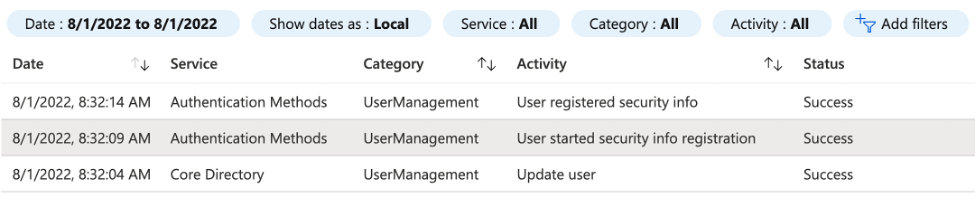
Image courtesy of Mitiga
Recommendations
To mitigate these risks, organizations should implement additional security layers, such as requiring a third factor tied to physical devices or authorized laptops and phones. Microsoft 365 offers Conditional Access, which can enhance security by requiring authentication via compliant devices.
Read a full analysis of the entire attack.
Phishing Campaign Targets Microsoft Device-Code Authentication Flows
A phishing campaign attributed to Russian state-sponsored hackers has been targeting various organizations globally since at least August 2024.

Image courtesy of Cybersecurity Dive
Device-Code Phishing Attacks
These attacks use a specific phishing technique to exploit device-code authentication flows. Attackers prompt applications to generate device codes and trick users into entering them into a legitimate sign-in portal. This allows the attackers to capture authentication tokens, which can then be used to access targeted accounts without needing passwords.
Microsoft Threat Intelligence has warned that the group known as Storm-2372 has intensified its phishing attacks by using the client ID for Microsoft Authentication Broker. This enables attackers to obtain refresh tokens and access organizational resources.
The phishing emails used in these campaigns do not contain malicious links or attachments, making them difficult to detect by cybersecurity products.
Read more about Storm-2372's activities.
Phishing Campaign Impersonates Booking.com
A new phishing campaign has emerged, impersonating Booking.com to deliver a suite of credential-stealing malware. This campaign is indicative of the ongoing threat of credential theft.
Credential Theft
Credential theft remains a significant concern for organizations, as attackers increasingly use sophisticated techniques to gain unauthorized access to sensitive information.
For more information on credential theft and protective measures, refer to the Microsoft Security Blog.
Explore how our company undefined can help enhance your security measures against these threats. Visit our website at undefined to learn more about our services.

